Some times back, I have tried to place before the readers of this blog who are mainly followers of Cyber Law, Information Security and Data Protection some thoughts on the impact of Quantum Computing on Cyber Laws through a series of articles. (indicated at the end of this article).
The essence of the discussions so far presented here is that Quantum Computing changes the way we process data today in classical computing.
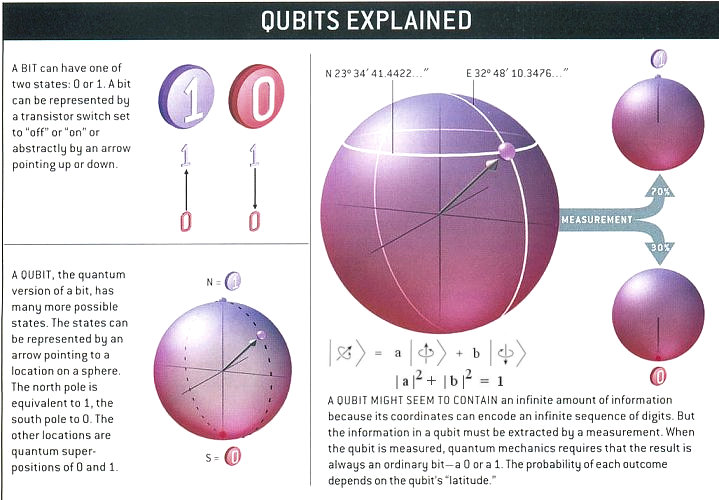
In Classical computing, a data holding element can assume the state of Zero or One and will be stable in that state unless it is changed. A combination of such data states read together is what we call as “Data” and give it a meaning as text, sound or picture etc.
In Quantum computing, the data holding element is not a miniaturized transistor or a charged area of a magnetic surface. Instead the data holding element is a sub atomic particle such as an electron or a nucleus. For the time being we shall simply call this as “Qubits” (Quantum bits). In Quantum computing, processing is carried out in an unstable Qubit state where a Qubits may exist in either a zero or one state and it’s state can only be measured in probabilistic terms.
For certain application, the probabilistic processing is good enough and in certain applications, the Qubits may have to be held in a stable state for a short period when processing happens in a near absolute zero temperature environment so that processing can proceed.
In the last article on this subject in this blog, I highlighted the research which one of my classmates is pursuing in US, on a new kind of sub atomic particles called “Majorana Fermions” which takes the thinking to a level even more minute than the electrons.
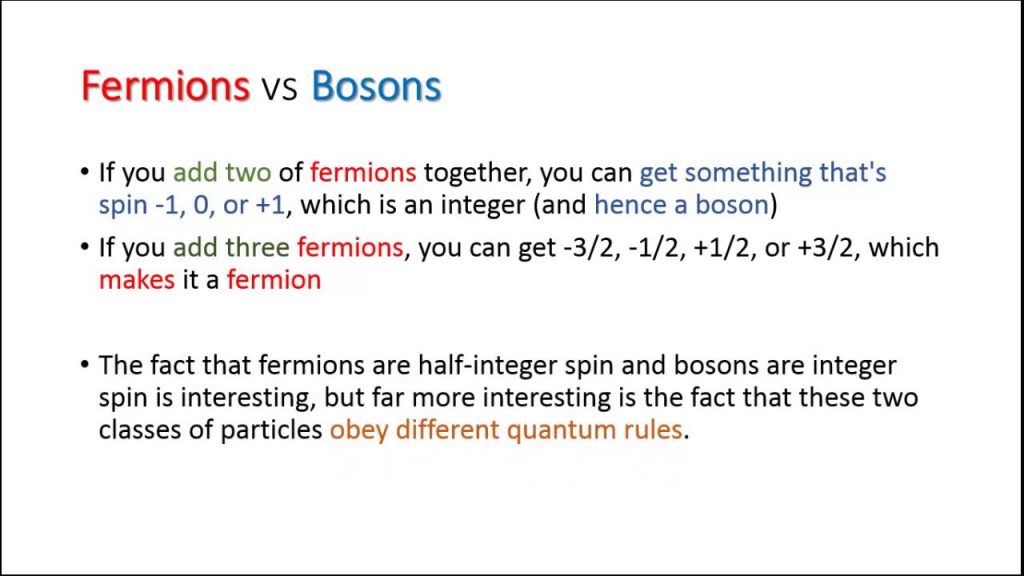
Fermions are a class of particles which have a spin state equal to half instead of zero or plus one or minus one. (If you are interested in Physics, explore here)
Majorana Fermions are a class of particles different from the common system of particles called Deric fermions. Deric fermions exist in two states “Particle” and “Anti Particle” with a positive and negative charge (Example Electron and positron). The Majorana Fermions are like the proverbial Ardha Nareeshwara and they are both particles and anti particles themselves. (Beyond this let us not confuse ourselves at this point of time).
These particles called Majorana Fermions whose existence has now been proved, are expected to be the building blocks of the new Qubits replacing the “Phosphorous Nuclei” which is being used now in construction of Quantum Computers. While the present versions of Qubits are now in the labs and expected to be commercially available in the year around 2030, the Qubits built with Majorana Fermions are expected to reach commercial exploitation beyond 2040.
There is no doubt that the issues raised by this development are issues of the future like the “Global Warming” etc..But in law, they will strike earlier because the “Uncertainty” of data states which these developments represent will render the evidentiary aspects of data suspect in the Courts of law.
Fortunately, the Indian system of admissibility of electronic evidence under Section 65B of Indian Evidence Act is constructed in such a way that electronic evidence created and processed out of the Quantum Computing system whether they are using Qubits created out of nucliei or Deric fermions or Majorana fermions.
Despite the practical difficulty of processing with Qubits, it enables computer processing to be done at a speed which makes all the current security related encryption vulnerable for brute force attacks. This is the biggest disruption that we may see to the classical computer system and the Information security technology. In simple words the use of crypto systems with RSA or ECC algorithms may no longer be considered as “reliable”.
All our security assumptions including the “Reasonable Security” that we consider as adequate legal obligation now needs to be revised now.
This document “Preparing Enterprises for the Quantum Computing Cyber Security Threats” from Cloud Security Allianceis an excellent reading material to understand the likely developments in this field. The document is so well written that it does not require any further explanation from my side.
I am aware that the developments discussed here are out of the normal orbit of a Cyber Law or an Information Security or a Data Security professional. It may also be more relevant beyond our life time and has been provided as a point of record here assuming that Naavi.org will survive beyond our life time. However I am bringing it up here so that young professionals in the age group of 25-30 who are working in the field of Cryptography can start looking at researching in this area so that by the time they turn 60, they will be global thinkers of repute and can take India ahead in cyber security to match the Chinese and US security specialists.
In particular, I invite our educational institutions such as Manasa Gangothri and more particularly the Physics department or the IISC to take the lead in initiating some research on building Qubits with the sub atomic particles so that we may not be lost out of the race to build the secure computers of the next generation.
Before I end, I want to reiterate that Cyber Laws and more particularly the Computer processing and Data are all concepts which have originated from the branch of science called “Physics” and people like the undersigned who graduated with a study of Physics and are now roaming the field of Law and Computer science can claim to be relevant in this domain as “Computer Science theoreticians”.
Naavi
Earlier articles:
Quantum Cmputing takes a step further: may 10, 2020
Quantum computing and Emerging Cyber Law Challenges… Are we ready? : March 10, 2018
Section 65B in the Quantum Computing Scenario: March 16, 2018
Theory of Dynamic Personal Data: March 31, 2018
In the wornderland of Quantum Cyber Law, Physics is part of the Law specialization: April 3, 2018
The Vast and Far Reaching Applications of Quantum Computing- June 20, 2018
China working on achieving Quantum Supremacy: July 5, 2018
China may be developing its own unbreakable encryption system through Quantum Computing: July 5 2018
Is it the beginning of the Chinese domination of the Globe?…Mr Modi to take note: July 5, 2018
10000 years=200 seconds in Sycamore Processor: October 24, 2019