Personal Data Protection regulation is presently a global phenomenon. While legislation like ITA 2000 try to protect “Data” in general(Section 43/66) with specific provisions for protecting “Personal Data” (Sec 72A) and “Sensitive Personal Data” (Section 43A), legislations like GDPR have focussed on Personal Data Protection only. India is set to follow the trend with its own Personal Data Protection Act in due course.
Indian companies today are eager to get themselves certified under various standards such as BS 10012 though these so called standards are nothing but a reiteration of GDPR articles in a slightly modified language.
It must be remembered that “Certification” under a certain standard is only an internal milestone for an organization to inform its stakeholders that they have indeed taken some formal steps towards compliance and is not an end in itself in the organization’s journey towards full compliance of data protection regulations..
BS 10012 is yet to formally align with the UK’s new Data Protection Act 2018 but still for the corporate managements, the tag “BS 10012 compliant” is a desirable asset for which they are willing to spare their budget. But for Indian Companies, BS 10012 may not be sufficient to be complaint with data protection regulation since Indian laws may have to be also understood and complied with.
Cyber Law College which is the academic organ of Naavi.org considers that there is a need to develop Personal Data Protection Standard for Indian Companies which goes beyond BS 100012 and be compliant not only for GDPR but also to ITA 2000/8 and the proposed PDPA.
Currently Naavi uses the Indian Information Security Framework with the following top line implementation charter which is identified as IISF309.
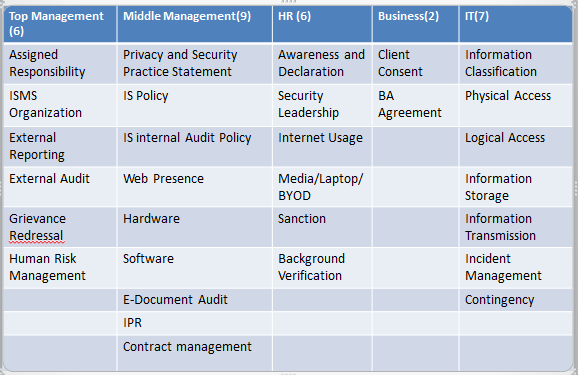
As one can observe, it captures most of the control requirements expected in an information security standard though the details may not be clear in the framework as presented above.
After the advent of PDPA 2018 in draft form, Naavi floated the idea of “Data Trust Score” as a measure of a “Data Audit” conducted under PDPA 2018. This was a measure of how good is the implementation of PDPA compliance in an organization.
The criteria suggested was a 5X5 matrix where 5 parameters namely
- Management Commitment
- Knowledge in the organization
- Controls
- Review mechanism
- Grievance Redressal mechanism
The evaluation was suggested on a scale of 0-100 in 5 steps of 20 each and hence it was called the 5X5 grid.
In order to further fine tune the approach and make it repeatable, Naavi is now working on developing a “Standard” which cover different requirements of compliance.
This “Standard” is presently the internal Audit Standard for Ujvala Consultants Pvt Ltd, the corporate entity of Naavi that addresses the audit requirements.
The standard is called “Personal Data Protection Standard of India” (PDPSI) and will be developed by Naavi.org as a part of its educational initiative of Cyber Law College.
The future idea is to make it an open standard which any intending corporate can adopt on their own.
Auditors are free to adopt it to their own audit framework if they feel like or ignore it if they donot feel it has any value, or adopt thoughts from this standard into their own audits.
The objective is to make an “Audit under PDPSI” incorporate principles of personal data protection imbibed in other standards including BS 10012 so that an organization which is PDPSI compliant is essentially also compliant with BS10012. It is understood that a Certification of compliance under PDPSI is not a certificate of compliance under BS 10012. However, an organization which is compliant under PDPSI should easily sail through any evaluation under BS10012.
However, we believe that “Compliance to a standard is required for a faithful protection of personal data as required under law and not just to sport a tag on which a blind faith can be placed”. Such blind faith often leads to complacency and needs to be avoided.
Conceptually therefore, PDPSI has been launched as the future of Naavi’s approach to Personal Data Protection approach and will be integrated with the DTS system which is already suggested.
The details of the standard under each of the above five parameters will be developed module by module and the standard will be published through this site.
Some may feel that by making such standards public, we will be losing an opportunity to commercialize it or we will be hurting other standards providers.
But we firmly believe that a “Suggested Standard” should be made available freely while commercial exploitation can be made through the implementation consultancy.
I trust at least a few of the data protection practitioners would accept this approach as what is required to make compliance to data protection laws affordable to most of the SMEs.
Any suggestions, comments etc are welcome.
This is also an open invitation to interested persons to join me in the development of PDPSI as a standard with wider acceptance in the community.
PDPSI first version will be referred to as PDPSI-0219, and hopefully it would get updated from time to time.
Await the publication of the different elements of PDPSI-0219 in due course.
Naavi







