[In continuation of the earlier article/s on PDPSI, we proceed to unravel the further details of the Personal Data Protection Standard of India (PDPSI). The objective of the standard is to make available a open source guideline to Indian Companies to comply with Privacy and Data Protection requirements that meet the standards of BS10012, GDPR as well as the Indian laws such as ITA 2000/8 and the proposed PDPA 2018.]
The compliance of Privacy Protection regulation whether under PDPA 2018 or GDPR or any other law normally starts with
a) Privacy Policy
b) Information Security Policy
The Privacy Policy declares the intentions of the organization in meeting the different requirements of the regulation. It is a comprehensive aggregation of several other sub policies that we will discuss here. It has to capture the objectives of the organization and reasonably describe how it proposes to implement the requirements.
Privacy Policy is for the organization to follow while “Privacy Notice” is meant for the information of those who interact with the company. “Privacy Notice” may contain many aspects of “Privacy Policy” but the objectives of the Policy are different from the Notice and this should reflect in the drafting of the two.
The Information Security Policy on the other hand is the policy that is intended to be followed within the organization to meet the Privacy Policy requirements.
Since a Corporate Information Security Policy has to protect both personal information and non-personal information, and the Privacy Policy is meant for Personal Information, the Information Security Policy should be broader to cover both Personal and Non Personal Information Protection.
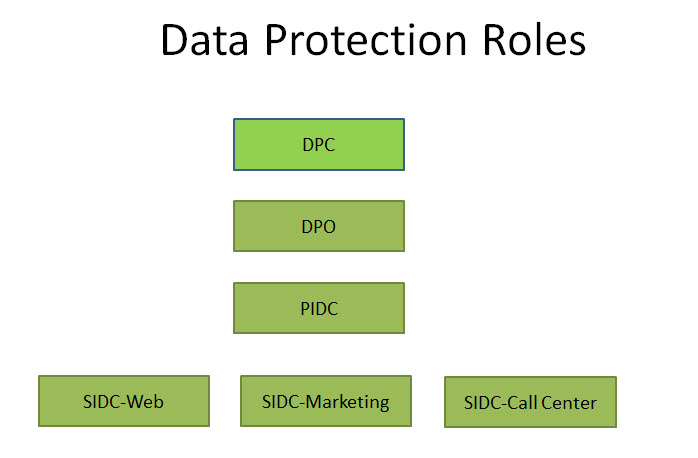
In a way, Information Security for Privacy Protection is a sub set of Information Security for the organization as a whole. If necessary, an organization may opt to develop a “Personal Data Protection Policy” (PDPP) which could be considered as a subset of the Information Security Policy and let a DPO/DPC manage the PDPP while the CISO handles the IS Policy of the organization.
While drafting Privacy Policy , one must remember that “Privacy Policy” meant for the website is not the comprehensive Privacy Policy for the organziation. Privacy Policy for the web only relates to the information collected from the website visitors. Once the website visitor opts for some service, the privacy policy relevant for the service will be relevant. In most cases the Privacy Policy for the website visitors can be simple since no personally identifiable information other than the technical details captured by the hosting system may be collected. What is relevant for compliance is more the policy applicable to the subscribers for different services who provide identifiable personal information.
We are reasonably familiar with the drafting of Privacy Policy and the IS policy. But what PDPSI expects is that an organization has a clear view of what is the “Legitimate Interest Policy” under which certain provisions of GDPR or PDPA are sought to be implemented with some customization and dilution where necessary using the clauses which provide “Exemptions”.
In order to ensure that an organization is not confronted with the charge of “Non Compliance” when may be required to override certain standard practices for the legitimate business interests of the organization or for reasons such as National Security, Public Interest, Journalistic requirements etc., it is recommended that a separate policy document is drafted to codify why the regulation may be either not followed or followed differently with some safeguards and under what circumstances.
Naavi normally starts with the Legitimate Interest Policy before drafting the Privacy Policy and tries to get the Legitimate Interest Policy dovetailed to the business context. If any recommended aspect of the legitimate interest policy is considered as a serious violation of the Privacy law, then the legitimate interest policy may have to be suitably modified with the consent of the management.
Not having a “Legitimate Interest Policy” would make the life of the DPO difficult since he would confront powerful business executives trying to bypass the privacy policies and justifying it in business interests while the resulting consequences of non compliance becomes the responsibility of the DPO. By having a separate Legitimate Interest Policy (LIP), the DPO knows exactly what he can do and what he cannot do.
[To Be Continued… Comments welcome]
Naavi
Other Reference Articles
- A Step beyond BS10012 and GDPR-Personal Data Protection Standard of India-PDPSI
- Data Protection Standard of India- (DPSI)
- Data Classification is the first and most important element of PDPSI
- Why 16 types of Data are indicated in PDPSI?
- Implementation Responsibility under Personal Data Protection Standard of India
- India to be the hub of International Personal Data Processing…. objective of PDPSI
- Principles of PDPSI
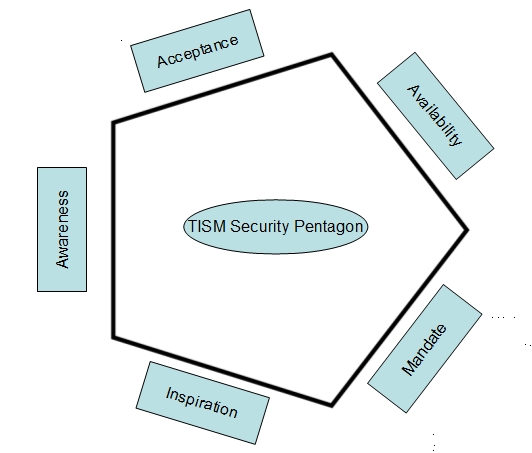
- Pentagon Model of TISM…An implementation approach to PDPSI implementation
- Personal Data Gate Keepers and Internal Data Controllers in Organizations
- Naavi’s Data Trust Score model unleashed in the new year
- Naavi’s 5X5 Data Trust Score System…. Some clarifications
- Naavi’s Data Trust Score Audit System…allocation of weightages