(Continued from the previous article)
P.S: This series of articles is an attempt to place some issues before the Government of India which promises to bring a new Data Protection Law that is futuristic, comprehensive and Perfect.
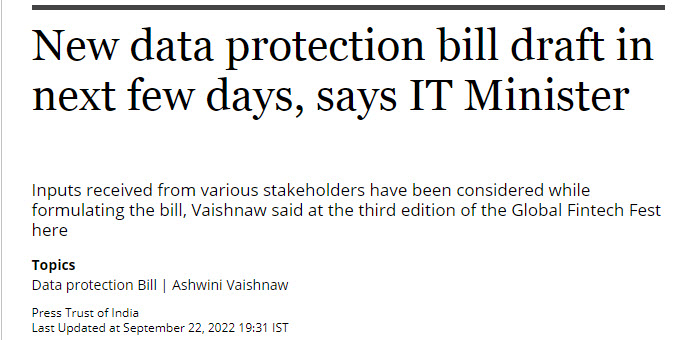
Reports emanating in the press indicate that the Government of India may come up with a new draft of data protection law sooner than earlier expected. According to the above report quoted in PTI on September 22, the bill may be presented in the “Next Few Days”.
We at FDPPI have already declared the focus of our IDPS 2022, a virtual summit to be eld on November 11,12 and 13 as “Shape of Things to Come” ready to discuss the new draft in as much depth as possible.
As a reference frame we have also been working on our own draft of what should be considered as an ideal law and we have been discussing this in the series of articles of which this is the 23rd.
Initially the Government was talking of a common law for both personal and non personal data and revision of ITA 2000 simultaneously with this new law. However, if the Government wants to release a draft for public comments immediately, then it is more likely that the draft will confine itself to personal data protection.
In such a scenario, there are two options before the Government. First is to pick the GDPR or the PDPB 2019 and cut and paste most of the provisions as is available and make some cosmetic changes to create the New Data Protection Act of India (NDPAI). The second approach would be to design the law as a zero based approach, forget GDPR and create a law afresh.
While the Government may take the easy path of using the existing GDPR and import it to the NDPAI so that there is easy acceptability of the industry, it would be an opportunity missed if we donot think of creating the law from basic principles.
Though we are aware that the probability of the Government adopting the second path which is more challenging and requires more conviction on the principles, we would continue to place some of our thoughts in this direction so that it goes on record that some thing was suggested even if it was not accepted.
Probably several years from now, some of these principles may become part of the regulations through amendments or through rules.
Since there is some urgency to place these thoughts in public domain before the Government commits itself to a draft of its own which becomes a rigid set of provisions difficult to change, we are providing here some key requirements of the law .
While there is plenty of scope for improvement of these suggestions, we need to start some where to know what can be changed and hence let us proceed further.
The basic aspects that the law has to cover is “Applicability”,” Rights of Data Principals” “Obligations of Data Fiduciaries”, “Prescribed penalties” and “Formation of a regulatory authority”.
Obligations of Data Fiduciaries would include compliance requirements and protection of Rights of data principals.
The details of whether the Data Fiduciary may be called the Data Controller or a Data Guardian etc is a matter of further details which we have tried to cover earlier and will be part of the detailed requirement.
In this article we are trying to take on record the “Rights” that a person needs to be guaranteed through this Act and how the declaration of Rights itself fixes the applicability.
The draft presented here is a “Rights Based Drafting of the Privacy and Data Protection Act” and does not follow the GDPR through cut and paste though all the requirements of GDPR may finally find a place in the Act in a different manner.
This draft revolves around the concepts of
a) Protected Right
b) Protected Data
c) Protected Person.
Protected Data refers to what other laws may call “Personal Data”. “Protected Person” refers to the “Data Principal or Data Subject” . Protected Right refers to the “Right to Privacy and the subordinated rights such as right to access, correction, etc).
The obligations to protect the right lies with the Government as well as every organization which has a duty under the constitution to protect the right.
How the obligations are to be discharged is the “Transparency and Accountability” or “Compliance aspects” covered in GDPR.
These form the real essence of the entire law though the Government draft is likely to focus on the “Regulator” and what would be his authority etc. Industry is also concerned about the detailing of the obligations including the cross border transfer and privacy activists will focus on how to criticise the powers of the Government, exemptions etc.
Our approach to construct the law from “Protected Right” is more basic in approach and is the Zero based approach.
In this approach therefore we will first indicate the core objective of the law by declaring the concept of “Protected Right” as follows.
Protected Right
(a) The right to privacy shall be a right that is protected through due process set by this Act as an intrinsic part of the right to life and personal liberty as envisaged under Article 21 and as a part of the freedoms guaranteed by Part III of the Constitution of India subject to reasonable exceptions under article 19(2) of the Constitution of India.
(b) Any data whether in oral, written or electronic form that is likely to have an impact on the Protected Right shall be construed as “Protected Data” and shall be collected, processed, generated, stored, or disclosed or otherwise used as per the provisions laid down in this Act.
(c) The “Right to Privacy” under this Act shall be applicable to the following category of “Protected Persons”
i. Living natural persons who is a recognized citizen of India irrespective of his place of residence
ii. Living natural persons who is a recognized citizen of a sovereign country recognized by India and under authorized residence in the territory of India
(d)Protection under this Act shall not be available to
-
-
-
- Natural persons who are under unauthorized residence in India
- The information related to a juridical person including proprietary or single person owned business entities.
- Protection of Right to Privacy under this Act is not applicable to a deceased individual
If we closely observe the above, these provisions defines the “Right to Privacy” which is not presently present in a statutory Act and is always derived from Supreme Court judgements. The definition covers both the Information Privacy and Physical Privacy and extends the definition of Information privacy to oral and written document dimension also.
Additionally the guaranteed right is restricted to living natural persons who are citizens of India irrespective of the place of residence and non citizens if they are residing in India.
This definition excludes illegal residents in India from protection. Naturally it excludes the business entities and deceased persons.
The exact manner in which the protection is provided will reflect in the compliance part of the law.
Having defined the basic objective of the law as to protect the Privacy right, the next section will be as follows.
Dimensions of the Right to Privacy
The Right to Privacy as envisaged under this Act shall be recognized as the choice of an individual to be “let alone” and extends to the following dimensions
(a) Physical Privacy related to the right of the person to prevent or otherwise regulate a third person gaining access to the physical proximity of the individual
(b) Information Privacy related to the right of the person to prevent or otherwise regulate a third person gaining access to the information in electronic form that provides access to the mind space or neuro space of an individual
The clause (a) here refers to the kind of privacy which Supreme Court decisions like the Kharak Singh Case addressed declaring the “Home as castle”
Clause (b) refers to the kind of privacy which the Puttawamy case addressed as the “Right to be let alone” which is a “State of Mind”. Additionally clause (b) recognizes the distinction between “Right of Choice” relevant in the general privacy understanding which belongs to a conscious mental activity and “Neuro Space” where the conscious choice is not available to an individual.
Thus this law will make India the second country in the world to address the Neuro Rights and we can claim it is progressive and contemporary.
Next, the rights which are covered in the GDPR and other laws are covered through a section on “Subordinate Rights”. These regulations may be stated as under.
Subordinated Rights
The Protection of the Right to Privacy as per Section 3.2 includes subordinated Rights prescribed under this Act includes
Every person whether an individual or a juridical person shall process data which is identifiable as related to a protected person subject to mandatory adherence to the personal data processing principles such as
i) Purpose Limitation:
No protected data shall ordinarily be collected or used in any manner except for a clearly identifiable purpose or purpose which can be considered as incidental to the main purpose except when the requirement is to explore and discover new uses for which a special “Discovery Consent” is obtained from the protected person.
ii) Collection Limitation
No person shall collect elements of protected data more than what is required for the specified purpose.
iii) Retention Limitation
No person shall retain protected data more than what is required for the specified purpose.
iv) Accuracy of Data
Every person using protected data shall endeavour to keep it accurate and ensure that incorrect data is duly corrected subject to production of reasonable evidence about the inaccuracy of the data and the accurate data.
v) Informed Consent
Every person collecting and using protected data shall ensure that the protected person to whom the protected data belongs shall be duly informed about the purpose of collection and use, the manner of usage, the time of retention etc and obtain a verifiable consent.
vi) Right to Information about processing
The protected person shall also have the right to request for information about the processing of protected data related to him any time after the collection and during the time the data is in use subject to such right being exercised responsibly.
vii) Right to Withdrawal of Consent
The protected person shall also have the right to request to withdraw the consent already provided subject to reasonable notice.
viii) Automated Decision Making
Any automated means of collection or use through a computing device shall be attributed to the person who caused the device to collect or use the data in a specified manner and shall be responsible for the consequences of any subsequent disclosure to a human being and automated decision that may cause a harm to the protected person.
ix) Right to Restrict disclosure of Profiling
Any person who has generated a profile of a Protected person shall not disclose it to any other person except with a specific consent of the protected person.
x) Right to Portability
A protected person shall have the right to request porting of protected data excluding the profile created thereof to the protected person only.
Where the profile is reasonably suspected to be causing harm to the protected person the protected person may request for a copy of the profile subject to protection of any intellectual property rights or Trade secrets of the person who created the profile.
xi) Right to erasure
Where the protected data collected by a person has completed its usage as per the specified purpose, it shall be archived as may be required for evidentiary purpose under law and be erased from active usage systems.
xii) Right to Forget
Where the protected data has been archived by the person who has processed it, the protected person may further request that the protected data may be removed from the archive through anonymization or deletion subject to appropriate regulatory review.
xiii) Right to Reasonable Security
The protected data shall be secured against unauthorized access, modification and denial of access by all persons who have authorized access.
xiv) Right to Grievance Redressal
Protected person shall have the right to an appropriate grievance redressal mechanism as prescribed under the Act.
After thus defining the rights, it is suggested that the obligations of the Government bodies is defined in one section as follows:
Obligations of the Government
(a) All the Government bodies including the Government of India the Governments in States and Union Territories and every organization which is part of such Government or Union Territory shall have the duty to protect the Right to privacy of Indian Citizens in harmony with the Right to protect the life and liberty as envisaged in the Constitution of India
(b) All such Government bodies shall institute reasonable and proportionate measures to meet the obligations of protecting such Rights.
(c)All such Government bodies shall designate a senior official to be responsible for compliance of the protection of the Right to Privacy and Right to life, property and liberty
(d) In the event of non compliance of the above, the designated person or in his absence the person responsible for the activities in the subject Government body shall be liable for disciplinary action
(e) If the non compliance is associated with malicious intention, the person responsible may be liable for punishment under appropriate criminal
Obligations of Non-Government Bodies
All organizations other than the Government bodies shall adhere to the provisions of this Act as stated further and shall be liable to penalties and punishments as specified here under for any contraventions thereof.
The further chapters can provide the details of compliance where also there is scope for innovation which we shall discuss in subsequent articles.
Advantages and disadvantages of the above approach is open for debate.
Naavi
P.S: These discussions are presently for a debate and is a work in progress awaiting more inputs for further refinement. It is understood that the Government may already have a draft and may completely ignore all these recommendations. However, it is considered that these suggestions will assist in the development of “Jurisprudence” in the field of Data Governance in India and hence these discussions will continue until the Government releases its own version for further debate. Other professionals who are interested in participating in this exercise and particularly the Research and Academic organizations are invited to participate. Since this exercise is too complex to institutionalize, it is being presented at this stage as only the thoughts of Naavi. Views expressed here may be considered as personal views of Naavi and not that of FDPPI or any other organization that Naavi may be associated with.