After the Supreme Court ruling in the Puttaswamy case, it is clear that the intentions of the Court is that Privacy is a Fundamental Right protected under the Indian Constitution. The Aadhaar judgement is still not announced and we are yet to find out whether use of Aadhaar as a citizen identity parameter linked to various services of the Government, Banking and financial data of individuals or property holdings to curb benami properties and blackmoney will be considered as acceptable or not.
The central debate of the acceptability of Aadhaar as an acceptable identity parameter will revolve around whether Privacy as a Right is paramount to what ever is the objective which Aadhaar linking is expected to achieve. Aadhaar is just one instance of an opposition to perceived erosion of the status of “Right to Privacy” as a supreme right of an individual. Beyond Aahdaar opposition lies the fundamental aspect of whether a citizen of a democratic country has any right that is more supreme than the Privacy Right.
We need to realize that in many instances of Cyber incidents, privacy activists often defend the Privacy Right so aggressively that we often forget that there is life beyond Privacy. In pursuing the “Right to Privacy”, we also discuss Data Protection Requirements and legislation like GDPR which adopts a policy of high penalty limits as “Administrative Fines” (as different from the wrongful loss suffered by a citizen data subject).
We however need to appreciate that Right to Privacy is a fundamental right but is subject to reasonable restrictions which include
a) interests of the sovereignty and integrity of India,
b) the security of the State,
c) friendly relations with foreign States,
d) public order,
e) decency or morality, or
f) in relation to contempt of court,
g) defamation or
h) incitement to an offence
Since “Privacy is a mental state of a data subject and differs from individual to individual it is impossible for a law to mandate based on the law subject’s mental state of “Feeling of being left alone”. Hence out of necessity, Privacy Protection is currently restricted to “Protection of Information Privacy” and the objective is to enable a data subject to have full control on determining how his personal data is collected and used.
In this context of “Information Privacy” being considered as “Privacy” and “Protection of Personal Information” as “Protection of Privacy”, we often consider “Data Protection” as same as “Privacy Protection”. When GDPR recognizes a role of a “Data Protection Officer” instead of a “Privacy Protection Officer”, it appears that GDPR considers that Privacy Protection and Data Protection is synonymous.
In India, until a new Data Protection Act comes into being, ITA2000/8 is the operative “Information Privacy Protection Act”. It defines Personal information, Sensitive personal information, responsibilities of a Data Processor and an intermediary (who is also a limited data processor), consequences of non compliance in the form of civil and criminal liabilities, the means of grievance redressal etc. It also prescribes data retention norms, defines powers of interception or data demand by authorities in the national interest.
ITA 2000/8 may be considered weak in terms of its implementation mechanism but the law itself does provide a comprehensive framework for data protection which covers not only personal data protection as envisaged under Information Privacy Protection objective but also the higher levels of data protection that goes beyond Privacy Protection into the area of “Information Security” within an organization.
Information security within an organization is an attempt to protect the entire data environment which is under the control of an organization from unauthorized access, modification and deletion besides ensuring against denial of access.
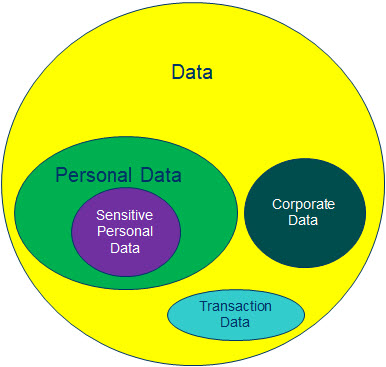
We must recognize that “Data Protection” as envisaged under ITA 2000/8 which is the goal of an information security team in an organization encompasses several types of data beyond the personal and Sensitive personal data which is the subject matter of Privacy protection. For example, every organization possesses its own data which could be business data and some which may be constituting trade secrets or intellectual property.
There may also be “Transaction data” which is data such as log records which gets generated during any encounter with an outsider through the systems. Some of these transaction data which may include the IP address from which a person has interacted may be considered as “Personal Data”. But the transaction data itself indicates that IP address ‘X’ interacted with IP address ‘Y’ and the interaction lasted for ‘N’ minutes and resulted in exchange of ‘P’ bytes in and ‘Q’ bytes out etc.
These transaction information is neither the sole right of the data subject or that of the company but is a joint property of both.
ITA 2000/8 tries to protect all these types of data by imposing “Due Diligence” and “Reasonable Security Practice” obligations along with asserting Data Retention and Data Demand rights by designated authorities.
Hence “Data Protection obligations under ITA 2000/8” is more comprehensive than Privacy Protection Requirements.
Now looking at the data protection obligations from the view point of the industry, a Privacy Protection Officer is satisfied if “Personal” data under his control is secured by appropriate means to avoid unauthorized access etc. But a Data Protection Officer of a company should be interested in protecting not only the Personal data but other types of data also. Hence it is not appropriate to restrict the role of a designation such as “Data Protection Officer” to only as a protector of personal information as GDPR actually does.
“Data Protection Officer” as a designation looked at in the Indian context is therefore larger than the DPO as identified by GDPR.
If we go another level up in the Data Eco system, data of individual entities (individual and corporate) when aggregated becomes “National Data”. National Data set therefore is an aggregation of data of individuals and corporates working within the jurisdiction of India. For the same reason, when information security obligations of individual entities get aggregated, that becomes the “National Security”. Some times we call this as “Cyber Security”.
If we adopt this convention, Privacy Protection is at the lower end and addresses security of personal data in electronic form, Information security addresses security of all data in information form within the control of one legal entity and Cyber Security is the security of all data in electronic form under the jurisdiction of the country.
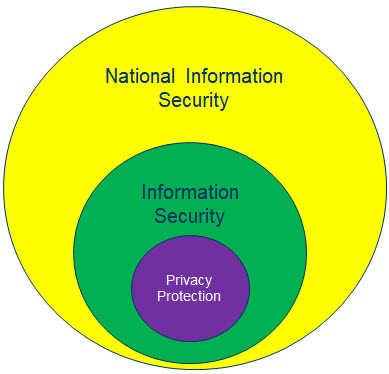
When we make data protection laws, we have a choice of making a Privacy Protection law and provide exemptions/derogations with respect to Information Security and National Information Security. Alternatively we can make a National Information Security law and create subordinate sectoral laws applicable to “Information within the control of a legal entity” and “Personal Information which is under the control of a legal entity”.
Laws such as GDPR adopt the first approach. It appears that ITA 2000/8 is closer to the second approach. If we donot properly prioritize our law making objective, there is a possibility of “Conflicts”.
For example, GDPR supports privacy according to which a recipient of an E Mail is not able to view the IP address of the sender which should be his right to information. A victim of defamation is unable to view the Who-Is data of the defaming website. Though work-around may be provided where by information is released upon legal demand, it is a hurdle placed on a genuine victim of a data related perceived crime in support of the privacy of an accused criminal. In many law enforcement situations, the golden hour of investigation is passed before the “Due Process” supported by a judicial order can be activated, permanently denying justice to the Cyber crime victims.
There is an urgent need to correct this skewed prioritization of “Privacy of a Crime Accused” ahead of the “Security of a Crime Victim” and the “Efficacy of the law enforcement system”. We need technical and policy initiatives that ensure that once a simple prima facie check is made on the identity of the person claiming a “perceived victim” status, the “Privacy Veil” has to be dropped and the “Right to Information” should take over as the over riding right. For example if a recipient of an e-mail demands the originating IP address of an e-mail he has received, it should be automatically provided since the identity of the recipient is inherent in the origination of the request itself. Similarly, if a Who-Is resolution request is invoked by a person with an irrefutable national identity such as a “Legally acceptable Digital Signature”, the Privacy veil on the who-is information should be dropped automatically.
I hope and demand that these and similar issues need to be addressed by the Indian Data Protection Act when it is released.
It is in this context that I would like to raise a slogan for the attention of the Government of India and the Supreme Court that “Cyber Security is my Fundamental Right and should override other recognized fundamental rights such as Privacy Right as well as Right to Freedom of Speech.”
I look forward to the comments from the Data Security Community which includes Law Enforcement persons.
Naavi