The essence of corruption is that it takes root in the principle that “One who financially benefits from an act turns soft on the legitimacy of such an act”.
It is therefore understandable that one financially benefits by a crime, he would turn soft to the crime. Most ISPs today are soft on pornography or spamming because they benefit from the traffic.
Privacy is preferred by many businesses because criminals thrive in an anonymous world. Hence Apple wants to protect the encryption of even the ISIS customers and ICANN wants to protect the identity of website owners who openly indulge in frauds.
Google does not want to disclose the identity of its customers who send fraudulent e-mails except when pushed to the wall by the law enforcement. Proton mail, anonymization service providers and the bullet proof hosting services exist because criminals are their valued customers.
Similarly, if the regulators benefit from their crimes, with an opportunity to levy a hefty fine, criminals may consider it better for them, because then there is a possibility how so ever small it is that the regulator would start nursing a soft corner for them.
This tendency must be identified and resisted.
When looking at some of the recent GDPR fines on Airbus and Marriott hotels a thought occurs whether the regulatory authorities are silently gloating over the opportunity to collect hefty fines when the companies are already wilting under reputation loss, business loss and perhaps individual law suits.
In the Airbus data breach incident, the ICO has levied a fine of Euro 200 million which is said to be a record. This is at 1.5% of the global turnover of the company though the ICO had the discretion to fine up to the upper limit of 4% if it wished.
According to Airbus the data breach occurred due to a sophisticated, malicious criminal attack which compromised customer names, email addresses, payment card information, credit card numbers, expiry dates and credit card security codes. (British Airways says that CVV numbers were not stored by them).
The Marriott issue was slightly different. In this incident for which ICO fined Sterling 99 million, Marriot acquired Starwood in 2016 whose systems were not adequately secured. The data breach occured in the period between 2014-2018 and ICO felt that sufficient due diligence was not exercised during the acquisition process.
In both cases as in many other instances of data breach, hackers targeted specific assets and awere able to penetrate them with sophisticated attacks. Of course this also indicates that the securiy was insufficient and was compromised.
However, when levying the fines, the regulatory authorities need to remember that the organizations might have taken steps which might have failed in the given circumstances. Hence the authorities need to be considerate to whether the organization was “Negligent”, “Reckless” or was outsmarted by the hackers before deciding on the fine.
After all, fines are supposed to be a deterrent and not a means of revenue generation by the regulatory agencies. But this thought is likely to be corrupted in due course as the colour of money in the hands of the regulators will change their perception.
Even if the initial crop of regulators may be honestly levying the fines only with an intention that it will be a deterrent for others, in due course, the earnings on fine collection gets into the balance sheets of the regulators and it will soon become a significant revenue item.
At this stage, the financial managers of these agencies will start checking the “Growth” of “Earnings through collection of fines” and start measuring the efficiency of the regulator from the amount of fines collected.
When the volume of fines collected determine the promotion of the officers of the supervisory authority, they will start enjoying the power to impose large fines to an extent that the expenditure budget of their organization will be balanced with the levy of the fines. The fines will then be decided not as a “Percentage of the global turnover of the company where the data breach occurred”, but as a “Percentage of the annual expenditure of the regulatory agency”.
This is not an allegation but a reflection of how things may turn out in future based on an understanding of human tendencies.
To prevent this trend developing and taking root and to emphasize that the role of the regulatory agency is to improve data security and not collection of fines, these agencies need to deploy their own policies where the officials do not become tyrants.
The efficiency of the officers of the regulatory authorities should therefore be measured positively with the number of cases detected and fined but negatively with the increase in the quantum of fines.
In India where we are still in the process of finalizing the PDPA, we should consider if some checks and balances can be introduced in the regulation itself to ensure that the DPA does not become seduced with the possibility of levying large fines just because it is permitted under law. We must introduce a “Justification Statement” to be provided by the authority every time a fine is levied which should be available for review in a suitable manner.
If such self imposed restriction on the quantum of fines is not introduced, regulators may subconsciously feel happy whenever a hacker successfully publishes a data breach since it becomes an opportunity for the regulatory agency to profit from.
If the law enforcement agency then asks for some assistance in prevention of such crimes, the regulatory agency even if being capable of giving good advice may refrain from doing so since reduction in crime will reduce their revenue.
We should be conscious of a possibility of such a tendency developing in the market and debate the measures to prevent it.
Comments are welcome.
Naavi
More on Marriott breach
Where to the fines go?


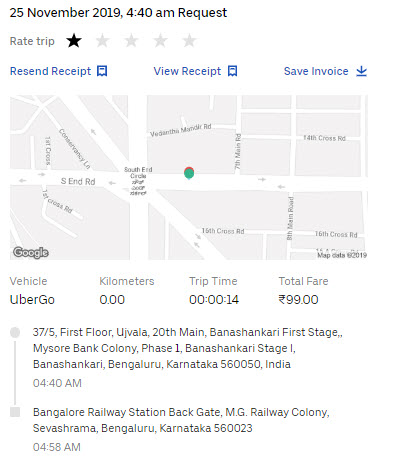 The first picture here was taken from the Uber website and indicates in the billing that I have travelled from one place in Bangalore 560050 to another place in Bangaore 560023.
The first picture here was taken from the Uber website and indicates in the billing that I have travelled from one place in Bangalore 560050 to another place in Bangaore 560023.