“Life Cycle” starts from birth and ends with death. In the case of humans, life form comes from the environment (in the form of the Pancha bhootas) and goes back to the environment. Human life has two components namely the physical body and the “Life within it”. Human body is constantly aging and growing and is never static. According to wise men, even after a person dies, some activities of the human body such as hair growth and nail growth continues for some time. So, there is a specific distinction between “Body” and the “Soul”.
In non-living bodies, the structure may remain static unless otherwise affected by an external agency. A stone may remain static unless rain water flowing over it or dust accumulating over it keeps it either eroding or growing over a long time frame. This however is different from human growth which occurs from within with the intervention of what we identify as “life”.
It is interesting to ponder when does a “Stone” take birth and when does it die and what happens to it during its life cycle?
A “Stone” is born as “Soil”. It is compressed under the earth until it becomes hard. During this process fine particles may come together as a larger group of particles bound together closely. This may then come out of the earth and get exposed as stones and rocks. Some times it may come out like Lava and there after solidify into a rock form on cooling.
The death of a rock is in it being powdered back into soil form. Hence the life cycle of a rock is from the soil back to the soil. In the intermediate life cycle it can assume different forms such as sedimentary rocks, Metomorphic rocks or igneous rocks etc. Some may be carved as “Statues”, “Idols”, “Slabs” etc.
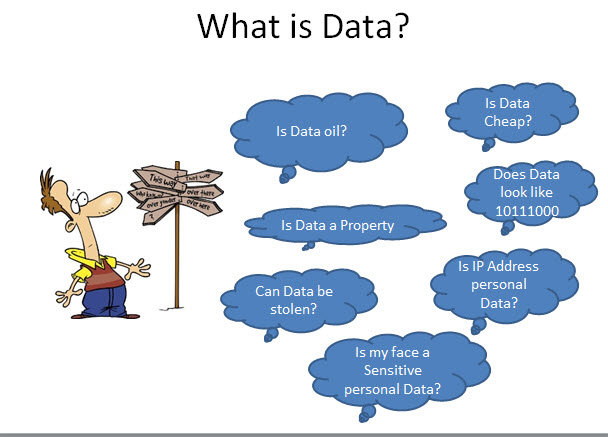
“Data” life cycle has some similarity. It is debatable if it has “Life”. It is also interesting to think …When does “Data” take Birth and When does “Data Die”? and what forms it can take in between is difficult to answer. During its life cycle, Where does “Data Reside”? Is it in a hard disk”, Is it in a tape? Is it in a Memory Card? how does it flow from one data holding device to another?… Will it copy? or will it move?.. are questions to which we believe we have an answer on a contextual basis. We say this can be this and also that most of the time.

If Data can be in different forms at different times, it is fine. But can some body explain this? Physicists often say Light is a stream of Photons but Light also behaves some times like a wave. But some body has to explain how can it be both? and at what circumstances the Light Photons behave like a wave? That explanation is what we may call the “Light Wave Theory”Another set of Physics went further and said there is a “Matter Wave Theory ” according to which all “Particles” have a “Wave like behaviour”.
Now, if we have doubts about “What is Data”? and “Data is many things to many people based on the context”, we cannot simply accept this “Context Based Excuse” as a “Definition”. Based on one such notions, law makers create laws and Judges interpret them according to their own whims and fancies and the industry is left to deal with the issue on an adhoc basis.
Some times the Supreme Court thinks “Data Disclosure” is a freedom or expression and some times it thinks it is a “Privacy Right”. Same kind of uncertainty exists when Quantum Computing says a “Data State can be either zero or one at the same time”.
If the differences between “Data” from classical computing and “Data” from Quantum Computing has to be resolved, and “Data” from Classical/Quantum computing perspective to Judicial perspective has to converge, then we need a “New” “Theory of Data”.
Naavi is trying to explore this interesting theoretical concept of “Data” and trying to find a model of description which should fit into the different perceptions of “what data is”.
This is the “New Theory of Data” which will be revealed bit by bit here. Watch for more…
(P.S: This discussion is purely academic)
Naavi