
Ollie Robinson made an impressive Cricket Test debut at Lords last week against New Zealand. He virtually saved England from losing the test by not only taking 7 wickets but also scoring 42 runs at a critical stage in the first innings.
However a lobby worked against him to point out tweets that had been posted by him in 2012 which was allegedly “Rascist” and “Sexist”. The English Cricket Board (ECB) in a holier than thou reaction, immediately suspended Mr Robinson indefinitely and said that they will conduct the necessary enquiry.
They said
” Ollie Robinson has been suspended from all international cricket pending the outcome of a disciplinary investigation. He will not be available for selection for the second Test against New Zealand starting at Edgbaston on Thursday 10 June. Robinson will leave the England camp immediately and return to his county”
Subsequently the England Prime Minister Boris Johnson said that the punishment was harsh and he was promptly criticized. It was unfortunate that even our own much loved cricketer Farooq Engineer was critical of Robinson as well as Boris Johnson for his remarks.
Ravichandran Ashwin however came up with a very mature response stating
“I can understand the negative sentiments towards what #OllieRobinson did years ago, but I do feel genuinely sorry for him being suspended after an impressive start to his test career. This suspension is a strong indication of what the future holds in this social media Gen”
Further, earlier statements on Twitter from Jimmy Anderson, Eion Morgan, Jos Butler have also been unearthed accusing them of passing intemperate remarks may be called rascist. They are more recent than 2012.
Anderson was reported to have stated
“I saw Broady’s new haircut for the first time today. Not sure about it. Thought he looked like a 15 yr old lesbian!”
As against this, it is interesting to note what did the offending tweet from Robinson stated.
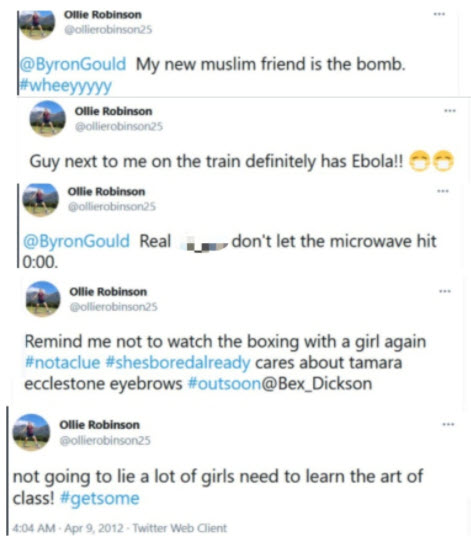
[Another publication quoted the following tweets:
“I wonder if Asian people put smileys like this ¦) #racist”; “My new muslim friend is the bomb. #wheeyyyyy”; “Real n—– don’t let the microwave hit 0:00”; and “Wash your fingers for the mingers #cuban”.]
Conservative party leader’s came up with statements suggesting that the statement of Mr Robinson should be seen in the context of a ten year old view of a teen ager and his current apology. However, the labour party which is a known supporter of Muslim interests in England and passed many remarks against Indian interests in the past jumped into the political debate to oppose the views of the conservative party leaders making the issue political.
We know that many times Cricket boards provide suspended sentences so that the career of an individual is not affected by an immediate ban. We have also seen that in civil suits we have a period of limitation and in criminal law, we have the principle of a convict being “reformed” and released into the world. Many rapists and murders come out of jail and lead normal life after a sentence of 5 to 7 years.
In such a situation, it is clear that the immediate suspension from all international cricket and throwing the person out of the team environment immediately and banishing him to his house in utter humiliations appears a very biased decision from ECB. Prima facie this decision itself appears an “Appeasement action” taken by ECB in support of the Muslims and Cubans who were referred to in Mr Robinson’s tweet.
Though the use of “Muslim” and associating it with “Bomb” must have irritated many, we should also observe that he has added the word “Friend” to his description. Hence there was a neutralization of the terror association within the statement itself.
The proposed punishment is definitely “Disproportional” to the gravity of the offence and appears to has been taken for political reasons.
From the Privacy perspective, we do get a thought that probably Mr Robinson could have exercised his “Right to Forget” some time back so that this controversy could have been avoided. This would not however prevented the possibility that some archived version of the tweet could have still surfaced.
Psychologists say that during adolescence, harmonal changes in human beings bring about some changes in a person’s behaviour and could make him/her do things which he/she may correct in later years as maturity dawns in. Many College boys and College girls might have been eve-teasers or adam-teasers but later turned into perfect gentlemen or women.
In fact we recently had controversies surrounding Hardik Pandya’s remarks in a TV show for which some limited punishment was given by the Indian Cricket Board. We know that even Gandhi whom we revere as Mahatma did admit of teen age indiscretions and we all admired him for his honesty.
Many of our celebrities may have had chequered careers during their younger days and if one digs deep, the past of many respected individuals may be tainted with such tweets or articles in print or recorded voice messages.
The action of ECB therefore appears to be more a case of reverse rascism than a move born out of a genuine reason of discipline. There is a need for investigation of how the tweets surfaced, who brought in a complaint to ECB and why such a severe action was contemplated. There could be political lobbies which were trying to create a political storm and gain sympathy of Muslims and Cubans for political gain.
It is high time that such incidents are evaluated based on the context and not literally on the basis of the words used.
An AI algorithm may commit such a mistake but human beings endowed with the power to think should not commit such mistakes.
The action of ECB will have a chilling effect on free speech and needs to be condemned.
Naavi
Reference articles
Republicworld.com
Indianexpress.com





 Foundation of Data Protection Professionals in India (FDPPI) is an organization of the Data professionals dedicated to the empowerment of the Data Protection eco system in India.
Foundation of Data Protection Professionals in India (FDPPI) is an organization of the Data professionals dedicated to the empowerment of the Data Protection eco system in India.





