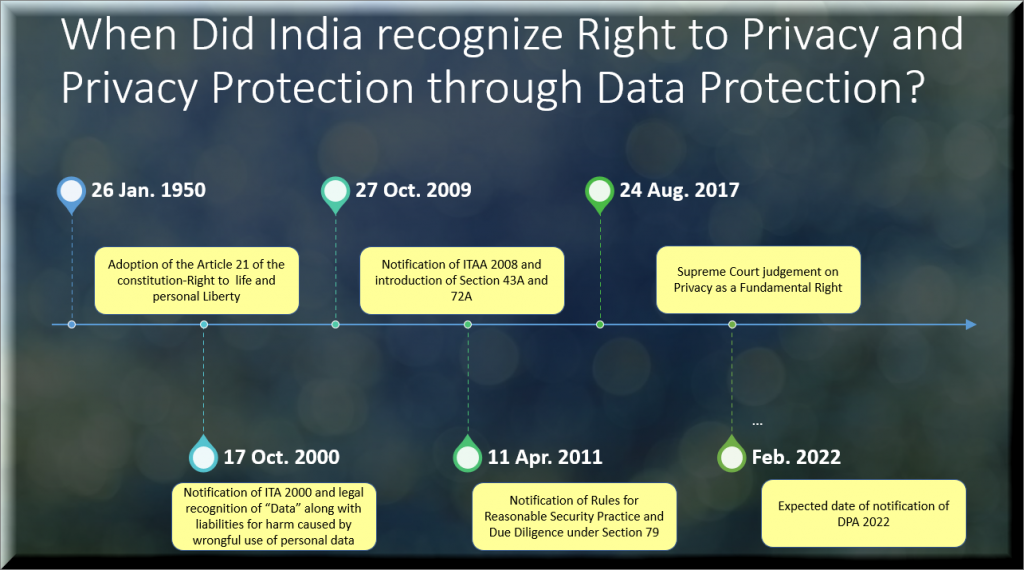
When India adopted Information Technology Act 2000 as the law that first recognized electronic documents and also introduced the concept of “Vicarious liabilities/Due Diligence” for organizations, Naavi came up with the concept of “Cyber Law Compliance.
Then when the amendments of 2008 came into effect, Naavi upgraded the concept of Cyber Law Compliance with a specific framework IISF 309 or Indian Information Security Framework so that organizations can have a specific framework to work on compliance.
When the PDPB 2018/2019 were introduced as a bill in the Parliament and sought to replace Section 43A of ITA 2000/8 with a complete act Naavi and FDPPI worked on the concept of PDPSI or the Personal Data Protection Standard of India as a framework for being compliant with PDPB 2019 as an extended due diligence under ITA 2000/8 to be rolled over to the compliance of PDPB 2019 when it became an act.
The JPC however made a surprise modification in the PDPB 2019 by renaming the PDPB 2019 as DPA 2021 and calling it a common law for “Data Protection including Non personal Data protection”. Though ITA 2000/8 will lose only one section namely Section 43A on the passage of DPA 2021 and the rest of the Data Protection aspects continue to be covered by ITA 2000/8 under the supervision of the CERT-In and the Adjudicators, the change of name of the Act as Data Protection Act and introduction of Section 2(d) stating that the Act is applicable also to non personal data brought in a significant difference to the compliance requirements under the Act.
At present though the title has been changed and Section 2(d) has come into reckoning the only operative change is in the reporting of Data Breach under Section 25 where breach of non personal data also has to be reported to the DPAI along with the breach of personal data if any.
Where in a single data breach incident both personal and non personal data is breached, the data fiduciaries and Non personal data processors need to report the breach to the DPAI. The DPAI reserves the right to give any directions to the reporting company/organization on the action to be taken.
So far there is no indication whether the obligations of a data processor under ITA 2000 has been modified in respect of the data breach report to be sent to the CERT IN. It can therefore be presumed that in case of data breach involving both Personal and Non personal Data, report has to be sent to both CERTI In as well as DPAI. Both may come back with their own directions on what the organization needs to do. Probably CERT IN will leave it to the DPAI to provide directions regarding how the data principals need to be informed etc. In the case of non personal data breach, the DPAI may leave it to the CERT In to provide whatever directions it wants to provide. Any other approach will be not in conformity with Section 56 of DPA 2021 according to which CERT IN would be deemed as a “Sectoral Regulator” having concurrent jurisdiction under a law of the Parliament.
While the regulatory agencies would be able to coordinate between themselves, the PDPSI and IISF 309 also need to reconcile as frameworks that could guide organizations for compliance of ITA 2000 and DPA 2021.
PDPSI itself was built on the principle of “Unified Framework” to have a single framework for PDPB 2019 and GDPR or other data protection laws to which an organization is simultaneously exposed to and hence it is natural to ensure that between IAT 2000 and DPA 2021 also there has to be a “Unification” of compliance requirements.
Some of the other systems of frameworks create multiple frameworks for different instances of requirements of an organization so that there is a greater focus. It also helps in certification so that multiple certification requirements can be created for the security compliance industry. However from the perspective of a compliant organization, trying to get certified for multiple standards all leading to “Information Security” whether it is “Personal Information Security”, “Non Personal Information Security”, whether the system being audited is “ISMS”, “PIMS” or “DPMS”, is a over lap of efforts leading to additional cost and effort with marginal benefit.
FDPPI would therefore like to stick to its principle of a framework for “Compliance of the Data Protection Law”. Earlier PDPSI was meant to certify the PDP-CMS (Personal Data Protection Compliance Management System) and now it has to transform itself as a means of being certified for compliance with the new “Data Protection Compliance Management System”.
Accordingly necessary minor modifications are being made to the erstwhile PDPSI standards and implementation specifications to accommodate
a) Consent for anonymization
b) Reporting of Data breach of non personal data
and any other measures that the DPAI may include in its future notifications.
Compliance to ITA 2000 will be an extension like the current extension for GDPR, CCPA etc and will be handled with the classification of data into
a) Personal Data under DPA 2021
b) Non Personal Data under DPA 2021
c) Personal Data under GDPR
d) Personal data under CCPA… etc
Having classified data to which DPA 2021 is applicable into two categories, personal and non personal data, the first level compliance will be as per DPA 2021 which will only cover the data breach notification requirement as of now. Where compliance to ITA 2000/8 needs to be assessed, the controls will be interpreted from the requirements of ITA 2000.
ITA 2000 compliance requirements will basically revolving around Confidentiality, Integrity and Availability of non personal information along with the Section 7A (data integrity audit), Section 3/3A (Authentication) , Sections 69.69A,69B, Sections 65-75 etc.
The Certified PDP CMS auditors have presently been trained in PDPB 2019 compliance and will adopt to DPA 2021 requirements. They have been exposed to ITA 2000 compliance only to a marginal extent. Hence it would be necessary for the PDP CMS auditors to undergo an additional training on ITA 2000/8 compliance requirements.
Measures are being initiated to ensure that this change of PDPSI auditors to DPSI auditors is being worked out.
Naavi