In continuation of our discussions of yesterday regarding TransUnion CIBIL, further thoughts on the data protection regulatory aspects are being discussed below to draw the attention of RBI, CERT In, MeiTy, Ministry of Commerce etc.
Data Protection laws try to protect personal data handling by insisting that
-
- The first collector of personal data from the data subject provides a clear Privacy notice and obtains an informed consent, which shall be an “Explicit Consent” in the case of sensitive personal information. GDPR considers the collector as the “Data Controller” or a Data processor working under a contractual direction of another Data Controller.
- Subsequently, every transfer of the personal data is subject to consent and a contract that binds the downstream receiver to the same level of protection that the consent expects.
- There is also a clear “Cross border transfer” restrictions that need to be adhered to.
In the case of CIBIL, data subjects donot have any direct communication from CIBIL that they have collected the personal data which is being processed in a specific manner etc. They have silently collected the data from the Banks and using it to influence the new loan applications of the data subjects without informing them the reasons why their rating has gone up or down.
In the case of CIBIL, which was initially promoted by a consortium of Indian Banks and regulated under RBI regulations, the personal data of millions of Indian citizens were aggregated. The objective of this was to prevent bad borrowers from taking the Banks for a ride by borrowing from multiple Banks and defaulting in the repayment.
However, contrary to this original objective the Credit Information Companies (CICs) used the data to “Profile” the borrowers and assign a “Credit Rating”. Initially, this was meant to assist new lenders with an indication of the credit worthiness of the borrowers.
As days passed, many lenders took the easy way out and did not conduct their own credit check on the borrowers and depended entirely on the credit rating of the CICs. The borrowing limits were fixed on the basis of the “Credit Score”. Lower the Score, lower would be the limit. In a way, this resulted in an “Automated Decision Making” by the lenders on the basis of the credit rating.
At the back end, the CICs used parameters such as length of credit history, number of defaults, overdues, loan enquiries made etc.., and arrive at the credit rating using some kind of an algorithm. Considering the way technology is used today, it can be presumed that the final credit score is the outcome of the processing of the set of parameters chosen in the chosen algorithm. There is most likely no human element in assessing the credit risk and the decision is “Automatic”.
Thus the decision to lend or not to lend taken by the lender is directly influenced by the credit rating which is a result of an automated decision making in itself.
Hence the credit score determination falls into the category of profiling with automated decision making under the data protection laws. This therefore requires an “Explicit Consent” from the data subject.
When the credit scores are incorrectly computed either because the algorithm is imperfect or the input data is inaccurate, the data subject is subject to a loss of reputation and denial of credit. This is therefore a serious legal issue that creates a liability on the credit rating agencies.
In this case the CICs need to be subjected to the rigorous privacy protection measures contemplated under the privacy regulations.
Data Laundering
One of the data protection requirements is the data transfer regulations. In India there is now a debate on “Data Sovereignty” and “Data Localization”. In this context , the data collected for profiling borrowers and developing the Credit scores become “Sensitive Personal Data” that should be subject to the Data Localization requirements.
To overcome the regulatory controls, some companies may use devious means to access the sensitive personal data and indulge in “Data Laundering” by taking over companies who already posses such data. In such cases a foreign company that takes over an Indian company will have access to the data and once access is availed, it is not difficult for the company to transfer it out.
Hence in case of “Critical Personal Data Processing companies”, it may be necessary to prevent the take over to prevent cross border transfer or have an increased oversight or conditions imposed on take over.
TransUnion take over of CIBIL appears to be one such transaction where, TransUnion took over CIBIL by acquiring equity and thereby got control of a huge amount of data of 550 million citizens of India. Whether this was “Data laundering” and whether there was a suitable over sight from RBI is a matter to be investigated.
Trans Union -CIBIL take over
When CIBIL was initially in operation, it was controlled by Indian Banks and we could presume that the data was held in India. Probably some time later the data could have been hosted on cloud servers belonging to non Indian Companies and stored abroad.
Presently we understand that Trans Union CIBIL is owned by TransUnion to the extent of 92.1%. According to the website of TransUnion in 2017, TransUnion acquired 92.1% stake in 2017 during the first Modi Government.
Initially, the shareholding of CIBIL’s was held by State Bank of India, Housing Development Finance Corporation Limited, Dun & Bradstreet Information Services India Private Limited and Trans Union International Inc. The shareholding pattern was in the proportion of 40:40:10:10 respectively.
This changed in 2009 to what is indicated (reference:taxguru.com) in the following diagram which shows that as of 15th September 2009, the shareholding of CIBILwas as follows.
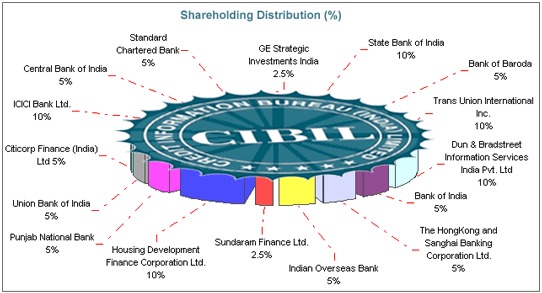
| State Bank of India |
10% |
| HDFC |
10% |
| ICICIBank |
10% |
| Dun & Bradstreet |
10% |
| TransUnion |
10% |
| Bank of Baroda |
5% |
| Bank of India |
5% |
| Indian Overseas Bak |
5% |
| Punjab National Bank |
5% |
| Union Bank of India |
5% |
| Central Bank of India |
5% |
| Citicorp Finance (India) ltd |
5% |
| The Hongkong and Shanghai Banking Corporation Ltd |
5% |
| Standard Chartered Bank |
5% |
| Sundaram Finance Ltd |
2.5% |
| GE Strategic Investment India |
2.5% |
It is clear therefore that the initial shareholders had diluted the shareholding mostly in favour of the other Indian Banks. TransUnion also maintained its share holding at 10%.
From this stage to the current level of 92.1%, TransUnion must have grabbed the share holding of most of the other share holders.
It is intriguing that RBI allowed the Banks and each of the Banks got their shareholder’s approval to divest their holdings in favour of one US company as a coordinated approach. If the share holding of one foreign entity raised to 92.1%, then it was a matter that should be the concern of Direct Foreign Investment in a Banking related activity.
How was this FDI permitted in 2017 is intriguing.
How did all the Banks were made to agree to sell their stakes to one foreign entity?
What was the price?
What were the board decisions at that time?
Did any board member object to this sell out? ….etc
are issues that need investigation from the CBI itself.
Modi Government needs to Clarify
A deal of this nature provides a definite scent of corruption and members of the Modi Government including Mrs Nirmala Sitharaman and Suresh Prabhu who were the commerce ministers in 2017 need to clear their positions.
Going forward, action should be initiated to disallow the majority share transfers to TransUnion and the shareholding has to be reverted back to the Indian Banks.
The heads of the Indian Banks in 2017 who must be aware of the reasons why they agreed to divest their shares also need to clear their position as otherwise it would be presumed that all the Banks were forced to sell their shares probably by the RBI and they did not raise any objections either because they were naive enough not to see anything wrong in the deal or were silenced otherwise.
It is interesting to note that Mr Raghuram Rajan was the RBI Governor of that time and he was a close associate of Mr P Chidambaram. Did he have a hand in these deals? is a doubt which naturally arises.
Mr Modi and Mr Amit Shah may be busy in other things and would like to let this pass and go un-investigated. But this will explode into a scam sooner or later and that time, questions will be asked why Mr Modi and Amit Shah decided not to pursue this. Was it because Mr Arun Jaitely was the finance minister of the time and they donot want any discredit to come to him?
Now that this issue has come to public, the public will be awaiting a clarification from the RBI, the Ministry of Finance and the Ministry of Commerce.
I have not at present obtained any direct information from TransUnion or the ministries. It is possible that the entire transaction is above board. But it needs to be clarified by the right persons.
I look forward to the clarifications from any of the parties who have been indicated here, including the 16+ share holders of CIBIL.
Academically, we need to check if PDPA provides sufficient cover to recognize and punish Data Laundering.
Naavi






