“Information Security” has been a term which we are all familiar with. But in recent days, people have been using a term “Data Protection” and talking as if it is different. This is intriguing and requires some discussion.
If we look at the definition of “Data” under ITA 2000/2008, it appears that there is no difference between “Information” and “Data”. Both terms refer to binary expressions which can be interpreted by computer devices as “Text”, “Sound” or “Pictures” or a combination of the same. Research is going on how the “Binary expressions” can also be converted into what we can feel by touch or what we can smell or taste. After all if we can establish a connect with the neurons in the human brain and send some stimuli triggered by some binary expressions, we will have a situation where human faculties of seeing, hearing, touching, smelling or tasting can all be replicated by binary triggers which may be called “Software” with the use of appropriate “Hardware”.
Hence if we talk of “Data Protection” as a measure of “Protecting” “Data or Information”, then our controls to ensure “Confidentiality”, “Integrity”, “Availability”, as well as “Authentication” and “Non Repudiability” should be considered sufficient to protect all kinds of data. The CISOs today along with their team of IS trained and certified army of professionals are geared to protect information and hence should be also capable of discharging responsibilities of “Data Protection” in whatever manner it is described.
However in recent days, there is a clamour for another kind of professionals in the industry. These are some times called “Privacy Officials”. Is this necessary?… Is this desirable? is a question that is bothering many.
These Privacy officers have a slightly different role than the Information Security Officers because, IS professionals focus on protecting the “Binary Data” without any reference to what a given set of binary data may mean when looked through an application and converted into a text or sound or picture.
On the other hand the Privacy officer looks at what the binary data translates into and whether it contains a name of an individual or any data which is identified with an individual. Such information is classified as “Personal Information” and the “Privacy Professional” focusses on how to protect such “Personal Information or Personal Data”. The Privacy officer then thinks of controls which are beyond what the IS professional has thought of. The Privacy Officers therefore require to be heard separately.
Again as distinguished from the Privacy professionals who work within an IT organization trying to protect the personal data, there are privacy activists like lawyers who try protect the right to privacy of people, under the Constitution as a Right to liberty and Right to dignified life. These advocates are not protecting “Data” but they are protecting “Privacy”. The Courts also are making orders about “Privacy Protection” as if “Privacy Protectio” and Data Protection” are one and the same.
We therefore have two kinds of Privacy professionals, one trying to protect the Right to Privacy under the Constitution who fights in a Court, and another set who work within the IT organizations to protect the “Personal Data”. Are they same? or Different?…is another dilemma we need to sort out.
Same way, the current IS professionals protect all data while the Privacy Professional in an IT organization tries to protect the “Personal Data”.
Since “Personal Data” is a subset of “Data” managed by an organization, it appears that the IS managers are already functioning as “Personal Data Protectors”. In such a scenario, there is a genuine question on why do we need a separate set of professionals called “Privacy Professionals” or “Data Protection Professionals” and some of them being coronated as “Data Protection Officers” (DPO).
India is on the threshold of a new Personal Data Protection Act (PDPA) which recognizes a special role for DPOs and if the legal provisions are taken seriously, the DPO will be a senior executive who will be reporting directly to the Board and some times even complain to the Data Protection Authority (DPA) even against the Board.
If we donot understand why this special status is given to the DPO, we are bound to have a fight within every organization where the CISO will expect that the DPO should report to him and not to the CEO or the Board. If the DPO reports to the Board or even to the CEO, it will undermine the position of CISO and this would create a disruption in the hierarchy.
To understand the difference why a protector of a subset of data needs more power than the protector of the super set of data, we can look around us to see the plight of the Police in Delhi who were struggling to control the Shaeen Bagh protests.
Normally one will say that Shaeen Bagh protest is like any other sit in protest and the Police should be able to handle it as they handle a worker’s strike or any other gathering.
But controlling the Shaeen bagh was beyond the capability of the Delhi Police because there was sensitivity to the situation. The protesters were all Muslims and any action such as a lathi charge could only result in a riot as it happened later. The possibility of international ramifications of a charge on the protestors could also not be ruled out. Additionally most of the protesters were women and children and this human shield could not be tackled just as any other group of protesters.
Similar protests in China or Hongkong would have been handled differently and Indian Police did not have similar powers. This made a difference between their success or failure.
In other words , “Who the protesters were” made a difference to “What security operations could be conducted”. If the Police had treated them as just another group of protesters without having any racial outlook or discriminatory outlook, they would have been accused as “Communal” and “Gross violators of human rights”.
Hence “Controlling the Shaeen bhag protest” was different from controlling “Any other Protest”.
This is exactly the situation that confronts the “Information Security professionals” and the “Data Protection Professionals”. Even though “Personal Data” is part of the “Data” , those designated to protect the Personal data need certain skills that are different from those who are handling protection of “Data” in general. “What the data is” makes a difference between the protector of “Data” and protector of “Personal Data”.
It is for this reason that the DPO is having a different brief than the CISO when it comes to protecting the data under his domain.
If “Personal Data” is more sensitive than “Data” in general then the DPO must have all the skills of a CISO and some thing more to handle the sensitivity. Hence the DPO assumes a role more important than the CISO in the organization and has to be on par with a CISO or even above him.
As a result the CISOs of today will have to accommodate the raise of another class of professionals called DPOs to occupy key professional positions in the organization. Some of these could be experts in Data Protection Laws but without much understanding of the technology and IS functions. Until the Data Protection lawyers acquire a reasonable understanding of the technology, there will be a constant friction between the designated DPO and the current CISO.
Not all CISOs may be ready to acquire additional skills required to be elevated to the position of DPOs and giving up the tag of CISOs since at present the importance of DPOs is a little bit obscured compared to the importance of CISOs in the industry. But sooner or later they will realize that DPO is a more elevated position in the organization and unless they acquire additional qualifications such as the “Certified Data Protection Professional” they may fall behind in the race to professional growth.
It is high time that CISOs and IS professionals realize this development and take steps to preserve their current industry position by acquiring additional Personal Data Protection Certifications.
CISOs and IS officials in India should also realize that acquiring certificates for GDPR knowledge with international certification agencies is not a substitute for acquiring certificates for PDPA knowledge and certifications that focus on the requirements of Indian Data Protection Professionals.
In this direction, the Certification program of FDPPI stand out in a class of its own and deserves a serious look.
Naavi

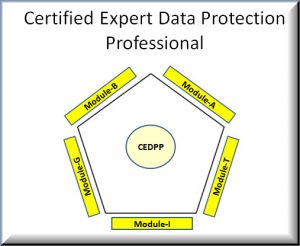 Professional” program to include a module on behavioural skills required for a DPO. This will be part of the FDPPI’s plans for extending the current knowledge modules such as Module-I, (Indian Laws), Module-G (Global Laws) and Module -T (Technology). The other two modules namely
Professional” program to include a module on behavioural skills required for a DPO. This will be part of the FDPPI’s plans for extending the current knowledge modules such as Module-I, (Indian Laws), Module-G (Global Laws) and Module -T (Technology). The other two modules namely