 Cyber Law College in association with FDPPI has earlier launched two programs related to building legal awareness on Data Protection Laws connected with the “Certified Data Protection Professional ” (CDPP) course. These were part of the larger 5 Module course to build 360 degree skilled Data Protection Professionals in India. The remaining three modules were one on Technology, Audit and Behavioural skills.
Cyber Law College in association with FDPPI has earlier launched two programs related to building legal awareness on Data Protection Laws connected with the “Certified Data Protection Professional ” (CDPP) course. These were part of the larger 5 Module course to build 360 degree skilled Data Protection Professionals in India. The remaining three modules were one on Technology, Audit and Behavioural skills.
The training for Module-I covered Indian Data Protection laws and training on Module G covered the global data protection laws.
Now FDPPI and Cyber Law College are launching the course on the Audit Module, namely Module-A.
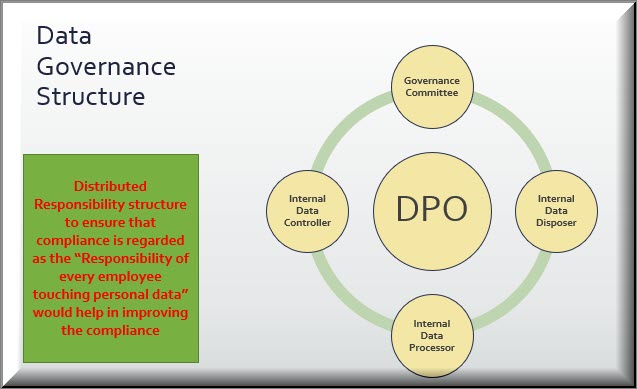
During this program, scheduled as a 12 hour online program, the Art and Science of Data Audit would be discussed. Since this is the first such program which is being conducted and introduces many new concepts including Valuation of Data in a Balance Sheet, Distributed Responsibility for implementation, etc., there is a possibility that the program may be extended beyond 12 hours if required.
The discussions will cover the conceptual difference between an “Assessment” and “Audit”, different types of audits that one encounters in the Data Protection profession , the objectives of each of these audits, the modalities of how a practitioner may conduct such audits etc.
The Data Protection Impact Assessment (DPIA), Harm Audit, Data Breach Audit and Data Protection compliance audits will be discussed separately.
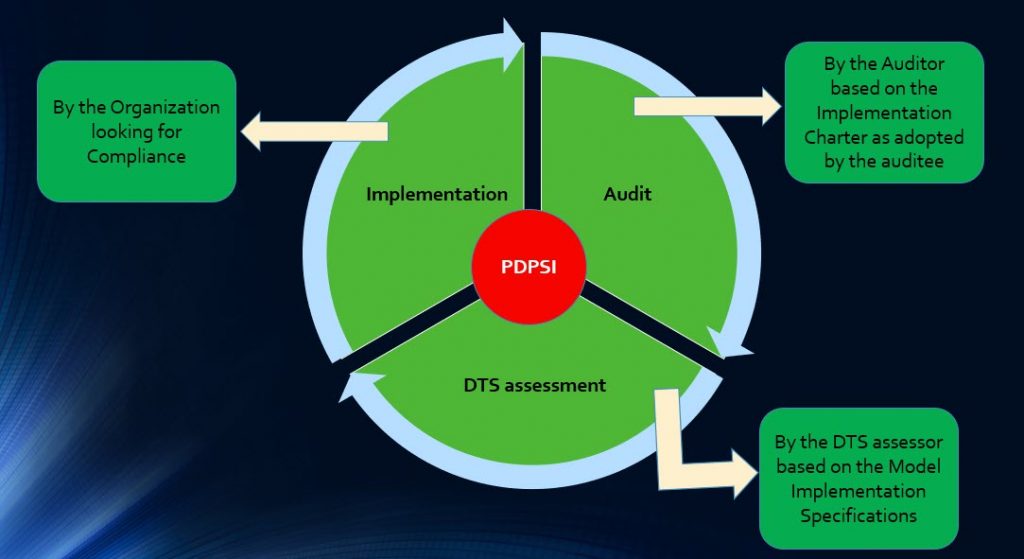
The Data Trust Score (DTS) Assessment which is a part of the Indian data protection regulation will also be discussed in detail.
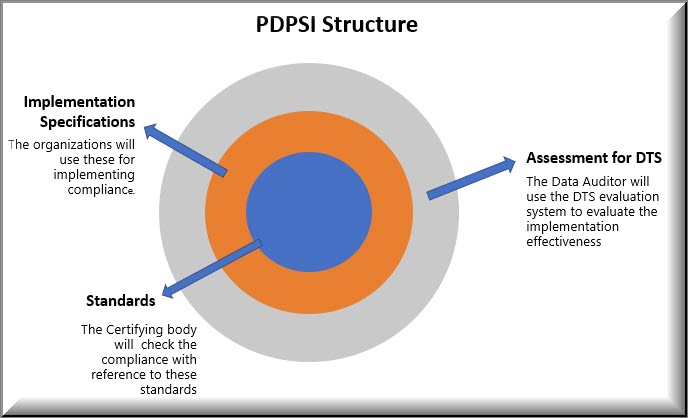
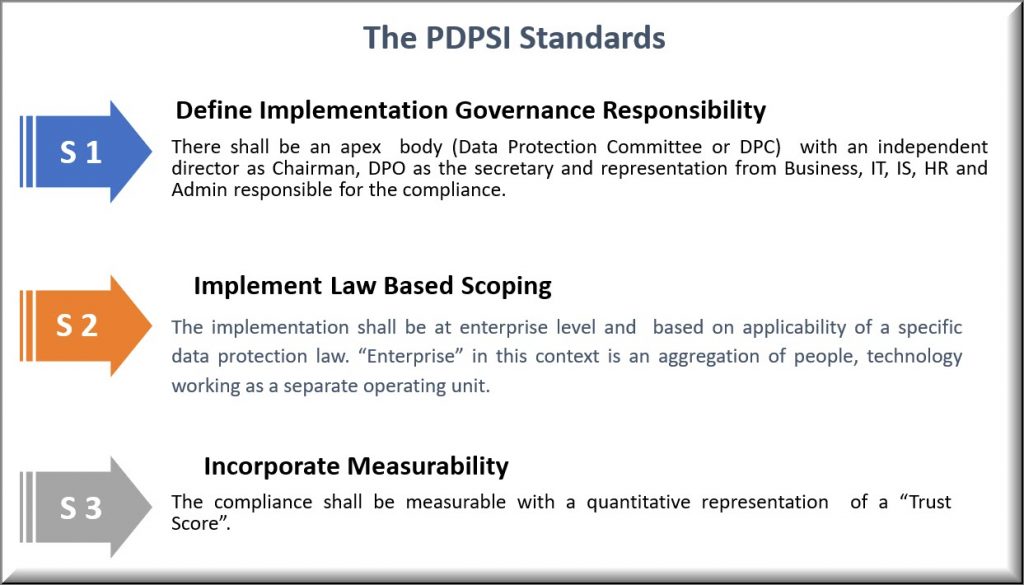
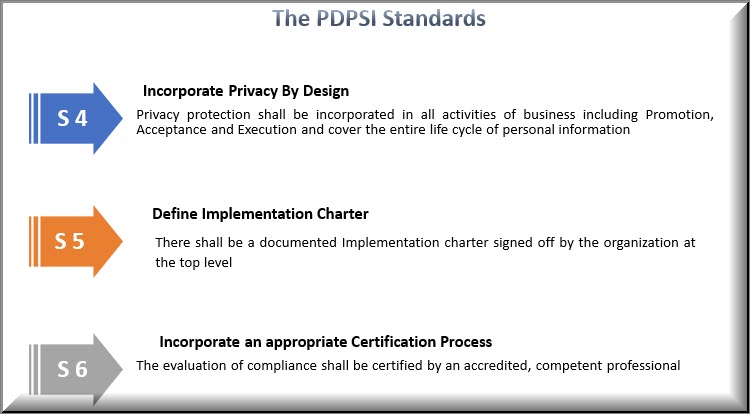
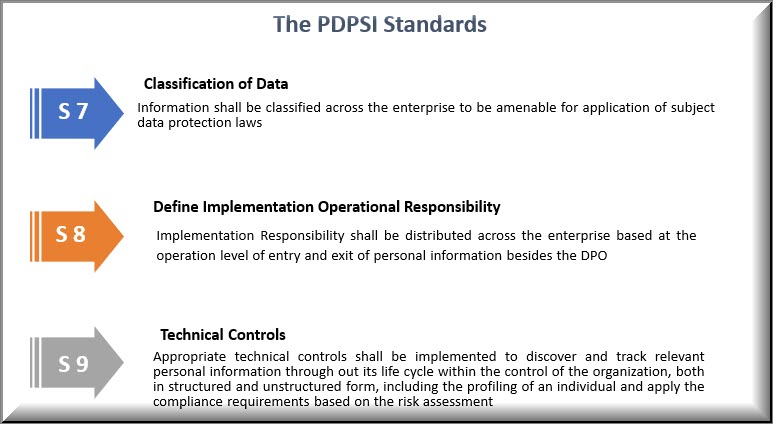
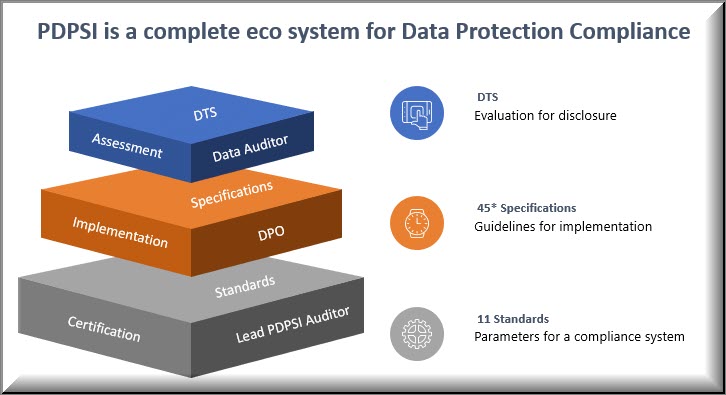
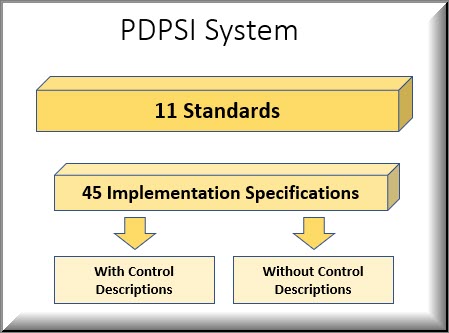
The Data Protection Compliance audit will be explored in detail using the PDPSI (Personal Data Protection Standard of India) framework .
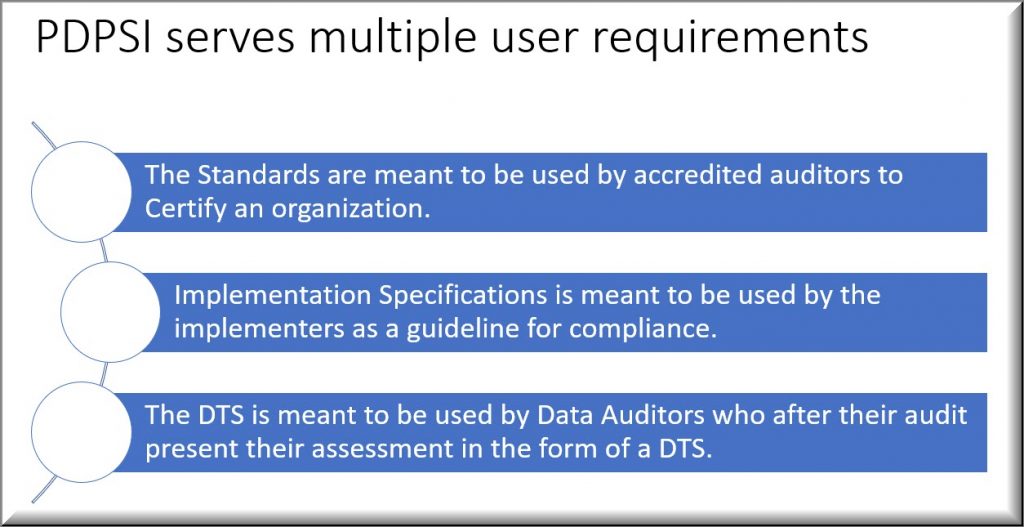
PDPSI is a framework for implementation and is also a Certifiable Standard of compliance. PDPSI is also a DTS assessment framework during the Audit process.
Foundation of Data Protection Professionals in India (FDPPI) is sponsoring the Data Protection Compliance audit under the PDPSI framework and this training is considered part of the accreditation of PDPSI Consultants and PDPSI Auditors who can provide consultancy to organizations on designing and implementation of Data Protection compliance programs as also to conduct Audits of such programs.
Consultation for implementation and Audit of the implementation will be undertaken by two different individuals.
While this Data Audit training may be considered mandatory for the Audit, implementation may be guided by the consultants. Organizations are open to implement the guidelines on their own and directly approach an auditor for Certification or take the assistance of consultants before approaching the auditors.
FDPPI may have additional criteria for accrediting auditors under their approved audit process for certification.
This Module-A training would be followed by an “Online Examination” and “Submission of Assignments”. 50% of the marks would be allocated for each of these two evaluation segments.
There will be three grades namely A, B And C.
Grade A: represents Ready for Audit
Grade B: represents Ready for Consultancy
Grade C: represents requirement of improvement
One Improvement re-examination will be permitted for upgradation of Grade C to Grade B.
According to the present scheme for accreditation of PDPSI Auditors,
FDPPI may accredit their members who pass out of this training with Grade A and have also passed out of the Module I and Module G program, as “Provisionally Accredited PDPSI Auditors”.
They may be upgraded into fully “Accredited PDPSI Auditors” after they complete the two other modules of the larger training program which includes the modules on Technology and Behavioural Skills.
FDPPI may also upgrade Persons who pass out of the program in Grade B “Provisionally Accredited PDPSI Auditors” based on their consultancy experience.
For registration for the program and kindly proceed to CDPP-Module-Audit”
The Date and time Schedule for the program is yet to be finalized. Tentatively the course should commence towards the end of January 2021 after the registrations close on 18th January 2021.
P.S: Though the training program is driven by the needs of the emerging Indian data protection law, the concepts discussed are universal and will apply even for compliance of GDPR and other Data Protection laws.
Naavi