-
Ask Vishy, the personal AI-assistant of Naavi for all your information on Naavi.org
Naavi

IICA Qualified Independent Director

-

-
DGPIN: 4PJ-7T8-FK8P: 12.94018310,77.55421020
-
Plus Code : WHR3+3P
Bing_site_search
Google_site_search
-
Recent Posts
Archives
Archives by Date
-
-
The 14 year saga of a Phishing Case reaches a significant milestone
November 9, 2022 was an important day when my 14 year old crusade for justice for S Umashankar who had lost money in a Phishing fraud at ICICI Bank reached a significant milestone. A judgement was pronounced by Madras High Court dismissing the appeal of ICICI Bank against the order of the TDSAT.
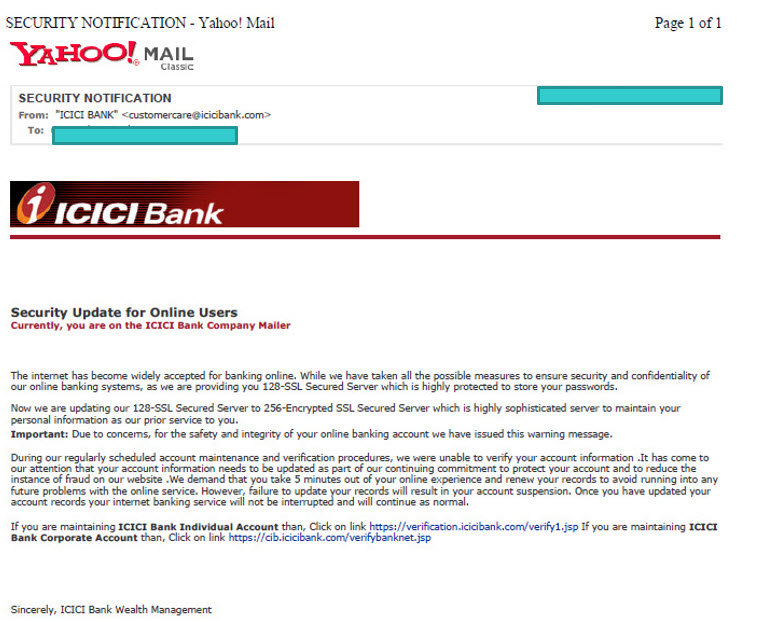
The episode started on 2nd September 2007 when the following e-mail was received by an NRI customer of ICICI Bank, Tuticorin. This was later identified as the phishing mail.
The mail had come from the same email from which the Bank was sending monthly statements and he considered it as having come from the Bank and proceeded.
(Though the customer was perhaps not aware, it was later pointed out in the Trial that the URL provided as the phishing link was a sub domain of ICICI Bank (https://verification.icicibank.com) which meant that the ICICI Bank server had been hacked and mail was being sent from there. Such hacking had been pointed out by Naavi.org earlier in one case of an educational institute.)
After the phishing mail having been responded, a sum of Rs 646000/- was transferred to a Mumbai Fort branch account of ICICI Bank in 6 transactions of Rs 1 lakh each and one of Rs 46000/- in quick succession on 6th and 7th September 2007.
ICICI Bank refused to accept its responsibility for the fraud and the customer approached the Adjudicating officer in Tamil Nadu through Naavi as a power of attorney holder and filed the application in June 2008. This was the first case for Adjudication in India.
After several rounds of enquiry, the Adjudicator gave a speaking order in 2010 awarding compensation to the customer.
ICICI Bank went on appeal to Cyber Appellate Tribunal and after a series of hearings, the case was posted for judgement and 3 days before the judgement the Chairperson attained super annuation and the case got stuck up till TDSAT took over Cyber Appellate cases in 2018. After several hearings TDSAT upheld the order of the Adjudicator .
This time ICICI Bank appealed in Madras High Court and the proceedings were held for about 2 years interrupted by the Covid and finally on 9th November 2022, the appeal was dismissed.
The case is considered historic as the first adjudication case and for the fact that Bank was held liable for negligence.
In both Adjudication, CyAT and TDSAT, the undersigned argued under a power of attorney.
In Madras High Court due to some technical issues, Naavi was recognized as a consultant to assist the Court and the arguments were finally made by an advocate Mr M A Ranganath.
Finally the Appeal has been dismissed and TDSAT judgement prevails.
We need to wait and see if ICICI Bank goes on an appeal to Supreme Court or closes its fight.
Under ITA 2000 adjudication is expected to be completed in 4-6 months and Appeal in the Tribunal in 6 months. But this case went for 12 years in Adjudication and CyAT out of which major delay was the non appointment of the Chair person in CyAT.
The case indicates the inefficiencies in the system which needs correction.
Since 2007 to this day, things have changed even in Banks and better security measures have been introduced. RBI has also introduced the Zero Liability system and very recently measures have been initiated to stop payment at the transferee Banks.
The recklessness shown by ICICI Bank in this case is beyond imagination and is a great example of what should not be done. It is a good case study for Bankers which should be used in Bank Training Colleges.
The case has already been part of examination question in some premier Law Colleges and it will be more often be used now after the High Court decision.
Naavi
Posted in Cyber Law
Leave a comment
Will EU generate another regulatory commotion in the world
When GDPR was introduced EU created so much fuss that it appeared that EU was making a law for the world. The extra-territorial jurisdiction was hyped up so much that Indian companies went into a shock from which they are yet to fully come out.
Subsequently the world was getting used to the GDPR when the Schrems Judgement and the following EDPB guidelines again caused a big stir on Cross border transfer of personal data.
The US Government under Mr Biden caved into the EU pressure and signed on the dotted line in the EU-US privacy agreement.
Now emboldened by the success of GDPR, EU seems to take yet another giant step in global Techno legislation through the Artificial Intelligence Act.
Copy of the Act is available here
The release of the draft Act has come when India is yet to finalize its version of the Data Protection Act and naturally there is a thought about whether any of the provisions of this Act could be included in the Indian proposed data protection Act.
The Tech giants raised a hue and cry when PDPB 2019 asked for Algorithmic bias audit. Probably they will go through this new law with care to see if it affects their business adversely.
The proposed regulatory framework on Artificial Intelligence with the following specific objectives:
-ensure that AI systems placed on the Union market and used are safe and respect existing law on fundamental rights and Union values;
– ensure legal certainty to facilitate investment and innovation in AI;
-enhance governance and effective enforcement of existing law on fundamental rights and safety requirements applicable to AI systems;
– facilitate the development of a single market for lawful, safe and trustworthy AI applications and prevent market fragmentation.
It may take a while for us to study the Act and comment but initial indications are clear that the law could be causing some discomfort to the Industry as well as the Government. Will it remain a small temporary disturbance or a major upheaval?…only time will tell.
The IDPS 2022 is likely to start a discussion on the Act on 11th November in one of the panel discussions.
Let’s look forward to the discussions…
Naavi
Posted in Cyber Law
Leave a comment
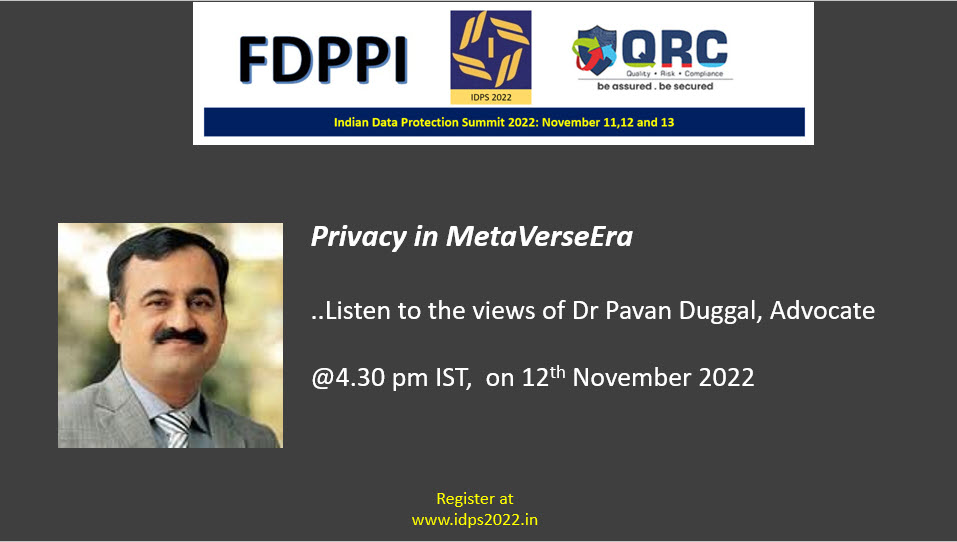
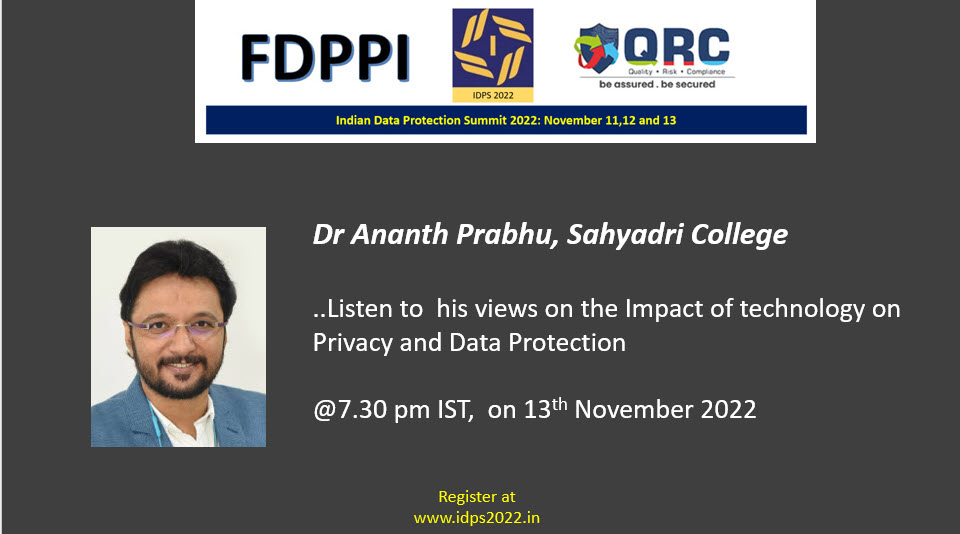
IDPS 2022… Unprecedented Rich Content
IDPS 2022 will be one of the richest Data Protection seminars/webinars to be held in India. Over 18 hours of content are planned to be delivered by experts between 2.00 pm to 8.00 pm on each of the three days, November 11, 12 and 13.
The webinar would be available on the virtual platform of ibentos..com.
Attendance is free but with pre-registration at fdppi.ibentos.com
Additionally more exclusive pre-recorded content would be available in the resource center. Some examples of content that would be available in the resource center are given below.
Bookmark this page and block your calendars. You cannot afford to miss this opportunity.
If you are an employed professional, ,it is time to inform your HR department and your boss that you need to take time off to attend to this webinar. The second and third days are weekends and you need to free yourself only from the afternoon of Friday.
Inform your colleagues also to attend and spread the word through your social media contacts. FDPPI is a not for profit organization and the seminar is offered free. All of you are our co-sponsors of the event and we request you to market the event to your contacts.
Naavi
Posted in Cyber Law
Leave a comment