Honourable Minister of State for IT, Sri Rajeev Chandrashekar has announced that the first draft of Digital India Act would be available for public debate by June 7.
Already, the Minister has conducted several public consultations on the general framework to be adopted by DIA. Naavi.org has also discussed the contours of the emerging Act in the following articles
- The New Digital India Act in the making-1 : Cyber Crimes under IPC?
- New Digital India Act in the making-2: Integrity of ChatGPT like models
- New Digital India Act-3 : Should the negative list be continued?
- Digital India Act-4 :Is there only one type of Intermediary in ITA 2000?
- Digital India Act-5: Adjudication
- Digital India Act-6: Fighting the Information Warfare
- Digital India Act-7: Data Monetization
- Digital India Act 8: Regulatory Oversight on PlayStore/AppleStore
- Digital India Act-9 : Digital Media Disclaimer
As we all are aware, the Digital India Act (DIA) is meant to replace the current comprehensive law namely the “Information Technology Act 2000” which has been amended substantially in 2008. The new DPDPB 2022 is an off shoot of Section 43A introduced in the 2008 amendment. There have been several CERT In guidelines and Intermediary guidelines that have also been released from time to time. A reasonable number of Cyber Crime cases have been investigated by the Police and several court decisions have also developed Cyber Crime jurisprudence.
If the new law in the form of DIA is introduced, there will be a substantial disruption to the understanding of Cyber Laws in India. We the professionals need to unlearn and re-learn several concepts.

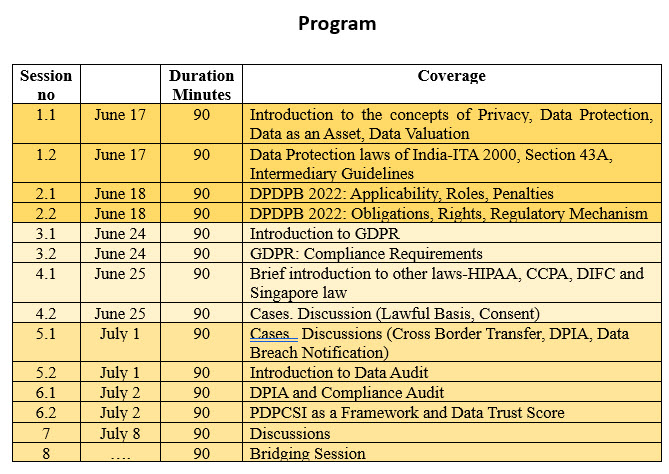
In order to prepare the Cyber Law Professionals for the upcoming law, Cyber Law College of Naavi is starting a new Course on “Certificate in Cyber Laws ” . This course will have two parts. The first part will cover the current laws. The second part will cover the proposed DIA in whatever form will be available in the month of June. If the Government provides a copy of a draft Bill, the Course will cover a discussion of the Bill section by section so that professionals will be able to participate in further discussions and understand the emergence of the law with a close observation of the debates that would take place later.
If the new Bill is not introduced, we will discuss the draft as is present now and covered over several articles indicated earlier.
The motto of Naavi/Cyber Law College is to enable Cyber Law Professionals to be Ready before others so that you can keep up the Knowledge leadership.
The full details of the Course for Part I is available below:
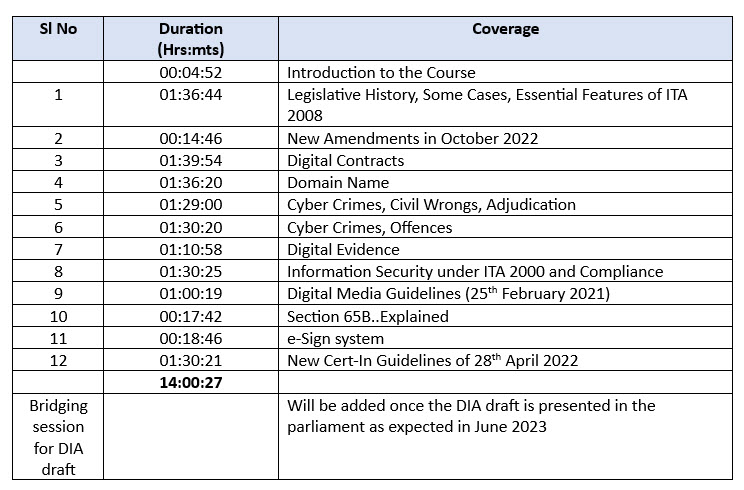
Part I of the program consists of 14 hours of online sessions available at present. This will be supplemented with the Bridging Session the duration of which will be decided based on the requirement.
The recorded programs can be completed in about 1 month. Once the new Bill is available, the schedule of live sessions for DIA would be announced. Since Naavi has also scheduled a course on “Certified Data Protection Professional” starting from June 17 as a week-end program, the DIA course will be scheduled during the week days at about one hour per day for which a schedule would be announced later. If the Government does not present the draft Bill, the Bridging session may be a short session.
Registration for this course is now open. The fees is a moderate Rs 6000/- (inclusive of GST). Participants can complete the course and obtain a participation certificate. They will also be provided an option to take an online proctored examination and if successful they would be provided with a Certificate as “Certified Cyber Law Professional (DIA)”.
Since this program is now under the umbrella of FDPPI certification, details are also available here. Kindly register only in one place.
Naavi