 During October 2019, a “New Theory of Data” was presented in these columns. The objective of the theory was to bring a common ground of understanding between the Privacy Activists who are leading the passing of data protection regulations in India, the Technologists who are racing ahead with AI based consumer profiling and Big Data Analytics and the Business Entities who are building profitable commercial propositions with “Data and Personal Data” being the raw material.
During October 2019, a “New Theory of Data” was presented in these columns. The objective of the theory was to bring a common ground of understanding between the Privacy Activists who are leading the passing of data protection regulations in India, the Technologists who are racing ahead with AI based consumer profiling and Big Data Analytics and the Business Entities who are building profitable commercial propositions with “Data and Personal Data” being the raw material.
Resolving the differences in the perspectives of these three segments of stakeholders is an essential part of bringing in a legislation which will be acceptable to a majority of people.
We already have stiff opposition from some business entities on at least one of the aspects of the legislation namely the “Data Localization”. There will be other entities like the “Digital Marketing Industry” which may have some conflicting views to be accommodated. Similarly, framers of the draft law of DISHA for the health sector have already expressed some contradictory views of their own. We therefore need to analyze the personal data protection bill when it is debated in the Parliament to discuss how it will satisfy the views of the different stakeholders.
While doing so, we shall also make a comparison with the New Theory of Data and see if some of the conflicts get a better clarity when the new theory is applied to the understanding of the data whose protection and governance we are trying to regulate through PDPA 2018 (whatever version that emerges in the parliament).
The New Theory of Data propounded three principles as three different hypotheses.
First was that “Data” is constructed by “Technologists” brick by brick through binary notations. But what we the humans understand as “Data” is an interpretation of the binary notations seen through a computing device with appropriate software applications. The human interpretation of data being dependent on the technology devices may give different experiences to different people both because the interpreters may be inconsistent as well as the person looking at the data interpretation may himself be inconsistent with his interpretations.
The very concept of “Privacy” is a concept that tries to understand the “State of Mind” of an individual. This “State of Mind” is dynamic and inconsistent. It differs from person to person and within the same person from time to time. But we try to formulate one single law that applies to all people for all times to protect their “State of Mind”. The legislation therefore has a huge challenge in bringing in “Flexibility” along with a ” Well defined Framework of Principles and Rights”.
Such flexibility needs to be available to the Data Subject (Data Principal) at the time of providing “Consent” where different persons should be able to provide different consents to suit the different purposes. The flexibility should also be available to the Data Processor at the “Data Management” stage where the Data Processor complies with various provisions of data security, data disclosure, data breach notification, etc.
To enable a smooth compliance of the regulations, the regulators need to understand that “Data” assumes different dimensions in the hands of the data processor depending on the applied human perspective and undergoes a “Reversible Life Cycle” where it exists in different states from its birth when the first binary set which forms one element of the data becomes available to the organization. This could be the “name” or the “E Mail address” or the “IP address” etc.
This single data set then combines with other data sets and forms the composite data sets such as “Name with E Mail Address”, Name with E mail address and Aadhaar number” etc. The regulations need to recognize this transition from “Unidentified data” to “Personal Data” to “Sensitive Personal Data” etc along with the possibility of a reversal through de-identification and anonymization.
An irreversible “Destruction” ends the life cycle of data within an organization when the data is disintegrated into individual binary elements and forensically jumbled up so that they become one with the “two elements” (The Zero and One) in a chaotic arrangement that provides no meaningful data to a human being.
These concepts of the New Theory of Data has to be consistent with PDPA provisions of definition of “Anonymization”, “Personal Data”, “Non Personal Data”, “Community Data”, “Corporate Data”, etc.
Similarly when a Data Processor applies his technology and creates a value added product from the basic raw data, there needs to be a recognition of the “Additive value theory of ownership” where each person/entity who operates on the data during its life cycle and builds value to the data entity is credited with ownership for the value addition.
At the same time if the Data Principal wants to retain his right over the value addition, it has to be enabled through the mechanism where by the consent itself recognizes that the right on the value addition part is retained with the data principal or transferred to the data processor for a consideration.
We must recognize how the California Consumer Privacy Act (CCPA) clearly recognizes the “Right to Sell personal data” where as the GDPR is being interpreted as a more rigid regulation where “Selling of personal data is a taboo”.
We need to see how the Indian law will be interpreted.
Will it take the left extremist view like the GDPR where Controller determines the means of processing based on a defined lawful basis ?or
the Right extremist view where the Data Fiduciary has the right to take decisions in the interest of the Data Principal? (like a “Mutual Fund Manager or a Portfolio manager taking investment decisions for a client”) or
A “Centralist View” of a “Purpose Specific Consent” determining whether a personal data can be sold, transferred, disclosed etc for consideration?
needs to be watched.
Let Cyber Jurisprudence on the role of Data Fiduciary on whether he is a “Controller” or a “Trustee” be developed through the debates that follow. This will be the first of the prominent principles that needs to be established in the course of time.
Naavi
Reference Articles
The Theory of Data
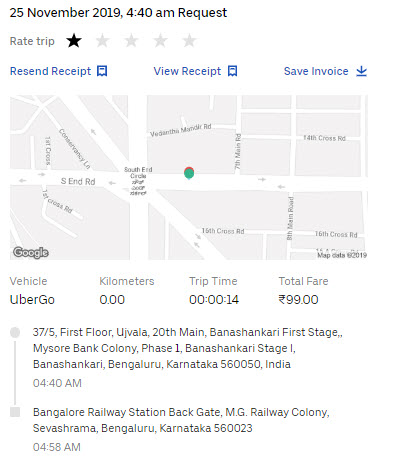 The first picture here was taken from the Uber website and indicates in the billing that I have travelled from one place in Bangalore 560050 to another place in Bangaore 560023.
The first picture here was taken from the Uber website and indicates in the billing that I have travelled from one place in Bangalore 560050 to another place in Bangaore 560023.


 During October 2019, a “New Theory of Data” was presented in these columns. The objective of the theory was to bring a common ground of understanding between the Privacy Activists who are leading the passing of data protection regulations in India, the Technologists who are racing ahead with AI based consumer profiling and Big Data Analytics and the Business Entities who are building profitable commercial propositions with “Data and Personal Data” being the raw material.
During October 2019, a “New Theory of Data” was presented in these columns. The objective of the theory was to bring a common ground of understanding between the Privacy Activists who are leading the passing of data protection regulations in India, the Technologists who are racing ahead with AI based consumer profiling and Big Data Analytics and the Business Entities who are building profitable commercial propositions with “Data and Personal Data” being the raw material.








