Evolution of the Term “Data”
Before the advent of ITA 2000, the normal understanding of the term Data was information in raw form. Data organized in a form in which it carried better use to the community was termed “Information”.
Data as Experience
With the advent of the ITA 2000, the meaning of the words Information and Data changed. Both were “Streams of binary states” of a magnetic or optical surface which was capable of being processed by a computing device, the purpose of such processing being converting the binary stream into a human intelligible experience.
Data was therefore an “Experience” delivered to a human by a computing device from a stream of binary notations contained in some device.
The device in which the binary stream was contained was called the “Container of Data”. The hard disk or the CD are examples of such “Containers of Data in binary form”. This binary form of data could be read only by machines which included the hardware and software like the computer, the application software etc. In order to enable the computer to render the binary stream into text or sound or image, the core element of the data had to be padded with header information that contained the instructions on how to “Experience” the data with the use of the appropriate computing device.
We may note that an Encrypted data or data read through the incompatible devices may come up as an unreadable gibberish or even corrupted data but it is still “Data” for the technical purpose though it is a “Meaningless junk” for the human purpose.
This “Data as Experience” was the central idea for which in the Indian Evidence Act, a section called Section 65B was introduced making it mandatory for every electronic evidence to be accompanied by a certificate from a human being for it to be admissible in a Court stating “What” and “How” he experienced the said data which is the evidence in a subject incident.
Arrival of Data Protection Regulations
With the arrival of the Data Protection Regulations in India first with ITA 2000 and more specifically with the amendments of 2008 and later the GDPR and PDPA (Bill under consideration), the debate on defining the term “Data” in the context of “Personal Data” got more intense. The regulation focused on “Personal Data” (PD) and Sensitive Personal Data (SPD).
Today, whenever we speak of “Data” we are mostly discussing “Personal Data” almost forgetting that there is data beyond “Personal Data” which also needs to be processed, protected and used productively. Those who called “Data as Oil” had this entire data set in mind where as those who called “Data is water” had the Personal Data in mind.
Debate on Non Personal Data
Privacy Laws are directed towards protecting the Privacy Rights of “Living Individuals” and hence data belonging to a Corporate/Organziational entity was outside the provisions of the data protection regulations. However Data of Corporates always continued to be the subject of Cyber Crime regulations such as ITA 2000/8 or Computer abuse regulations or Digital Contract related regulations.
Now the discussions on “Non Personal Data” has surfaced with a greater intensity since there is a possibility of a new regulation in India exclusively for regulating “Non Personal Data”.
This law may be called “Data Governance Act of India” (DGAI) for our discussions.
Apart from covering “Non Personal Data” which is part of data covered under the ITA 2000/8, the new regulation is likely to introduce new terms such as “Joint Personal Data”, “Community Data”, “Anonymized Data”, “Business Data” etc.
For those who were fully engrossed in GDPR discussions without taking into account the “Data beyond the Personal Data”, the new terms and categories of data will not be easy to absorb.
While the Data Protection Professionals keep struggling with issues such as
-Whether Business E-Mail is personal data?
-Whether Big Data is regulated under PDPA or the Data Governance Act?,
-Whether Community data is the property of the community as a whole or is a joint and several property of each of the community members,
-Whether an E Commerce data of an individual belongs to the individual or the E Commerce company,
-Whether a ML process generates a profiling algorithm which is the intellectual property of the Company or the individuals (or the community), etc
the new category of professionals namely the “Data Governance Managers” will emerge from the Business Schools and start demanding interpretations on
-What is Data?,
-Whether Data is “Property” or Right”?
-Whether Data Fiduciary is a contractual servant of the Data Principal or a Trustee of the Data Principal,
-Whether Data is an Asset of the organization and has to be deployed productively to a higher yield in terms of revenue
-How risks of non compliance can be transferred with “Cyber Insurance” after the Data Protection Professionals have mitigated it to a certain extent,
-Whether the “Risk Mitigation” is a residual effort after Risk Avoidance, Risk Transfer and Risk absorption? or Risk Absorption is the residue after Risk Avoidance, Risk Mitigation and Risk Transfer?
-Whether the Data industry would be able to meet the Cyber Insurance regulations of “Contract of utmost faith”, “Co-insurance”, “Expected Protective Action as if no insurance is available”, “Whether Extortion and Zero day vulnerabilities are insurable”? etc
Naturally the views of a management professional will be different from an IT professional or a legal professional. Hence there is bound to be some disagreements and heated debates within the corporate circles on fundamental aspects of Data Protection and Data Governance.
It is therefore vital that we continue to keep boiling the academic debate on the subject of Data and what is meant by Data Governance and how does it differ from Data Security and so on. We may thereby contribute towards better clarity of the subject.
In the past, as an academician, Naavi has tried to describe Privacy and Data Protection from different perspectives. We have tried to look at Privacy Protection regulations from the Johari Window concept, Looked at Data as a “Dynamic Concept” etc.
In this direction, let us today explore another perspective of “Data” and “Personal Data” from the vision of “Nuclear Physics” and see if we can get a better hang of the complex concept called “Personal Data” which we need to regulate as if our life depends on it.
Some of the issues that we need to discuss here are
1.Is “Data” actually is a “Data Set” consisting of multiple sub elements like an “Atom” consisting of “Protons, Neutrons or Electrons”?
2. What will be impact on the human being in his experience of the “Data” when different “Elements of Data” come together, or When some elements of data are removed from a data set,
3. Will in such occasions, when a data set undergoes a fission or fusion, the value of the data as an experience increase or decrease,
4. Will the ownership of the data change during this process of mutation?
5. How the laws of data governance handle the concept of “Data as Experience undergoing mutation due to environmental aspects in which different stakeholders have contributed differently”
We therefore need to take one more look at the “Data” and try if we can understand its nature better.
Continued…..
Naavi
[P.S: Why this “Nuclearaization” of “Data Concept”?…
Naavi was a student of Physics at one point of time and was always fascinated by the fact that Internet was actually discovered in a Physics Lab. We observe that the entire domain of Computers is directed by the “Transistors” who in their miniature form become “Chips” and carriers of data and computing instructions. This is a derivative of the branch of science called Physics.
The Quantum Computing has already taken the data holding space to nuclear and sub nuclear particles. The law of Electronic evidence can only be explained through data being represented by the binary states which are the states of the transistors or electromagnetic orientation of particles in a container.
Therefore it seems logical that even the concept of “Data” and its classifications into different forms for data protection is also explained in terms of the concepts of nuclear physics”. This should also in a way establish the role of the students Physics who have strayed into the domain of “Data Protection” who have to often face the question of “What are you doing in this field of lawyers and engineers?”, and establish the “Oneness” of different fields of science.
Naavi]


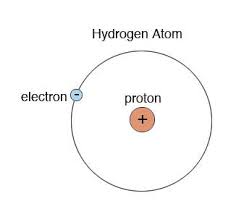 In comparison, a Helium atom is heavier with two protons and two neutrons in the nucleus with two electrons revolving around the nucleus.
In comparison, a Helium atom is heavier with two protons and two neutrons in the nucleus with two electrons revolving around the nucleus.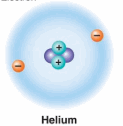 Hydrogen and oxygen combine together they may together form a liquid called water. Some of the molecules may be so tightly bound that they even become solids.
Hydrogen and oxygen combine together they may together form a liquid called water. Some of the molecules may be so tightly bound that they even become solids.







