PDPSI (Personal Data Protection Framework) is one of the suggested frameworks for compliance of the data protection regulations, like the BS10012 or ISO 27701.
PDPSI framework tries to address the requirements of the Data Fiduciaries/Data Processors incorporating all the best practices under the international frameworks and extending it to meet some of the difficulties that are encountered by the implementing agencies.
In this article, I try to explain a few concepts which are necessary to adopt PDPSI framework for compliance of data protection regulations. (Please refer to www.pdpsi.in where there are many other articles on the framework)
Naavi
We often use the terms Data Protection and Information Security as synonyms. However with the advent of strong Personal Data Protection regulations like the GDPR and the forthcoming Indian PDPA, there is now a need to distinguish the terms Data Protection and Personal Data Protection. If we would like to use the term “Data Protection” only in the context of “Personal Data Protection”, then we should use the term “Information Security” for referring to “Protection of Non Personal Data”.
We should adopt this convention and also distinguish the two terms in terms of implementation of any compliance requirements.
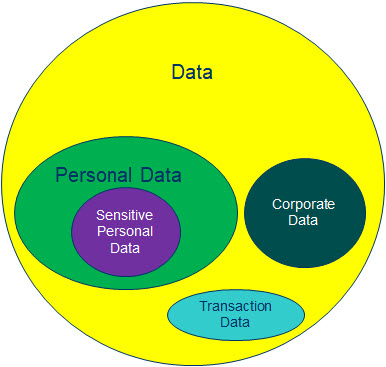
“Data” is generally recognized as an “Asset” of an organization. It is often generated within the operations of the organization and some times acquired at a cost.
The Objective of any commercial organization is to earn legitimate profits in business by using its assets. Hence companies which want to use Data as a raw material for their business activity are well within their rights.
While processing “Data”, the organization has to recognize that the subset “Personal Data” requires a separate treatment because it has to be compliant with the applicable laws.
“Personal Data” is like the hazardous inventory that an Inventory Manager has to confront with, storing and processing of which requires the special knowledge of the data protection laws. It is for this reason that while the CISO handles the responsibilities of securing the Data asset in an organization and a Data Governance Manager/Officer (DGO) handles the responsibilities of ensuring the productive use of Data asset of an organization, the Personal Data Protection Officer (DPO) is assigned the special role of protecting the Personal Data which is in the custody of an organization.
While the DGO and CISO handle the “Non Personal Data” from the management and security perspective, the DPO needs to handle the “Personal Data” both from the point of view of management and also from the point of view of security.
The DPO will determine how productively personal data can be used and also how to secure it as per the law. Since the processing of the personal information should conform to the requirements of the relevant data protection regulation, a proper compliance of this provision requires
a) Classification of data as Personal data
b) Identifying the purpose of processing
c) Identifying the lawful means of processing
The Data Protection laws place a high reliance on the “Informed Consent”. But at the same time, they also recognize that some times, obtaining “Consent” may be practically not feasible and in such cases factor in exemptions and derogations. Additionally emergencies and public interest also have to be recognized.
Beyond all these lies the concept of “Legitimate Interest of the Data Fiduciary/Data Controller”.
While “Purpose” is the end objective of processing, “Means” is the path through which the objective is achieved. In the context of Data Processing, Purpose and Means are closely related and often used synonymous.
In view of the different purposes of processing permitted under the data protection laws, the Data Fiduciary/Data Controller can use an appropriate means of processing of personal data which may fall into any of the 5 categories indicated in the following diagram.
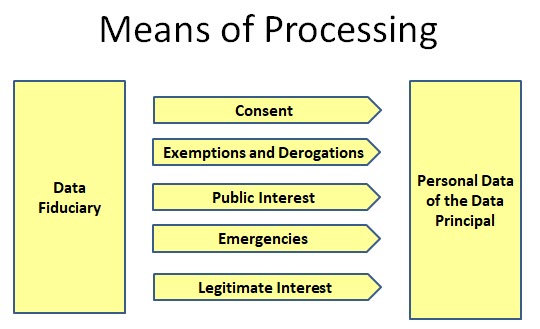
Purpose of processing which is “Unlawful” is obviously out of consideration of a Data Fiduciary.
Those purposes of processing which are not covered by the exemptions and derogations and are also not covered under the consent or emergencies have to be considered under the “Legitimate Interest of the Data Fiduciary”.
Any other purpose would be considered as “Non compliant”.
The management of the “Legitimate Interest” of the organization in a manner in which personal data remains to be productive without increasing the risk of non compliance of data protection regulations is the challenge that the DPO has to handle.
However, the DPO has to appreciate that most data protection laws try to draw a line between “Legitimate Interest” and “Harming the Privacy Right of Data Principals(Also called Data Subjects)”. The boundary of the legitimate interest argument is the unacceptable harm caused to the data principal.
One extreme view of Privacy activists has always been that “Privacy is Paramount”. If this argument is accepted then there is “No Legitimate Interest argument”. Either there should be a public duty or legal compulsion of some sort (which includes the self legal defense) or there should be a “Consent”.
However, as long as the term “Legitimate Interest” remains in the legislation (Both GDPR and PDPA use this term)
GDPR recital 47 states
“The legitimate interests of a controller, including those of a controller to which the personal data may be disclosed, or of a third party, may provide a legal basis for processing, provided that the interests or the fundamental rights and freedoms of the data subject are not overriding, taking into consideration the reasonable expectations of data subjects based on their relationship with the controller….
the existence of a legitimate interest would need careful assessment including whether a data subject can reasonably expect at the time and in the context of the collection of the personal data that processing for that purpose may take place…
The processing of personal data strictly necessary for the purposes of preventing fraud also constitutes a legitimate interest of the data controller concerned…
The processing of personal data for direct marketing purposes may be regarded as carried out for a legitimate interest.”
The Indian PDPA as proposed indicates under Section 22(d) that every data fiduciary shall indicate the legitimate interest in the Privacy by Design policy which is approved by the DPA and hence becomes an “Approved Objective of Processing”. The Indian law has reduced the uncertainties between what the Data Fiduciary may consider as the “Legitimate Interest” and what the privacy activist may consider as an “Intrusion of Privacy” by bringing in the concept of “Privacy By Design Policy” which is a document that is filed with the DPA at the time of registration of a Significant Data Fiduciary.
In the light of the above, let us now introduce how PDPSI tries to address the legitimate interest of a business.
PDPSI differs from other frameworks such as ISO27701 or BS 10012 as it tries to bring in a concept of ” Unified Data Protection Program”. Both ISO27701 and BS 10012 address the PIMS for GDPR. PDPSI on the other hand addresses PIMS for PDPA-India, GDPR-PDPA-Singapore,CCPA, Dubai DPA, UK DPA., etc. It is a single framework which branches off into individual compliance requirements. It also encourages the technical architecture that supports the need for multiple data protection requirements.
The identification of what falls under the “Legitimate Interest” is the responsibility of the apex Governance committee for Personal Data Protection. This apex committee which may be called by names such as the Personal Data Protection Committee or by any other name should have representation of
1) At least one Independent Director of the Company
2) The CEO
3) The DPO
4) The CISO
5) The CTO
6) The CCO
7) One or more Business managers
8) HR Manager
9) Data Governance Manager (if any)
The designation of a DPO without conflicting responsibilities and constitution of this committee is an essential starting point for compliance of PDPA and PDPSI places a significant weightage on this aspect.
In the committee, proposition of what should constitute the legitimate interest of the organization beyond what is otherwise permitted should be discussed and approved into the charter of implementation.
As a process,
the legitimate interest discussion stems from a business proposition by the Business Manager that is converted into a technical process by the CTO and approved by the CISO but objected to by the DPO.
The DPO may raise objections for the reason that the identified process and the purpose may infringe on the Privacy rights of a data principal.
The Committee has to deliberate and arrive at a consensus on why the suggested process is necessary for the business and what safeguards can be introduced based on the suggestions of the DPO.
Following this, the process will be part of the Privacy By Design Policy or a DPIA and in both cases, Indian law envisages an approval from the DPA. If the DPA suggests any modifications, the process has to be discussed once again and approved.
The DPO on his own may have to refrain from a unilateral decision since the determination of the legitimate interest has an impact on every other business functionary and should carry the concurrence of the top management.
We shall explore more on how PDPSI achieves this unified data protection implementation in the follow up articles.
(To Be Continued)
Naavi









