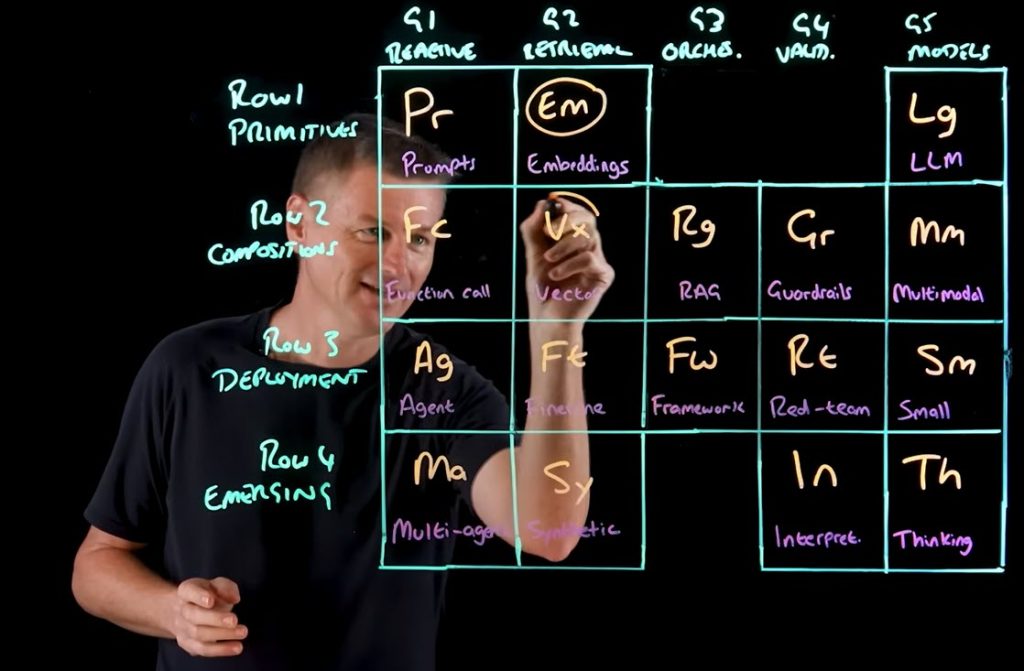
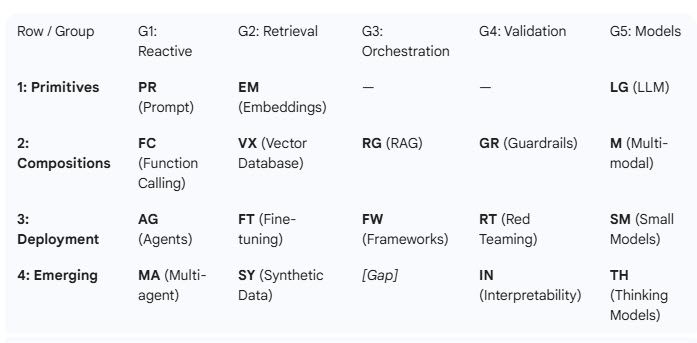
As India prepares for the DPDPA Era, it has become necessary for organizations to explore the technical tools required to work towards compliance. FDPPI has already unveiled the Compliance frameworks, conducted many awareness sessions and also created many certified professionals.
It is time now to move to the next level of assisting the industry for compliance with assistance to understand and evaluate technical tools necessary for DPDPA Compliance.
It is natural that all existing international software solution providers who are already in the game serving the GDPR community are now eyeing the “Big and Beautiful Indian market” which is “Tariff Free” and are tweaking their software to meet DPDPA requirements. Some of them are opening Indian subsidiaries to give their software a local touch.
Many Indian start ups are also venturing into the development of software for DPDPA Compliance including the Six shortlisted companies which are into the final round of development of the open source “Consent Management” software in the Coding Challenge.
Many large entities are however not relying on the external software suppliers and are developing their own in-house software for compliance .
Already many of the professionals in the organizations have started gathering data and taking presentations from the vendors. Those who were already using some international products are experiencing the customization for DPDPA.
We as a community of Data Protection Professionals need to understand where the industry stands as of today, who are the serious players and what are their offers and what is the experience of the early users are. We know that these are early days and experience is sketchy. Many have only the marketing presentations to depend for their understanding. But this is early 2026 and we need to make an assessment of what do we have today.
FDPPI has therefore launched the country’s first survey of DPDPA Compliance tools as a perception study from the users.
The Indian National Survey of DPDPA Compliance tools is an initiative launched by Naavi and FDPPI as a part of the celebration of the International Privacy Day of 2026.
The survey is now open and over the next one month till end February 2026, will collect the data. It will then be analysed and a report would be prepared.
Your views will be consolidated and all respondents will get a copy of the final report if they have shared their contact e-mail in the form
The tool manufactures can participate in the survey identifying their role as vendors of solutions. FDPPI would also give a one hour slot to them to present their software in one of the Jnaana Vardhini Sessions to the members of FDPPI if interested.
Naavi