PDPSI is the Personal Data Protection Standard of India developed by Cyber Law College as an open standard framework for Personal Data Protection particularly in compliance with the proposed Indian Personal Data Protection Act. Naavi has been explaining the different concepts of PDPSI through the articles in Naavi.org also collated at www.pdpsi.in.
Professionals working in the field of Information Security are used to the format of a framework followed by ISO and it is difficult to make them look at any new framework unless it is explained with reference to the known frameworks. Hence it would be necessary to explain the PDPSI framework with reference to ISO27701 or its predecessor BS 10012. However, Naavi urges professionals to look at PDPSI independently without being too much clouded by their experience with the ISO frameworks.
PDPSI is meant to be an open standard document unlike the mesh of proprietary standards that are used in the ISO framework. It is our belief that what is a “Standard” should be for the benefit of the society and such standards should ideally be open standards. Professionals can still make money out of the standard in the form of implementation consultancy since any standard will require interpretation by an expert and adoption to a given context. This give enough room for our professional income generation rather than milking the standard itself for our revenue.
Today we shall highlight the special feature of this framework that extends beyond PDPA compliance into the domain of GDPR compliance.
The PDPSI framework is built on the following five key boundary implementations
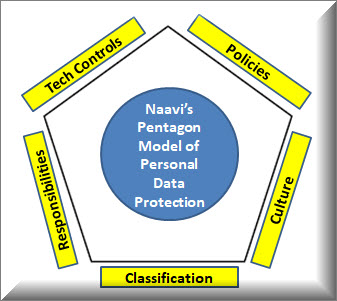 namely Classification, Distributed Responsibilities, Development of the PIMS culture, supported by the policy documents and technical controls.
namely Classification, Distributed Responsibilities, Development of the PIMS culture, supported by the policy documents and technical controls.
“If I certify for ISO 27701, will I be considered certified for GDPR?”.
Most professionals who look at ISO 27001 try to map its controls to GDPR and the frequent question we receive from IS professionals is that “If I certify for ISO 27701, will I be considered certified for GDPR?”.
A similar question has been raised in India also regarding ITA 2008 compliance with reference to ISO 27001. It is a history now that Naavi vehemently opposed the MeitY when it was working under Kapil Sibal that the Government of India should not give an impression that being ISO 27001 certified is deemed compliance of Section 43A. Though the department gave some vague answer as follows:

This was in reference to the rules under Section 43A notified on 11th April 2011 (Refer details here)
Despite the clarification, the MeitY has done nothing to expel the general impression in the community that being ISO 27001 certified is deemed compliance under ITA 200/8. ISO organization (which is not a Government body ) made full use of the misconception in marketing its certification in India.
Now there is a new attempt in the international scenario to project as if Certification for ISO27701 is deemed compliance of GDPR. In future this argument may be extended to “Deemed Compliance under PDPA” and hence this has to be flagged here and now.
It is important for professionals to realize that ISO standards are industry best practice standards and though they go a long way to meet the requirements of the law, the compliance to a data protection law is independent of the certification under an industry standard.
The same principle applies to PDPSI also when it is used as a means of compliance to either PDPA or any other law. Irrespective of the framework used, the data protection authority has a right to ask for a separate “Data Audit” or “Data Breach Audit” or “harm Audit” or a “Data Protection Impact Assessment” and ignore the certifications.
Hence let us first make a categorical statement that being certified under ISO 27701 (or PDPSI-GDPR being discussed here) is not to be considered as “Deemed Compliance” to GDPR.
Now we shall proceed further to discuss what is PDPSI-GDPR?… in the next article.
Naavi







