(Continued from the previous article)
The initial reactions from the market on the IRCTC tender document which spoke of appointing a consultant to study and implement a “Data Monetization” policy was to suggest as if IRCTC is about to loot the public and infringe on the privacy rights in a big way. Simultaneously there were a few reports to suggest that IRCTC will backtrack and withdraw the proposal because of the criticisms.
In the past IRCTC has been accused of not adopting adequate information security on its ticket reservation platform and using excessive advertising to the extent of annoying the users. A few articles have also been written in this website on these issues.
However that does not mean that IRCTC should be blindly criticised for their latest move in trying to create higher value out of its data assets. As long as the “Data Monetization Program” is handled without a marginal adverse effect on the customers of IRCTC, there should be an open mind to appreciate that there has been a recognition that certain assets of the organization which have a value can be re-valued and used in a better manner to generate more revenue.
It is fine to flag the Privacy infringement risks but there is a need for critics to study the intentions as expressed in the tender document, and thereafter follow the implementation plan to raise their objections to the next level.
We would also like IRCTC to not chicken out like the UIDAI (in withdrawing its tender for monitoring social media) or the Government in withdrawing the farm laws. Instead they should stand and fight the opposition in cases like the Agniveer scheme. If there intentions are honest, they should not cave in for the criticism which will only embolden the critics for further such attacks to prevent the Government from introducing any progressive measures.
We have appreciated the Indian Railways when they have expressed plans to generate solar energy by planting solar panels on train tops, convert bogies into mobile hospitals during Covid time etc. Similarly any other innovative measures to use their data assets and generate more revenue is not to be opposed per-se.
Naavi has been advocating that “Data Valuation” and “Bringing Visibility to the Data in the financial statements” of an organization is required and we have added it as one of the suggested Data Protection controls under the DPCSI (Data Protection Compliance Standard of India). We have discussed this topic extensively both under Naavi.org as well as under the separate website www.dvsi.in .
(please also refer this article or to the video available here)
We therefore look at the IRCTC projects with an open mind and look at what are the positives behind this tender. We reject the hypocrisy of critics who accept the private sector’s attempt to monetize the data surreptitiously and raise public money through IPOs and the dubious records of some organizations which opposed the data protection bill till it was withdrawn and are now using the withdrawal of PDPB 2019 as another ground of criticism. The same critics also objected to the provision in PDPB 2019 which empowered the Government to pick up anonymized personal data from private sector companies for public good though they were aware that the private sector companies were collecting and monetizing personal data in violation of all known norms.
The subject tender document indicates two projects.
Under Project A, the objective is “To study monetization of digital data of Railways” . In this project the Railways will share the kind of applications they use and the type of data collected so that the consultant can understand the data environment and identify the potential value of the data collected and how they can be leveraged. At this stage there is no need for the consultant to access real personal data except for testing purposes.
IRCTC can “Pseudonymize” the personal data even for testing purpose so that “No harm” is caused to the passengers due to any activity that arises from this tender.
The tender document specifies that the study shall be conducted in compliance with laws including ITA 2000 and its amendments as well as the Personal Data Protection Bill 2018 of India.
We may point out that they could have mentioned the JPC vetted PDPB 2019 instead of PDPB 2018 though the justification could be that PDPB 2018 is a draft owned by the Justice Srikrishna Committee and cannot be questioned on political bias.
The deliverables under the project are creation of a framework for using the data and crating a monetization strategy.
What IRCTC has set out to do is what every “Data Driven Business Organizations” needed to do immediately after Kris Gopalakrishnan committee gave its report on “Non Personal Data Governance Framework”. This committee suggested that organizations need to recognize “Data Business” within their activities and generate a recognition of “Data Assets”.
We have earlier pointed out two incidents in USA where data valuations have prevented companies from declaring insolvent and two cases from India where lack of data valuation resulted in one company being declared insolvent and another company selling valuable national assets to a foreign agency without any record of consideration collected. Briefly the incidents are discussed below. There could be many more such incidents which we may not be aware.
1.Case of United Airlines and American Airlines
United Airlines collaterised its passenger data held in the “Milege Plus” scheme (loyalty scheme) which was valued at $20 billion at a time its market capitalization was at $ 9 billion.
Similarly, American Airlines valued its loyalty scheme data of “AAdvantage” at $19.5 billion when its market capitalization was $8 billion
2. Caesar Entertainment Operating Corp
Creditors of this company encashed its Total rewards customer loyalty data base for over $1 billion which was more than the value of Ceaser’s Property.
3. Case of Net4India.com
Net4india.com was the leading domain name registration company in India which the NCLT declared as insolvent because of their inability to repay Rs 100 crores of borrowings from SBI. In the process, NCLT failed to recognize the presence and value of data assets worth far more than Rs 100 crores and let the company be closed liquidating the real estate and causing losses to more than 3 lakh customers of Net4India. (Check out for details here)
4. Case of CIBIL and Trans Union
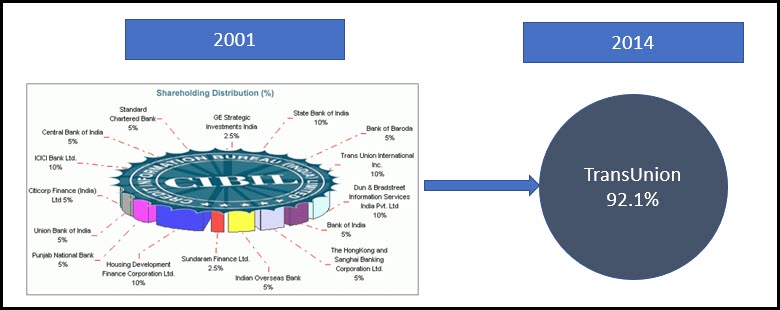 CIBIL is the credit rating agency started under a separate statute to assist the Indian Banking industry. Initially it was owned to the extent of 80% by Banks in India and agreed to share the data of borrowers for better debt management. However today this organization has become “Trans union CIBIL” which is a private sector company listed in USA with a share holding of 92%. In the process, sensitive personal data of 500 million Indians, worth over a few lakhs of crores of INR became the property of this US private company. This was a scam because the loss was on the account of Indian Banks who transferred their shares to Trans Union under an undisclosed deal.
CIBIL is the credit rating agency started under a separate statute to assist the Indian Banking industry. Initially it was owned to the extent of 80% by Banks in India and agreed to share the data of borrowers for better debt management. However today this organization has become “Trans union CIBIL” which is a private sector company listed in USA with a share holding of 92%. In the process, sensitive personal data of 500 million Indians, worth over a few lakhs of crores of INR became the property of this US private company. This was a scam because the loss was on the account of Indian Banks who transferred their shares to Trans Union under an undisclosed deal.
We have also pointed out earlier that Vodafone is sitting on a gold mine of monetizable information which could be beneficial to its share holders.
In any of these instances there is no need to sell customer’s data. The value of the data is substantial even in anonymized form or pseudonymized form or de-identified form.
Value of data in identified form is even higher and can be used provided there is appropriate “Consent” from the data principals.
Naavi had developed a patent application around 2008-2009 under the title “Ad View Certification” where monetization of “Advertisement Views on websites” were sought to be monetized with a sharing of revenue with the contributors of data. These were the days before the concept of “Data Subject” or “Data Controller” or “Data Protection” were known in India. The patent was abandoned as it was not commercialized.
What IRCTC is set to do and what Net4India and CIBIL failed to do is therefore well within the realms of possibility and can be achieved without causing any privacy harm to the railway passengers.
While IRCTC estimates a value of Rs 1000 crores to be unearthed, our estimation is that it could go to several tens of thousands of crores. Implementation of digital assets to discover this Rs 1000 crore value is the scope of Project B in the IRCTC tender.
If this tender goes through, it will be one of the Big Tech companies with experience in big data analytics which may be involved. Their objective could be to discover data value in excess of Rs 1000 crores, hand over Rs 1000 crores to IRCTC and exploit the rest.
The challenge for Privacy Activists therefore is to ensure that IRCTC either through ignorance or through corruption does not become another CIBIL when lakhs of crores worth data is made accessible by the implementer of this project (Particularly Project B).
If at all we need to criticise the tender is to question the ability of IRCTC to safeguard its assets from being exploited.
Though it is stated in the tender document that,
” The implementation strategies of Bidder shall comply with various Acts or laws including IT Act 2000 and its amendments, User data privacy laws including GDPR (General Data Protection Regulation) and current ‘Personal Data Protection Bill 2018 of India, and accordingly propose the business models for monetization of Digital Assets and the Bidder shall ascertain the legality and extent of Monetization of Digital Data of IRCTC before the potential is delved into.”
…it is not explicit on protection of stealing of data particularly since this could be implemented as a Build-Operate-Transfer project.
This project will generate what Kris Gopalakrishnan Committee termed as “Sovereign Data” and it needs to be protected like the Gold or Minerals which are dug out by a private operator from a Government owned mines.
One objection we would like to notify is that the tender does not appear to have flagged the Cyber Security threat including the Data Theft risk and identified corrective measures with indemnity and criminal consequences.
The real concern is in the data being handed over to an unscrupulous operator, developed into a valuable asset but the utility of the same is not available to the Indian Government.
Will IRCTC clarify on this concern?
Naavi
Also refer
CBI Enquiry is required for finding the truth behind TransUNion taking over CIBIL
Is Trans Union-CIBIL guilty of accessing Critical Personal Data through surreptitious means?
Mistaken Identity lands TransUnion in a $40 million class action suit







