Naavi has recently launched the New and Improved service for online Arbitration at www.arbitration.in The service is presently available for any commercial arbitration though lot more work is being done in the background to scale up the services as a new StartUp.
While introducing the service to some of the professionals in the Arbitration industry, it was observed that there was some difficulty in understanding the nature of the service and whether it is a “Legal Service or a Technology Service”.
The fact is that Arbitration.in is a Technology Service to be used by the legal professionals and can be rightly called a “Techno Legal Service”. or an IT Enabled Legal/Judicial Service
It’s Different
Arbitration is already an established ADR (Alternate Dispute Resolution) process and its benefits are easily appreciated. Mediation is another similar form of ADR which also has been used extensively. Worldwide, there has been a talk of ODR (Online Dispute Resolution) and when Arbitration.in is introduced as an ODR, many are unable to immediately recognize that this is not the ODR they have otherwise heard. It is different.
In order to provide more clarity to why the system proposed by arbitration.in is globally unique, innovative and judicially robust, I discuss some of the USPs of the project.
It is wise to be ODR Ready rather than be sorry later
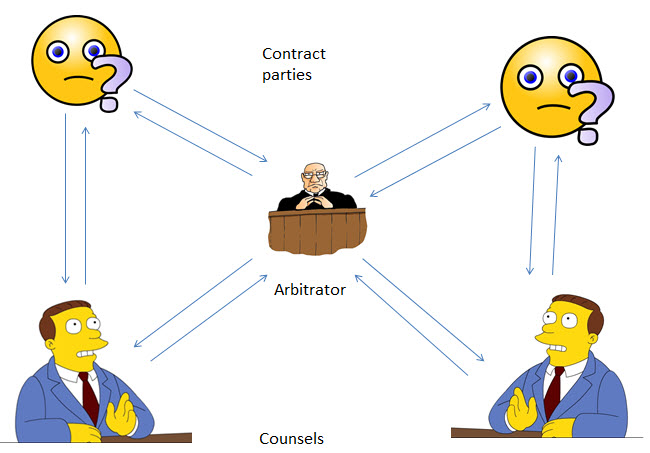
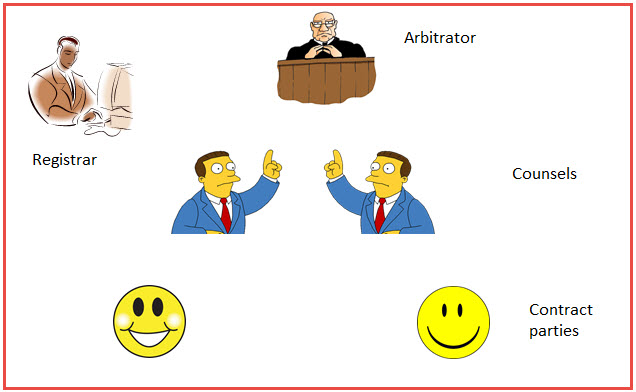
First of All, I would like to clarify that the target audience for the Arbitration.in service are the “Arbitrators” and the “Arbitration Councils”. (Or the Mediators and Mediation Councils).
When an existing Arbitrator is called upon to conduct an Arbitration, it is open to him to set the rules of conduct. Since most of the Arbitrators are familiar with the Court procedures under Civil Procedure Code (CPC), though the Arbitration Act provides them to be flexible, they tend to err towards the safer side of doing things just as in the CPC.
But with the need to speed up the proceedings and particularly when pursuing a “Fast Track” arbitration under the amended Arbitration Act, there is need for Arbitrators to innovate without losing the “Principle of Natural Justice”.
It is therefore open to the Arbitrator to suggest that the Claimant of an Arbitral proceeding (originator) and the Respondent to adopt the ODR process under Arbitration.in.
Inevitability of Transformation
Permanent Arbitral Institutions may in their rules include the ODR process of Arbitration.in as part of their approved process so that any member of the institution can use it if he so desires.
Obviously, ODR of Arbitration.in would not be used if all the parties are comfortable of the use of the system and agree to use it. If they donot agree, the Arbitrator may fall back upon the clause in the Agreement which may define the Seat of Arbitration. In the case of Arbitral Institutions, the institution itself may provide the physical and secretarial infrastructure which will be used by default.
If the disputing parties recognize the advantages of the Arbitration.in facilities, they can either incorporate the use of Arbitration.in in their contract itself or agree to use it in a supplementary agreement. The arbitrator may then have to be chosen on the basis of whether he would be able and willing to use the ODR of Arbitration.in.
It may not be too far for E Commerce companies such as the Snapdeal or 99 acres.com or the online Banks, to insist that they would resolve their consumer disputes only through ODR, since otherwise, the time and effort required for grievance redressal (mandatory requirement under Section 79 of ITA 2000/8) would be unproductive for their business.
Arbitral Houses should therefore try to be “ODR-Ready” before their members start losing out business in the emerging Digital India. At the same time, the young and tech savvy new generation of Arbitration professionals may opt to be individually “ODR Ready” and start using ODR to an extent that public may start preferring them instead of those who stick to the legacy systems.
ODR particularly of the variety proposed by Arbitration.in has the potential to be a disruptive technology that will shake up the ADR industry. Initially there may be an attempt at protecting the legacy system by those who are already established, but sooner or later the young brigade and the USPs offered by the new technology would break any attempt to delay the onset of ODRs as the most preferred option for ADR.
Just as Sunil Manohar Gavaskar had to give up his opposition for limited over cricket the Gavaskar’s of the ADR industry will have to transform themselves to the ODR world.
It would therefore be inevitable that all Arbitrators as well as the Permanent Arbitral Institutions take steps to upgrade themselves to the use of ODR.
Arbitration.in has therefore placed a high emphasis for providing training to the members of the ADR community on how to use the ODR facilities of Arbitration.in. It is expected that the community will use these training services to familiarize themselves with the ODR process.
I have already claimed that the ODR process of Arbitration.in is “Different”. First of all I refer to this as “Virtual ODR” instead of calling it only as ODR so that we can distinguish it from the current forms of ODR which are in vogue mostly outside India.
Transformation from ADR 2 Virtual ODR is
-A Transformation from
–Confusion to Clarity
–Delays to Expediency
–Inefficiency to Efficiency
–Opaqueness to Transparency
I will explain the difference in the follow up article how these USPs add up to make Arbitration.in a globally unique service.
Naavi
Continued…