The story of the former Tamil Nadu Chief Minister Ms J.Jayalalitha’s hospitalization and the mysterious secrecy that shrouded her treatment has now become a topic of discussion on what is “Privacy” in the context of health care in India.
Initially, there was a silent appreciation that Apollo hospital was committed to patient information privacy when no information leaked out of the hospital about the health condition of Ms Jayalalitha. But when arrests were made on any person who publicly wondered what has happened to her, it was clear that the “Confidentiality” concern had turned into some thing more sinister. The attempt was to suppress the information about her health by the force of the law enforcement.
If rumours could cause law and order problem and hence the health information needed to be kept confidential, for the same reason health condition of Ms Jayalalitha was a matter of public interest and the “Confidenitality” or “Privacy” was not sustainable because of the over riding “Public interest”.
Now there is a serious doubt that extends to the charge that perhaps Ms Jayalalitha was murdered and if so the hospital authorities would be considered as “Accomplices”.
It is unfortunate that apart from the doctors of Apollo hospital, there were doctors from AIIMS and one London doctor who were also privy to her health condition and have played along the tune “She was recovering”. They will now be considered as also accomplices if things take an adverse turn.
The fact however is revealing.
Ms J. Jayalalitha, fondly addressed by her followers as “Amma”, was admitted to the Apollo hospital on September 22nd, 2016 on what appeared to be some simple health problem of dehydration and fever. Then she continued to be treated until she was put on ECMO and Ventilator and perhaps a dialysis machine simultaneously indicating a dead heart, dead lungs and dead kidneys. However no proper health information flowed out and all health bulletins said that she was “recovering” and close to being “Discharged as a living individual”.
People were naturally left shocked when finally she was declared dead on the night of 5th December 2016.
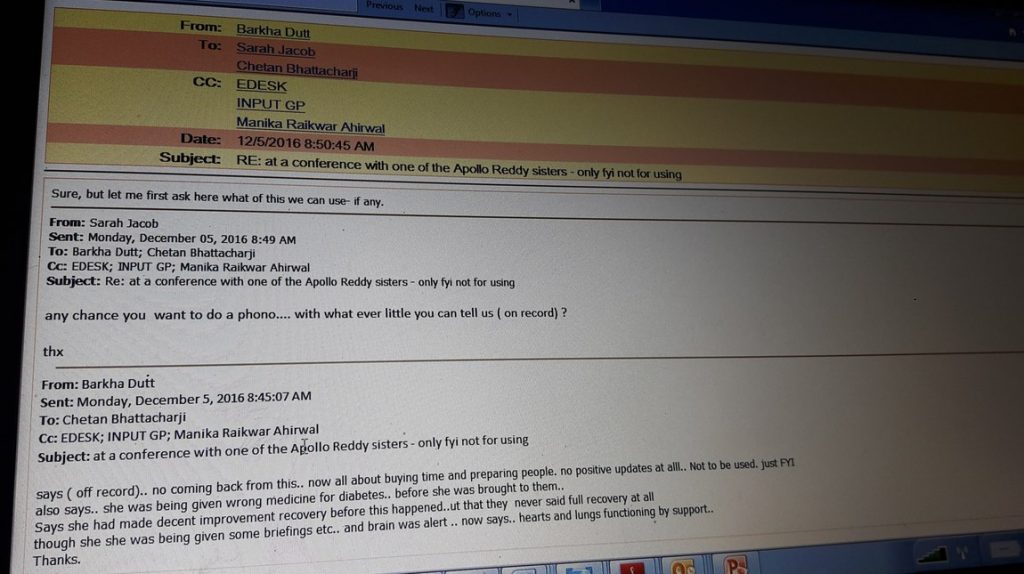
After her death, an e-mail leak of the NDTV journalist Ms Burkha Dutt has surfaced. The email clearly indicates that there was a clear
ground to believe that there was wrong medicine administered to her to worsen her diabetes condition. When she was admitted to the hospital, she was perhaps in a serious condition because of the wrong treatment for diabetes leading to failure of some of the organs and internal infection. Apollo may claim that they were not responsible for this but they definitely had no business to hide it from their medical bulletins.
Apart from this prima facie evidence of what can be loosely termed as “Causing death by negligence”, some of the relatives of Jayalalitha have complained that they suspect some wrong doing and also that the hospital failed to allow them to meet the patient during the last few days. They even conducted a second funeral for her in Srirangapatna holding her burial unsatisfactory last rites.
It is therefore now obligatory on the Government to conduct a thorough investigation to find out the truth. However, considering that the death of a king is always to be suspected to have been caused by the successor, and the prime suspect in this case as per the relatives of Jayalalitha is her potential successor, the investigation cannot be trusted under the hands of the Tamil Nadu police. It has to be handled by CBI and using officers who are not from TN cadre to avoid conflict of interest.
During the days when Jayalalitha was in the hospital, several decisions were taken under her name as part of the Government decisions including one on which her finger print was supposed to have been applied. A forensic investigation on the finger print would reveal if it was a finger print of a living person or a person whose blood circulation and sweat glands donot indicate life. There must be all the medical records and statements of the staff including that of the man political leaders who visited her which all should be collated as evidence.
If any evidence is missing, then it would corroborate the offence and call for additional charges of destruction of evidence and obstruction to justice.
The primafacie evidence indicates that Apollo hospital is in the docks.
Under health care privacy we always say that when the patient is in a mental condition in which he/she is not capable of taking a rational decision, the “legal heirs” have the right to assume charge and the attending physician needs to provide the health information to them. In the instant case, Apollo authorities seem to have decided that “Ms Sasikala” was the “legal heir” to Jayalalitha.
It will be interesting to see how the Supreme Court will interpret this aspect. If a close political associate can be considered as the “Legal Heir”, then in any business concern, if the Managing Director dies or is in a serious condition, it would be the “Deputy Managing Director” who will be considered as the “Legal Heir” to whom the health information would be trusted and not the son, daughter or the kin of the patient. The action of Apollo is therefore unsustainable in law and this may make Apollo a co-accused in witholding heath information from the blood relatives of the patient. The daughter of Jayalaitha’s sister by name Ms Amrita and another cousin by name Deepa have claimed rights as the surviving legal heirs.
Law cannot be changed just because in this case, the political interests are involved. If Deepa and Amrita are the surviving legal heirs, law should determine not only the inheritance of the deceased wealth, but also answer the question why Apollo did not take instructions from these persons during the stage when the patient was not in a mental condition to provide any “Authorization”.
India is now on the verge of framing a law for “Health Care Data Privacy and Security”and it should address situations such as these in no uncertain terms.
Naavi