The so called “Aadhar Hacking Case” filed in Bangalore on Abhinav Shrivastava, has also revealed two important lessons for organizations such as UIDAI, NIC and Hospitals on the one hand and also the Police and the Adjudicator of Karnataka on the other hand. I hope these lessons will be learnt.
Techno Legal Vs Technical Information Security:
Today’s reports corroborate the views expressed yesterday in these columns (Refer :The Aadhar unauthorized access case in Bangalore.. Requires More Debate)in which a tentative modus operandi was indicated.
This is a vulnerability in the systems operated by the e-Hospital application owner and shows lack of due diligence under Section 79 of ITA 2000 and lack of “Reasonable Security Practice” by that organization under Section 43A.
The modus operandi as indicated by the accused in his demonstration indicate the vulnerabilities in the system which not only the e-Hospital app user (eg Hospital like NIMHANS), but also NIC and UIDAI who should have been aware of. It is this kind of threats and vulnerabilities that need to be identified in ITA 2008 compliance audits which these agencies are failing to conduct.
I consider that this incident has given a good example of how “Techno Legal Information Security Incident Management” is different from what people (Information Security professionals who use the Uni-dimensional Information Security approach) call as “Incident Management today”.
I hope that this is the first lesson we need to take note from this incident.
Human Rights Violations by Unwarranted Aggression by Police
Police however have not so far initiated any action on the organizations who contravened provisions of Section 79 and Section 43A of the ITA 2000/8. UIDAI also has not made any complaint against NIC or the e-Hospital application user whose app was used by the Abhinav App.
Instead, both the UIDAI and Police are after the techie who created the app that enabled the release of the aadhar data of individuals on specific request by the mobile owners whose mobile is linked to the aadhar.
On August 4th itself TOI reported that UIDAI chief AB Pandey said, “The UIDAI would like to inform and reassure the public that there is no breach of any Aadhaar data and compromise of individuals’ privacy and security in this case.”
In view of this admission the very basis of complaint by UIDAI can be declared as unfounded and wrong. They rushed to complain before understanding in full what had happened and the Police blindly acted. Ignorant media persons naturally went to town stating that there was a breach of Aadhar security etc.
All this sensationalism will influence the Supreme Court hearing on the Privacy issue. We know that it was one such indiscretion committed by some constables in Palghar who booked Section 66A case against two girls for their Face Book post/like that made the great Supreme Court ultimately coming down heavily on the Section 66A and scrapping it. A similar over reaction of the Judiciary cannot be ruled out because Bangalore Police is making a mountain out of the mole hill in this case.
Now that UIDAI says there is no breach, it is inappropriate for the Press to continue describing this incident as a “Hacking” incident and they should stop this representation. This is actually a “Security Breach” incident in the e-hospital platform which was exploited by a Techie to create an App which was used by about 50000 persons to check their demographic data as available in the Aadhar data base.
This incident was similar to an earlier case which the undersigned had brought out when a Hyderabad techie had created an application for booking of train tickets through IRCTC bypassing some server restrictions and Captcha. In that case the concerned person was informed by the undersigned and reminded by a TOI reporter that what he did in posting an IRCTC booking application for public download was wrong in law. Fortunately, he understood the error and removed his web post before anybody complained to IRCTC. This saved the career of an otherwise intelligent techie.
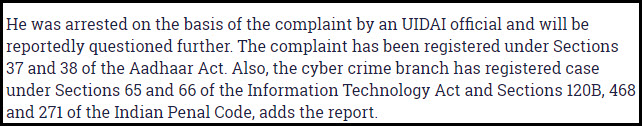
As per the original report on the Aadhar case, the Police had booked a complaint under Aadhar Act Sections 37 and 38, ITA 2008 Sections 65 and 66 as well as IPC Section 120B, 468 and 271. (P.S: Sections used has been corrected as indicated at the end of the article. IPC sections used are Sections 34, 120B, 468 and 471. Aadhar Act sections are not there.)
Now that the complainant (UIDAI) admits that there was no breach of Aadhar data, it is difficult to see the logic of how the Police can apply the Aadhar Act sections.
Section 120B of IPC is for “Conspiracy” which should include multiple persons acting together for common criminal intent. This also is absent in this case and hence this section is not applicable.
Section 271 of IPC is completely off the mark and I cannot understand why it was used. This section states as under:
Section 271 of IPC: Disobedience to quarantine rule.—Whoever knowingly disobeys any rule made and promulgated by the Government for putting any vessel into a state of quarantine, or for regulating the intercourse of vessels in a state of quarantine with the shore or with other vessels, or for regulating the intercourse between places where an infectious disease prevails and other places, shall be punished with imprisonment of either description for a term which may extend to six months, or with fine, or with both.
(Ed: 7th August: As per the copy of the FIR accessed just now, it appears that Section 271 is not added in the FIR. Instead Section 471 (IPC) is present. The error is due to the wrong reporting by a news paper and regretted)
Section 468 of IPC pertains to “Forgery” which also is difficult to be proved.
As regards Section 65 of ITA 2000, it is strange that this section continues to be mis-understood and misapplied in cases where there is no requirement by law for information to be retained for a certain period of time.
The only section that is relevant to Abhinav Shrivastava, incident is Section 66 of ITA 2000 where one can allege that there was an “Un-Authorized Access”. This also can be disputed as to whether the unauthorized access was to a e-Hospital application or Aadhar server and whether there was a dishonest and fraudulent intention.
We also should not forget that in Karnataka, there is a decision of the Adjudicator of Karnataka that Section 43 (and therefore section 66) cannot be applied when the person who has committed the offence or the entity on whom the offence (Unauthorized access) has been committed is not an “Individual”.
Hence under this precedence, Section 66 also may fail in this particular case.
Thus it appears that the entire case is built on fancy interpretation of different sections all together made to appear as if it is a serious and heinous crime deserving a huge punishment. In the process the Police have arrested the person in a good technical position and permanently damaged his career prospects.
Probably all the sections were added so that no bail could be granted to the person. Otherwise when people with thousands of crores frauds are roaming freely both inside and outside prisons in Karnataka, there was no justification that Abhinav should have been remanded to custody and could not have been interrogated without arrest or under house arrest.
If the Police had understood the problem properly and not swayed by the name of the complainant, they could have handled this with finesse without unnecessarily hurting the accused to the extent they have done.
Probably this calls for a review of the police action from the “violation of Human Rights” angle. Unfortunately all our Human Rights activists are only interested in protecting Terrorists and Naxalites and this techie will not be considered as a fit case for them to step in.
I am reasonably confident that some of the more informed persons in the Cyber Crime police station in Bangalore would have felt that the arrest might not be necessary in this case but some body must have persuaded the Police to make this a demonstration of what would happen if some body meddles with the UIDAI system.
“Consistency” is the hallmark of good Policing and unless this is maintained, public will not be able to trust the law enforcement system. I hope that Cyber Crime Police in Bangalore tries to maintain this consistency and stand up to pressures from vested interests.
I request the Police to revise their approach and let this techie out on Bail to mitigate part of the wrong they have already committed.
This is the second lesson we need to learn from this incident.
A Note to the Principal Secretary IT of Karnataka
At the same time, I would like to use this opportunity to remind the Principal Secretary IT, Government of Karnataka, who is also the “Adjudicator of Karnataka” that it is a standing precedence created by a past Adjudicator that Section 43 cannot be applied to anybody other than an “Individual” and hence section 66 also becomes a section that can be invoked only of the victim is an “Individual” and not UIDAI or NIC or a NIMHANS hospital.
The current Adjudicator has the responsibility to review this precedence and correct the past mistake. I request him to take this up suo-moto without waiting for any body to file a petition in this regard.
A Note to the Techies, OLA and other Start Ups
I have repeatedly highlighted the necessity of techies to be aware of the Cyber Law related risks that they may ignorantly transgress leading to a permanent loss of career as this incident would mean to Mr Abhinav Srivatsava. The responsibility lies on the educational institutions (like IIT Kharagpur in this case) and the Companies (like OLA in this case) to ensure that those who are trained to create Cyber products are aware of the ethical ways to use their skills.
Just as I have earlier stated that had TCS conducted a “HIPAA Awareness Training” for its employees who were involved in the EPIC case could have saved the $940 million liability, if OLA had conducted an ITA 2008 awareness training for its key executives, they would have been able to retain Abhinav as their key employee and avoid a shock to its entire work force which would have a very demoralizing impact on the organization.
Perhaps this incident in which OLA was not involved will however reduce its valuation of the because the company they acquired (Qarth Technologies Pvt Ltd) is now an “Accused” in a Cyber Crime. Other Start ups need to take note.
Naavi
P.S: The above article is based on the news paper report on the sections under which the arrest has been made. Also, it is possible that Police may have information that we donot know. These views may therefore be taken as a view based on available information in the public and stand corrected if required.
7th August 2017: 19.00 hrs: PS: I have just accessed the FIR copy and would like to make a correction in the sections used in the case. As against the earlier asianet report based on which the sections have been indicated in the above article, the FIR indicates the following sections now: Sections 65 and 66 of ITA 2000, Sections 34, 120B, 471 and 468 of IPC. The complaint has been made by UIDAI but the sections of aadhar act seems to have been removed. Some of the comments made in the articles therefore stand corrected.
The earlier report of the sections used was based on the following news report in asianetnews.
Naavi