Zomato a leading Mobile App owner and a restaurant guide has suffered a major security breach in which 17 million data sets of customers including the name, email address and hashed password is reported to have been lost.
The hashed passwords are said to have been hashed using the MD5 algorithm which is considered weak and has already been dis-accredited even in India for a long time.
Most of the customers of Zomato are Indians particularly from the high income group of IT workers who use the App on a regular basis.
It is suspected that the data lost may include the payment details which may include Credit Card and Bank related data.
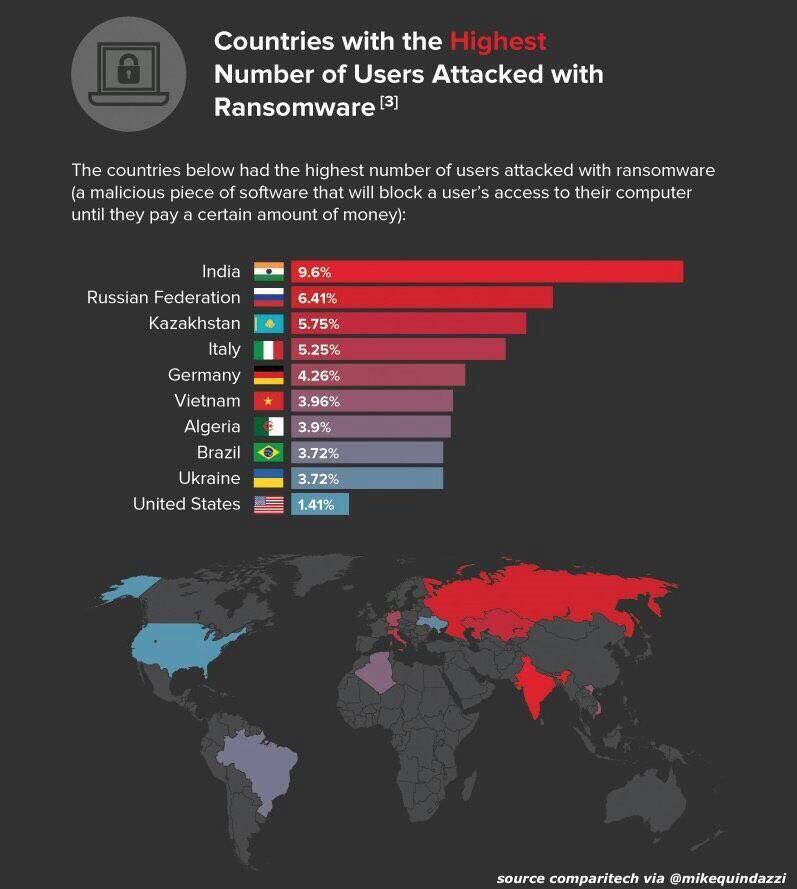
This is therefore a very serious situation that could in association with the currently prowling ransomware and other malware could create chaos in the Indian Financial Markets.
We have a real Cyber Financial Terror threat on hand and need to defend the situation in national interest.
There are discussions about what kind of liability does Zomato face under Section 43A of ITA 2000/8 for failing to provide “Reasonable Security” for the “Sensitive personal Data”. This is a legal discussion which can be kept for a post mortem analysis.
But what we now need to decide is an action plan on how to handle the crisis. This is a disaster management situation where the Private Sector, the Public Sector as well as the regulators need to come together and find solutions to first contain the damage and ensure that there is no large scale adverse effect on customers of Zomato.
There will be two kinds of Zomato Customers. Those who have downloaded the App and used it for searching the restaurants and those who have further ordered food through Zomato and made payments.
According to Zomato, all payment information on Zomato is stored in a highly secure PCI (DSS) Compliant vault and hence no payment information or credit card data has been leaked.
Zomato also claims that the passwords leaked are in hash format and hence is not easily readable though there is a claim that MD5 hashing is not secure enough.
On the other hand, the Privacy Policy of Zomato says:
“We assume no liability or responsibility for disclosure of your information due to errors in transmission, unauthorized third-party access, or other causes beyond our control.”
It is doubtful that such blanket self declared indemnities are valid in law.
In US, it is common regulatory imposition in such cases for the organization to pick up the cost of “Data Identity Theft Insurance” for a certain period such as 2 years. (Such insurance may cost around $30 per person and in the current instance it would be of the order of $500 million in total). Such an insurance covers consequential losses that may arise to the data subject on account of the current breach.
In India we donot have any precedence of any organization being held liable unless an individual files an Adjudication application under ITA 2000/8.
ITA 2000/8 of course provides an option for the Adjudicator to take Suo Moto action on behalf of unnamed victims and impose a fine on an offender but we can be reasonably certain that no Adjudicator may do so. (In the current case, the jurisdiction may fall on the Adjudicator of Haryana.)
The companies like Zomato are ignorant that there are multiple sections under ITA 2000/8 where civil and criminal liabilities are defined for lack of compliance.
While the company claims PCI DSS compliance, there is no indication of whether the Company is “ITA 2008 Compliant”. It is obvious that the company may not even be aware of the need to be ITA 2008 compliant and like many other companies, big and small, consider Indian laws with a “Chalta hai” attitude while looking at international laws with reverence.
Some are suggesting therefore that this is the time to make Zomato an example and make these companies realize their responsibilities. Naavi has a history of pursuing Banks for their negligence and has been shouting from roof tops that the Start Up companies using Mobile App based business model should also be ITA 2000/8 complaint and should not be blinded by being certified either under ISO 27001 or PCI DSS.
Unfortunately most IT personnel in these companies donot want to take responsibility for running the business fairly and take the consumers for a ride. Professionals in such companies often are not worried since at the first such instance they leave the troubled company and join another company leaving the promoters to go behind bars if necessary.
Promoters on the other hand are often dependent on professionals who donot take any liability for their negligence and end up paying the price.
If CERT-In and the Police are strict in implementing the provisions of ITA 2000/8, most of these companies will find their business unviable under their current business models.
Without further hurting the already hurt Zomato, its promoters and their IT professionals, let us see how the situation can be salvaged.
Zomato presently uses a Privacy Policy and Terms which indicate their present commitments to security which need to be reviewed. A Copy of the Privacy and Terms of use is available here.
The Privacy Policy is an “Implied Contract” which is a “Standard Form Contract” and an “Unconscionable” contract. It is legally unacceptable and hence cannot be defended. This was my argument against Banks and will hold against these companies also.
We can therefore consider that the Company is likely to be held liable to prove its “Due Diligence” with the appropriate authorities and the Courts if required.
It can however be said that ITA 2000/8 compensates when a loss has accrued and not on a possibility of loss. Hence Zomato may not immediately be liable for any actual loss. There is also a lack of “guilty mind” and hence it can defend against normal criminal charges.
However, regulatory agencies may be able to persuade and it would be a good gesture for Zomato to offer a warranty to its customers in the form of “Cyber Insurance Coverage” against “Any loss that may arise to the customers of Zomato, within the next one year on account of data loss that can be directly attributed to the current breach, subject if necessary to a limit of (say) Rs 25000”. I am sure one of the Cyber Insurers can structure a policy of such nature.
Additionally, Zomato should assure to revise its Privacy Policy and Terms to be in tune with the legal requirements in India and also introduce a grievance redressal mechanism (Which may include the Online Dispute Resolution Facility similar to what is suggested in www.odrglobal.in) .
As a PR exercise it can also provide some discount coupons to soften the impact to all those customers who are willing to forego the Cyber Insurance coverage otherwise offered. (Probably most would opt for this rather than wait for Cyber Insurance).
The CERT on the other hand needs to examine the claim of the company that the critical data lost is in encrypted/hashed state and the risks are containable. Users will better change at least the VBB associated with the cards (or its equivalent) they might have used in their transactions with Zomato.
Credit Card Risk managers need to create an “Adaptive Authentication Filter” by which any card used at Zomato would be flagged for additional authentication.
With such protective measures we may be able to reduce the impact of the crisis until another reckless App company brings in another crisis for the Citizens of India.
Naavi