US is a land where commercial exploitation is the natural business strategy. The Face Book, Google, WhatsApp are all representations of such “Money First” approach. The laws are therefore often used to make money while pretending to protect the common man.
The “Ambulance Chasers” are a creation of this tendency. A new genre of “Ambulance Chasers” are now emerging in the light of the “Privacy Laws” which try to provide several rights to the Data Subjects to protect their sense of Privacy.
We had discussed in our earlier article “How Do I harass a Company with GDPR”?how a Company was harassed by a data subject by an unreasonable pursuit of a a valid right with no substantiation of the “Harm”.
Presently it appears that some companies in USA have started a business by which they can represent such data subjects and raise claims on other companies apparently in trying to protect the interest of the data subject but more surreptitiously to extort money from companies.
The business model of Privacybee.com is one such attempt where the modus operandi starts with an innocuous looking e-mail is sent to a company stating that X is my customer and please let me know whether his/her personal data is being processed by your company. There will be no “Verification” of the data subject nor a digitally signed e- mail request. It does not substantiate what harm has been caused to the data subject by the suspected processing of personal data of their customer by the noticee.
To answer this query the Company has to search its data base for the name of the data subject with only such supporting information as an “E Mail Address”. Even if the Company cannot find any data, if the Company has to commit it through an e-mail, it has to make a “Personal Data Discovery attempt” probably through an external consultant and certify the findings under Section 65B of Indian Evidence Act before responding that no data is being processed for X.
The cost of this exercise is disproportionate to the basic cause which is “Prevention of harm to the data subject”. Privacybee.com does not send/ provide evidence about how it has obtained the right to represent the data subject. Instead it sends out a link which is meant to promote subscription to its service. It refers to a page claiming to show “Power of Attorney” authorizing the request which may lead to a 404 page.
Indian companies may remember that a “Power of Attorney through Electronic Document” is not recognized under Indian ITA 2000 (Section 1).
The notice exercises a “Right to Forget” which according to Indian PDPB 2019 requires adjudication.
The notice does not provide any context where the consent might have been given and simply declares that consent is withdrawn. Indian PDPB makes it necessary for withdrawal of consent to be justified and in unreasonable withdrawal, expect the data subject to bear the cost.
The notice makes references to several data protection laws both from US jurisdiction and EU jurisdiction (known to privacybee.com) without establishing how the data subject and the notice receiving company is related to the relevant law.
As expected the notice ends with a “Threat” of legal action if no reply is sent within one month. In the absence of the proof of damage or harm caused to the data subject the threat of legal action does not stand judicial scrutiny.
When such e-mail notices are received by Indian companies, Naavi.org considers them as an “Attempt to harass and extort money” from Indian companies. We have flagged this incident with the Ministry of Information Technology and the CERT-IN .
While the PDPB-2019 was being drafted, we have repeatedly brought to the notice of the Justice Srikrishna Committee as well as the JPC that Indian data processing companies need to be protected against misuse of such privacy related notices by introducing a provision that
“No legal action against a registered Indian data processor would be permitted without sanction from the Indian Data Protection Authority.”
We called it as the “Umbrella Protection”
We have also repeatedly suggested that Indian companies should provide for a GDPR Exclusion clause in their Privacy Policies to expressly disclaim the jurisdiction of GDPR and other foreign laws.
This issue is some thing that Nasscom should address in the interest of the Indian data processing companies. However NASSCOM and DSCI may be more interested in fighting against Indian data protection legislation rather than taking up such public causes.
A time has come now for Naavi.org to consider representing such victim companies who are being harassed by privacybee.com type of vultures.
We may remember that such activities (like what Privacybee.com wans to undertake) under Indian PDPB 2019 are allowed only of the organization itself gets registered with the Indian DPA as a “Consent Manager”. A consent Manager is himself a “Data Fiduciary” and is expected to follow law. We can observe that privacybee.com does not follow privacy principles under either CCPA regulation nor the GDPR regulation but projects itself as the Privacy Saviour.
We invite companies affected by such companies to come together as an “Association of Data Processing Organizations in India” and fight for their justice against international data invaders. We request MeitY to take a lead in guiding such companies. This can also be part of the PDPB 2019 revised after the JPC discussions. We await the final version of the PDPB 2019 when it is presented in the Parliament.
The privacybee.com is registered as a company in USA and we request FTC to conduct an enquiry about the activities of this company and for Attorney General of Califorina and Washington also to conduct their own enquiries on this extraction racket.
If this tendency to misuse law is not curbed, the genuine data subjects who are really harmed and need to take the protection under a data protection law will also get discredited and their rights will get diluted.
Naavi
Also refer:
Protect Indian Companies from possible GDPR overreach
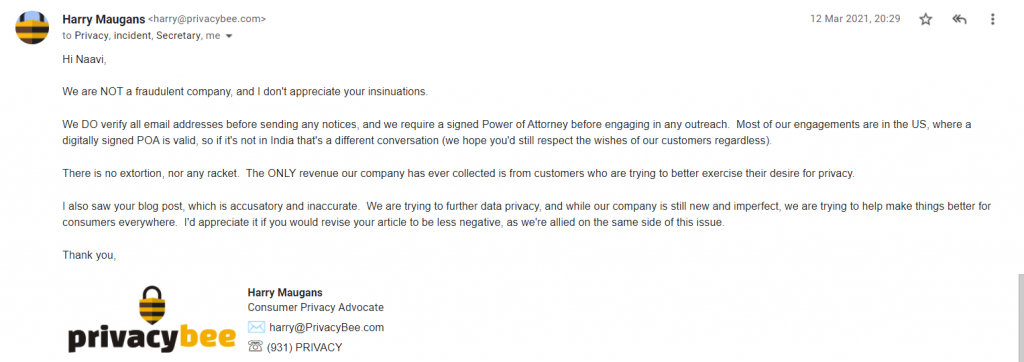
Following is the reply received from Privacybee.com
P.S: We are happy to note that the company acknowledges its restricted jurisdiction. Our intention is to point out that the business model built on sending a roving enquiry relying on a general power of attorney without a company specific request from the data subject when the data may not belong to a EU citizen, is unethical.