[P.S: This post is meant for the Academicians and discusses certain theoretical concepts. Professionals in the Information Security domain may seriously dispute some of the concepts and it is considered perfectly logical and welcome.]
Naavi is a techno legal professional and has been thought leader in the field of Cyber Laws in India. Many of the innovative thoughts of Naavi have been expressed through this website and have found practical uses in the form of services.
As an academic practitioner, Naavi has applied his Technical, Legal and Behavioural Science training and education to the field of Information Security to develop his own version of Total Inform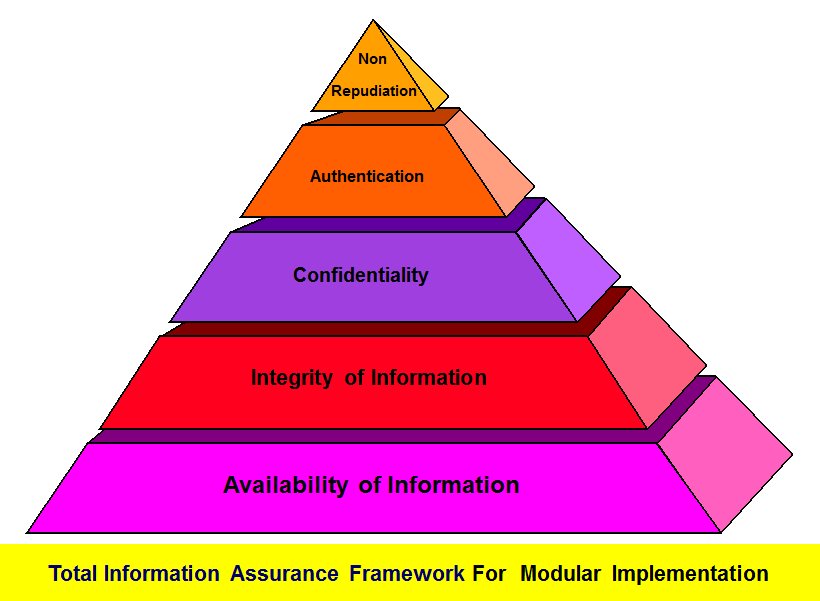 ation Assurance (TIA) built on the pyramid model of hierarchy of TIA objectives from Availability to Non Repudiation through different stages of Integrity, Confidentiality, and accountability.
ation Assurance (TIA) built on the pyramid model of hierarchy of TIA objectives from Availability to Non Repudiation through different stages of Integrity, Confidentiality, and accountability.
Naavi has adopted a model which differs from the traditional model with “Availability” as the foundation while traditional thinking of “Security” places “Confidentiality” as the focus and no hierarchical stacking of objectives. The reasons for the deviation is explained elsewhere and it suffices to say that it is based on the practical implementation thinking process of a business manager and stems from the basic premise that “Information Security is for the protection of the Information Owner” more than “Protection of the Information” and hence decisions are to be guided primarily from the business owner’s perspective and not the perspective of the Information Security professional if the two functions can be distinguished.
Similarly, Naavi propounded the “Theory of Information Security Motivation” based on the “Pentagon model” where he tried to explain the process of how Information Security implementation in an organization can be motivated for implementation by the practitioners. This adopted a closed 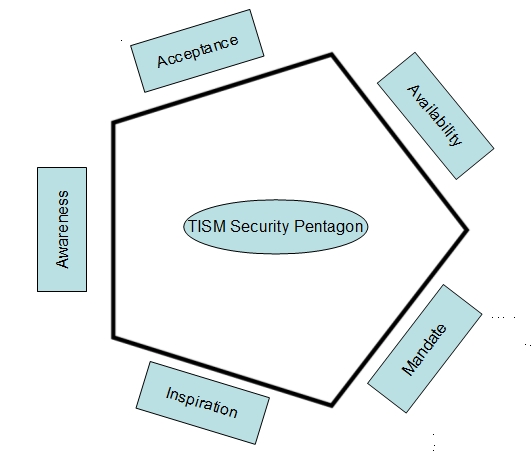 wall integrated approach concept instead of the hierarchical concept under the premise that all 5 elements of IS motivation need to close in like walls to be effective.
wall integrated approach concept instead of the hierarchical concept under the premise that all 5 elements of IS motivation need to close in like walls to be effective.
The essence of the theory was that IS implementation cannot be motivated until the five elements of Awareness, Acceptance, Availability, Mandate and Inspiration formed a closed boundary plugging the possible leaks. This included the three dimensions of technology (availability and awareness), Law (Mandate and awareness) and Behavioural Science (Acceptance, Inspiration and Mandate).
Now, in the “Theory of Secure Technology Adoption” Naavi is focussing to study and present how in his view, technology is adopted by people and organizations and what is the role of security in such technology adoption.
Obviously there could be many other studies of similar nature which has thrown up different dimensions of this thought. This is yet another contribution to the academic pool of thought.
I will present some brief thoughts about the theory in subsequent posts and expect others to build on it and develop it with the central thought that “Secure Technology Adoption” has a pattern which we try to understand so that in future product/service developers would take note of why certain technologies get easily adopted and certain technologies get adopted after a lapse of time and certain technologies are shunned by the market.
In developing my thoughts on this subject I would be influenced by what I have read, studied, tought and experienced over time and hence reflect some thoughts of the great thinkers of the past. Such coincidences are incidental and not intentional.
Naavi