Our honorable Minister of IT Mr Ravi Shankar Prasad has stated that India will create a Global bench mark with its Data Protection Act which is being drafted now.
While we welcome the goal set by the Minister, it is time to discuss how India should approach creating the Global Bench Mark. The proposed Act will be based on the report of the Justice Srikrishna Committee which will actually draft the contours of the Act to which the Government will just add some structure.
Since Justice Srikrishna comes from the judicial background and we are fresh with the 9 member Supreme Court bench decision that “Privacy is a Fundamental Right”, it would be reasonable to speculate that the proposed “Data Protection Act” will operationalize the “Informational Privacy” as discussed in the judgement.
After the judgement, there is already a discussion on whether mobile information is subject to Privacy and whether Police can seize mobiles etc. There is therefore an apprehension that if the law is not properly drafted, there would be serious hindrance on the capability of Police in particular to carry out investigations. Criminals and Suspects will quickly jump to Courts and bring stay and by the time Police are able to get the stay vacated, the electronic evidence might have been irrevocably erased.
The proposed act will note that “Privacy” is equivalent to “Right to Control personal Information in data form” and hence protection of Personal information is the objective of the Data Protection Act.
Will the Act therefore focus only on protecting “Data that contains the personal information”? or will it extend its scope to all types of data including those which constitute say Copyright, Domain Names, Patents?, Will it also extend to corporate information such as financial data, marketing data or HR data? Will it also extend to log records? telephone conversations? …are all matters that this act will perhaps try to address.
This means that the Act should define what is “Data that has to be protected”? and then proceed to classify them into “personal” and “sensitive personal”, “other” etc.
The Act needs to also define who owns “Data” and whether “Data” is a property? and how the Data can be used by who soever owns?
When Data gets aggregated, value gets added and there is always a question whether this value addition belongs to the data subject or the data processor or the data controller who actually instructs the data processor to process the data in a particular manner. Under the Copyright law, the data base administrator gets the copyright on the aggregation part and therefore it recognizes different property rights between the raw data supplier who is the data subject and the entity which adds value which is the data processor or any other entity that uses the raw data .
If Copyright law recognizes copyright on data base creator, then similar principle has to be used in the data protection law also recognizing that the nature of property changes from the data subject to the data processor.
Once we recognize that “Data” is a “Commodity” and different values can be ascribed to it in different stages of its life time, we need to recognize it as a property which can also be traded.
Recently a store in London was reported to be accepting “Personal Data” as payment in exchange for goods.
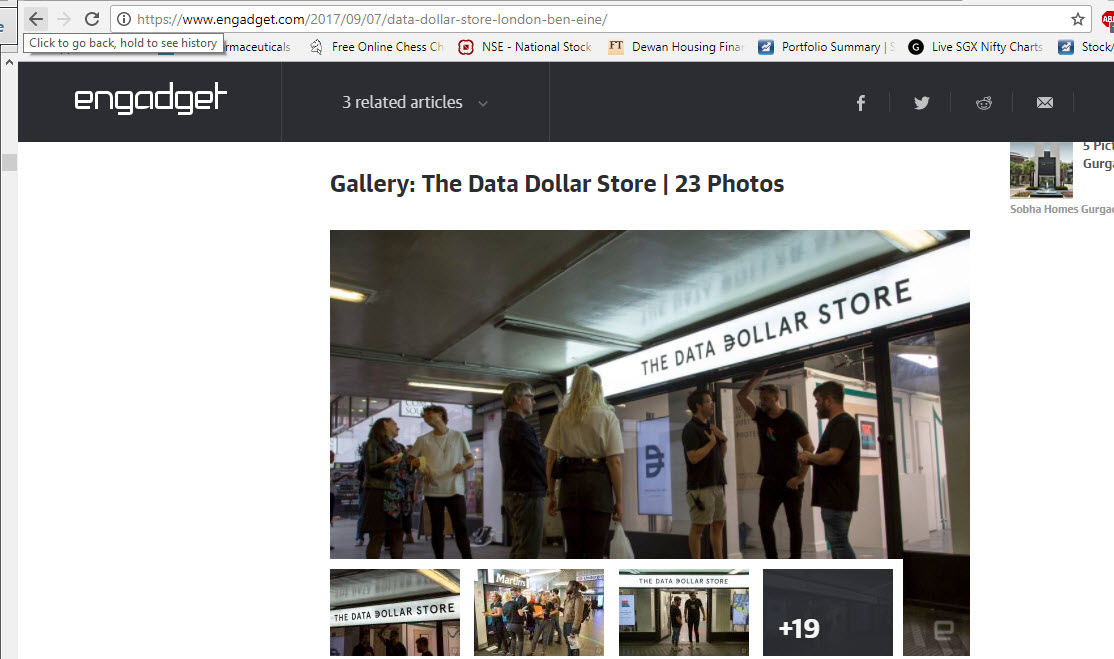
The “Data Dollar Store” appears to value the data you present and allow you to trade them. In a way it is a “barter” system . From the initial reports, it appears they may accept some photographs etc as “Personal Data with value”.
Of course if you offer “Digital Money”, perhaps they may not refuse since this also is “Data”… but the concept is interesting particularly for people who can create valuable personal data instances.
Coming back to our discussion on Data Protection Act, there are some practical problems that the authors of the law will encounter. Since the Supreme Court has not really defined “Privacy” but went on a wild discussion on what one eats or where one travels etc is all “Privacy”, the Zomatos and Make My Trips will be dealing with “Privacy Sensitive Information”. If therefore Government makes any law that tells how such companies need to collect information and deal with it, such a law may be questioned as a violation of a Fundamental Right not being saved by the exceptions of national security etc.
We realize that if we take this extreme view, then there can be no e-commerce without some form of personal data being shared with the service provider. Currently, accepted privacy principle is that one can collect personal information as long as it is necessary to provide the service offered and a “Consent” is provided by the data subject in the form of a “Deemed Contract”. The only discussion is on the quality of disclosure and ethics of the collector in collecting only the minimal required information and using it only for the purpose it is required.
But can the Government make a law stating that “The Fundamental Right of Privacy can be infringed by any individual if he has taken a consent in the form of undigitally signed web/mobile based acceptance forming a deemed contract in which the data subject’s rights are agreed to be infringed”. Will it be a “Contract for a consideration that is legally untenable”?
If we take a stand that this is a globally accepted principle and there is nothing wrong in the data subject entering into a contract with another person saying that he can make use of the personal data and he is not pressing his fundamental right, then we are automatically accepting that “Data is a commodity that can be transferred for consideration”.
Will Justice Srikrishna committee be having sufficient courage to say that “Personal Data” is a “Property of the Data Subject” and he can sell it for a price which includes agreement to use the services offered by a service provider?. If they do, then Government will not have any problem with its Aadhaar per-se or mandatory linking of Aadhaar with PAN or mobile number etc.
But If they do, they may be standing against the spirit of the 9 member Supreme Court judgement.
If the Srikrishna committee hesitates and continues to carry over the uncertainty on the definition of Privacy from the Judgement to the committee’s findings, the problem gets transferred to the Meity in drafting the law.
The Government can simply define the law as a “Law to protect the Confidentiality, Integrity and Availability” of Information and make it more as Cyber Security law than anything else. It will of course create the office of the Data Commissioner. It may also introduce licensing of data processing and other regulations and in the process may make the life of E Commerce entities such as the Zomatos and Make My Trips miserable.
In the end, the law will be an extension of ITA 2008 and will not add much to the domain of “Privacy Protection”.
In all probability, this is what is going to happen and we will continue to keep worrying about the definition of Privacy and without understanding its nature try to protect it in data form.
Considering the futility of such an exercise, I would like the Government to accept that given the wide definition of “Privacy Right” as ascribed by the Supreme Court, it is not possible to make a law that protects the unknown and omnipresent.
Instead, the Government may focus on how the Citizens can be compensated when a “Data Breach” occurs and go onto define “Data Breach” and its consequences.
The definition of “Data” can apply to any information in electronic form and “Breach” is defined as any action which is a violation of a contractual agreement.
If we take this approach we need not define what is “Data that is Personal Information”, “Data that is Sensitive personal information” and “Data that is neither a personal information or a sensitive personal information.”.
If the Supreme Court can use a strategy to define the “Privacy Right” without defining “Privacy”, Government may be able to create a “Data Protection Law” without treading on the difficulty of defining “Data which is Personal information that forms part of the Privacy Rights”.
The existing law in ITA 2000/8 and the rules there under, are sufficient to carry on the market activities since it already provides a definition of personal Information as well as Sensitive personal information in addition to the larger set called “Data”.
The new law can state that any person can enter into a contract with his data as a commodity and bring the data protection requirements under the Indian Contract Act read along with ITA 2000/8.
The new law can also enable and empower any business that may be set up to buy, sell, process or exchange data under a contractual agreement with the data subject or a personal data custodian to whom the data subject has transferred his personal data.
This will define the “Data Trading” concept and provide clarity to companies in Data Analytics and Big Data activities. It will also prevent the IoT industry from being stumped with the new Privacy debate since any information collected by the IoT device is likely to be considered as “Personal Data”. Though IoT data is linked to the device ID, along with the purchase and installation information, it is linked to the personal data of the owner and his location and hence will become a part of the “Privacy Right”. The CCTV captures will also be legally protected if a person walks into a mall and is being photographed by the CCTV system in exchange of the benefit of walking through the premises.
Additionally innovative companies may set up business to de-identify a data set and create value there on before they are actually sold for a profit which they can share with the data subject at the time of re-identification.
Some company may also set up a “Regulated Anonymity” system where it will absorb the identity and provide a proxy ID to the user with which he can do all transactions on the internet. The business can even run an “Identity Gateway” where the identity such as Aadhaar or PAN etc can be pseudonomized without adversely affecting any service or security requirements of the Government while at the same time protecting the critical identity data from unknown threats.
It is to be recognized however that these intermediaries are still vulnerable to an Equifax type of attack on their systems which could compromise the customer data if they donot implement appropriate security measures.
In such a eco-system, the so called “Data Protection Law” may change its objective from “Protecting Data” to “Protecting the Citizens from the consequences of a Data Breach” where Data breach is defined as an unauthorized data access in contravention of the data sharing contract.
Such consequences will of course expand on what ITA 2008 now says as “Intermediary Responsibilities”, “Civil Liabilities” and “Cyber Crimes” but with a better implementation mechanism.
The new law can additionally define a system of “Leasing of Personal Data” different from “Selling of Personal Data” to meet temporary requirements. This would automatically incorporate a right some where nearing the “Right to Data Erasure” as referred to in GDPR since data leased cannot be used beyond the lease period. It will automatically terminate the rights of the data processor and shift the onus on him to get the contract renewed much better than the current “Opt-In” system.
The new law can also talk of “Fundamental Duties” of a citizen as a “Data Subject” and uphold his fundamental rights to decide how he can use his personal data including monetizing the personal data as if it is a property that belongs to him. If there after a challenge is mounted on the law in the Supreme Court and it has to take objection to this law, they have to object to the provision that defines the fundamental duty and fundamental right of a citizen to deal with his own data property. Hence the law may be protected against a legal challenge.
In this context, it would be better to call this law not as “Data Protection Law of India” but as “Data Breach Protection Law of India”.
Naavi