The Year 2017 saw a big fight against Black money which started in the last months of the previous year with the “Demonetization Drive”. The move was bold and long awaited.
However, two things worked against the complete success of this move. The first was the presence of a large number of fake currency notes in the country, some of which was perhaps produced by well equipped Government presses in Pakistan. This completely foxed even the RBI which lost count of the demonetized currency returned to the Banks. The second was the dishonesty of some of the Banking employees who assisted corrupt persons in the society and exchanged notes even at the Bank and RBI level itself.
Nevertheless, though at first glance it appears that the demonetization move might not have succeeded as expected, there is no doubt that not all persons holding black money earlier in Rs 500/1000 denominations could get it converted into new currencies. Hence in reality, black money did go down in circulation and much of the idle money held by individuals came out into the Banking system. Many who used proxy accounts to deposit their monies are now caught in the investigation net of the tax authorities and this should result in higher tax revenue for the Government.
However, the year 2017 also saw the growth of an alternate to Black Money in the form of Bitcoins and a phenomenal growth in its international price. There is definitely a speculation that a large part of the Indian black money must have got itself converted into Bitcoins and this could be one of the reasons apart from the creation of a “Future Trade” that helped the Bitcoin rates to go up.
However, within India, the increased attention received by Bitcoins can be directly linked to the “Power of Black Money” and the related “Power of Corruption”. People who are in the forefront of corruption in India are the politicians and the bureaucrats and it is evident that they have become big supporters of Bitcoins now. The techies who created the Bitcoins and the businessmen who sensed its commercial value earlier are now the conduits for conversion of Black Money to Bitcoins and their laundering into new Bitcoin holdings of public who are being lured into the game as if Bitcoins are an investment avenue.
Recently, Business Standard carried a report on 28th December 2017 which has been reproduced below. This report raises several questions of propriety at the way the Finance Ministry is functioning when it comes to regulation of Bitcoins and indicates the possibility of corruption having been taken over the officials. I request Mr Arun Jaitely to investigate the matter.



Firstly we note that this report filed by one Mr Shirmi Choudhary categorically states that the “Government has decided” and is “Likely to define crypto currencies and bring in a regulatory framework in the Union Budget 2018-19”.
This means that the Finance Ministry is using its power to bring a “Finance Bill” to over come the objections of RBI and give a legal recognition to Bitcoins.
Though the same ministry cautioned on the next day by the following report, stating that “Virtual Currencies are like Ponzi Schemes”, the report quoted above is more specific of the intentions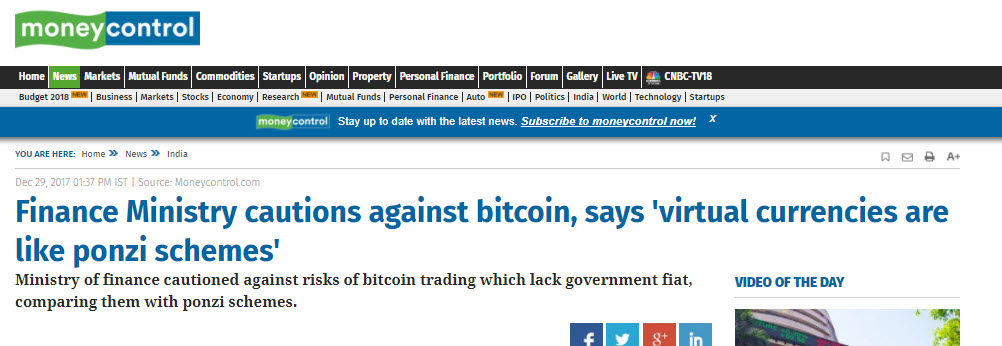 of the Government and quotes “A Government official privy to the developments”. It also quotes that the “Expert Panel” has stated that “These currencies are as good as fiat currencies”. It goes ahead to quote the tax officials as stating that “Due to lack of clarity” the gains in Crypto currencies cannot be taxed.
of the Government and quotes “A Government official privy to the developments”. It also quotes that the “Expert Panel” has stated that “These currencies are as good as fiat currencies”. It goes ahead to quote the tax officials as stating that “Due to lack of clarity” the gains in Crypto currencies cannot be taxed.
It is clear that the official has revealed that the Finance Ministry is actually trying to help the Bitcoins being recognized as a “Legal Currency” which could be used instead of Rupees in transactions. Once this is done, the entire Bitcoin market capital and along with it the entire Crypto Currency market capital in the world becomes legal tender in India.
We must note that the estimated market capital of Bitcoins is US $ Rs 217 billion and the estimated market capital of all Crypto currencies is about US# 571 billion. (1 billion USD=Rs 6400 crores). The Bitcoins and other Crypto currencies are fungible and can be converted with each other with no control. Hence if Bitcoins are legalized in India, about Rs 36.54 lakh crores equivalent of Indian Rupees would come into “Currency with the Public” which includes residents and non residents and further includes criminals, terrorists, foreign Governments etc. This is perhaps twice the pre-demonetization currency stock in India, and about six times the floating currency in the country.
What will such flooding of the market with free currency mean to “Inflation”? … economists need to explain.
Since some of this holding will be with foreign countries including China, what will be the impact on our international economic stability? the Finance ministry should explain.
Since part of the holdings will come into the hands of the terrorists including ISIS and LeT, what will be impact of this on terrorism in J& K, our home ministry should explain.
Does the Secretary of the Ministry of Finance explain whether there is any possibility of legalization of Bitcoins in the next budget?. If not what do you mean by “Regulation of Virtual Currencies”?
I demand that the Finance Minister Mr Arun Jaitely has to explain to the public of India if anything is cooking up in the background and the honest Citizens will be surprised during the budget session with a decision which will favour Dishonest Citizens of India?.
If not, how come Business Standard reporter quotes an official of the Finance Ministry on the budget provisions?
If Crypto currencies are recognized under the Finance Bill, there will be no parliamentary debate on the matter and even if it is debated, the opposition is more keen than the ruling party to have an avenue for black money and all our MPs will unanimously pass the resolution to legalize Bitcoins just as they come together for passing a raise in their salaries.
Only Kirit Somayya and Rajeev Chandrashekar would be the MPs who may like to fight against Bitcoins but they will be in complete minority.
The Finance Ministry at present does not even know how to distinguish Crypto Currencies from “Digital Currency and Virtual currency”. They refer to Bitcoin as “Virtual Currency” which itself betrays the confusion of the officials.
Some officials in ED appear to be looking only at the revenue potential of taxing the Bitcoin transactions. We need not be surprised if these officials look at legalizing drug trade and gun trade so that government revenue can be increased.
The SEBI Chairman who should have swung into imposing penal action on Bitcoin exchanges,is completely sold out to Bitcoin recognition to the extent that when MCX posted a message in the MyGOV.in site arguing for legalization of Bitcoins, no action was taken on MCX officials. Shame on them.
The Finance Ministry officials including SEBI are guilty of not taking penal action against the entities which are calling themselves “Bitcoin Exchanges”. The ED has conducted a survey and confirmed that there are more than 4 to 5 lakh perople who have done transactions in Bitcoins. If the exchange is not licensed either by RBI or SEBI and was an “Illegal Exchange”, why is RBI, ED and the Finance Ministry keeping quiet?
I suspect that many of these officials have been corrupted with “Bitcoin Gifts” and cannot be relied upon. The Government has not asked these officials to declare their Bitcoin holdings despite a call for the same. The reluctance itself tells a story of its own.
Is this not a dereliction of duty on the part of SEBI Chairman and also our honourable Minister Mr Arun Jaitely?
The time has passed for Mr Arun Jaitely to say that he is on the side of curbing black money. By not taking any action on Bitcoin exchanges and simply fuelling speculation on whether Bitcoins will be regularized or not for more than six months, Mr Jaitely has become the central figure of “Lack of Action Against Bitcoins”. Today, I may be the only person who have lost confidence on the Finance Minister. But soon there will be others…unless he acts decisively to completely shut off the speculation in Bitcoin trade by announcing the ban on Crypto currency trading in India before the budget.
The year 2017 will not go down as the year of achievement for Mr Jaitely because of GST. It will go down as an year of lack of action against Black Money by allowing the growth of Bitcoins.
I urge Mr Jaitely to clarify that my conclusion is wrong.
I therefore urge Mr Modi to open his third eye and destroy the evil called “Crypto Currency” (I refer to the privately managed crypto currencies like the Bitcoins”. If he does not wake up, all his work against Black Money will be ground to dust under the growth of Bitcon usage in commercial transactions.
This is what I look forward to in 2018.
Naavi