Aadhaar has been the center of Privacy debate for quite some time in India and has even attracted international attention. Amidst the criticisms that Aadhaar system is not properly secured and therefore it may lead to loss of privacy of the citizens, Supreme Court took up a petition on whether Aadhaar infringes Indian Constitution and should be discontinued. Initially, the Aadhaar baiters scored a victory as Supreme Court under the previous CJI hurriedly constituted a 9 member bench and passed a judgement stating “Aadhaar is a Fundamental Right”. It appeared as if the judgement was a tool given to the smaller bench which was hearing the Aadhaar constitutionality issue to scrap Aadhaar.
However things have changed in the last few weeks. First the new CJI shuffled the bench and case allocation rules so that politician advocates who wanted to get the Aadhaar case heard by a bench of their choice were frustrated in their design.
The case is now being heard in a more neutral bench than what the politicians intended.
At the same time, UIDAI came up with its own master stroke introducing the “Virtual Aadhaar ID ID (VAID) proposition which has changed the scenario of security in such a manner that one of the key argument against Aadhaar that it leads to breach of privacy has been put to rest.
Naavi had been suggesting for a long time that the principle of “Regulated Anonymity” should be applied to secure Aadhaar and actually hoped that this would be a good commercial business proposition to be used by an enterprising private business entity. Now Aadhaar by introducing the system of VAID has come up with its own version of “Pseudonomization” which would perhaps take the Privacy protection up by several notches.
The VAID system is expected to be in operation by March 2018 on trial basis and mandatorily by June 2018 unless some extension is given. Once the system comes into use, all KYC agencies will have to be prepared to use the VAID which may be a 12 digit randomly generated number which is mapped to the real Aadhar ID of an individual for all their KYC enquiries.
In other words, the KYC authority will not receive the real Aadhaar ID for its KYC purpose but receive only a randomly generated, changeable VAID number. This may perhaps be forced by UIDAI by mandating that the AUA/KUAs donot shall stop using the real Aadhaar ID for any KYC queries.
As for the users, they will have the option of generating a VAID against their real Aadhaar ID and ascribe it a date of expiry or designate a specific one time purpose. Such number would meet the requirement of SIM card verification or even Bank account verification.
How Virtual ID secures the system
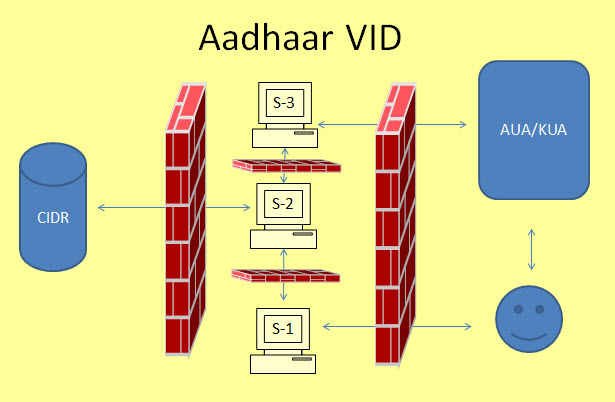
The exact architecture that UIDAI may use for the purpose is not known and need not be made public. However, it may consider the following features.
(P.S: This diagram is only an illustrative representation of a suggested architecture. This is not what UIDAI may implement)
The first change could be that access to CIDR will be only through an internal system and access by AUA/KUA would be stopped at an intermediary server.
Public will access a Virtual ID generator (S-1) service as and when they want. They will provide the real Aadhaar ID to this server and obtain a Virtual ID. This ID will be randomly generated and will have an expiry tag and stored in another system. S-1 will then deposit the information to S-2 where a map of Real Aadhaar ID and Virtual Aadhaar ID is maintained and updated with a history of VAIDs associated with a given Real Aadhaar ID.
When a user requires a service, he will provide only his VAID to the AUA/KUA who will send their request to another exclusive server of UIDAI where the request will be processed (S-3). This server will push a request to S-2 which will re-identify the VAID and forward the KYC request to CIDR,(Central Identities Data Repository). CIDR will push the required information back to S-3 for onward transmission to the AUA/KUA.
In this structure, S-2 which holds the map of the real Aadhaar ID with the Virtual Aadhaar ID will be accessed only by internal servers one accessible to Aadhaar users and the other accessible to the AUA/KUAs.
S-1 will only generate VAID and does not store any data after the process is over. CIDR is accessible only from S-2. S-2 will not hold any data other than the mapping of the real ID and Virtual ID. S-3 will allow passing through of Virtual ID and the KYC information but will never access the real ID.
S-1 and S-3 will be only transaction servers and need not store any data except in transit. Firewalls will manage the access to different servers and ensure that Aadhaar demographic or Biometric data is not accessed by any outsiders except through queries passed through S-2.
How Biometric Security Can be fortified
Presently, the Aadhaar has a record of 10 finger prints and iris scan for biometric identity purpose. To this multiple face parameters may get added with the new addition of the Face recognition feature. Face recognition in intended to be used as an alternative biometric in cases where finger print recognition fail so that false rejections can be reduced.
Additionally, we can consider that one or more Face parameters would be an add on to the many biometric identification parameters (10 finger prints+Iris scan). Totally therefore there may be around 11 plus biometric parameters which can be used for authentication.
Considering the possibility that as of now some biometric data might have been compromised, or biometric devices may be manipulated for a store and replay attack, UIDAI may consider a “Double/Multiple biometric authentication” on an “Adaptive Authentication Principle”.
Under this system, biometric of one finger is first obtained. When this is successful, the server may randomly chose another biometric feature to be provided with or without mobile OTP as well. With such a system there would be simultaneously three parameters that are verified for authentication and the second authentication would be a random variable and provide a defense against most of the normal attacks.
Assuming that UIDAI has other security features already installed for preventing the store and replay attack, the addition of a random additional biometric parameter based authentication will fortify the current system and make an enormous improvement in the system.
Since it is possible to get the biometric device ID and its location as a transaction input, the adaptive authentication can be configured with the known behavioural pattern of the user as is done in credit card transactions.
One issue that needs to be tackled in the suggested system is the latency of the transaction and connectivity. But this is a challenge that can be handled and should be handled in the interest of security.
(P.S: I presume that the current team of UIDAI consists of more accomplished information security experts than the author and hence what is discussed above may be steps which are already in place. They are however discussed here to inform public that security of aadhaar is feasible.)
Naavi