What
Motivates an Individual to adopt Security?
Naavi
[This
article is in continuation of the earlier article titled
“Theory of IS Motivation based on
Behavioural Science” published in these columns]
Motivation
has been a subject of intense interest in corporate circles since a long
time. Management experts have mainly discussed the behavioural science
aspects of Motivation from the point of view of employee productivity.
There have been many
theories of motivation trying to explain how and why a human being would
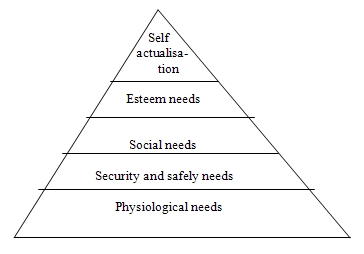
work. One of the most popular motivation theories has been the Maslow’s
theory of “Hierarchy of needs” which states that human beings have certain
“needs” and if a work satisfies those needs, they get motivated. The theory
also holds that the different motivational needs can be classified into
five categories stacked one above the other in the form of a “Pyramid” and
a person has a tendency to fulfill the needs in a specified order. To
demonstrate the theory, Maslow depicted his principle in the form of a
pyramid as shown below with the Physiological needs at the bottom and Self
Actualization needs at the top.
This
theory cannot directly help us identify “What motivates an IT user in
adopting Information Security practices”. One way we can link Maslow’s
theory to Information Security Adoption is by considering that “the
existence of a person is threatened by non adoption of security practices”
and hence it falls in the category of “Security and Safety needs”. This
happens when non adoption directly leads to a loss to the concerned person.
In fact information
security requirements directly contradict the “Social needs” since security
prohibits “Sharing” of information (such as passwords) while the need for
“Social Belonging” strongly supports sharing of information amongst the
people around. Also, it is difficult to identify the relevance of
Physiological needs and Esteem needs. Self actualization is a generic
factor and may be considered relevant.
In view of the
incongruence of Maslow’s theory of motivation to explain the behaviour of
IT users in adopting IS we need a different approach. None of the other
management theories also are suitable for the purpose.
The undersigned has
therefore propounded a different theory titled “Theory of Information
Security Motivation” modeled on a “Security Pentagon”, the features of
which were explained in an earlier
article.
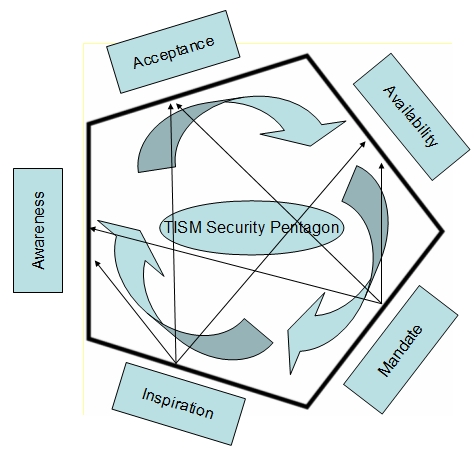
In brief, this theory
states that the motivation for Information Security (IS) comes from five
factors namely
- Awareness
- Acceptance
- Availability
- Mandate
- Inspiration
Also the theory states
that these needs are not stacked in a hierarchy like in the Maslow’s theory
and for modeling purpose they are better represented as sides of a Pentagon
as shown below.
It is also part of the
theory that the tendency for adoption of IS practices is to flow from
Awareness to Acceptance to Availability to Mandate and Inspiration. However
it is also accepted that “Mandate” and “Inspiration” are independently
capable of triggering awareness, acceptance and availability.
Out of the five parameters
of motivation, three namely Awareness, Acceptance and Inspiration refer to
individual who is being motivated while Availability is an organizational
influence on the motivation while Mandate is a regulatory influence on the
motivation.
This theory therefore takes
the individual, the organization and the environment in understanding the
motivation for adopting information security practice.
Awareness, Acceptance and
Inspiration may be considered as “Internal Motivators” for an individual.
“Inspiration” is like
the self actualization need propounded by Maslow. When a person’s
acceptance of IS needs is so strong, he becomes committed to adopt the
standards with or without any body else requiring him to do so and with or
without others funding the availability or forcing him with a mandate.
Though this is entirely at the control of the individual, Inspiration is
linked at the end of the chain of five parameters since reaching there
requires maturing of an individual through own experience which comes out
of “Availability” and also the realization of at least the Perceived
Mandate” from the external society.
What this theory means is
that “Awareness” is the foundation of all IS adoptions. IS cannot be
introduced without creating “Awareness’. Mere “Awareness” is not however
sufficient for adoption. The subject has to “Accept” the prescription. It
is in the conversion of “Awareness” to “Acceptance” that management
theories of motivation such as Maslow’s theory can have relevance. For
example, after creating “Awareness” if there are incentives for adoption,
then a person may get motivated.
One of the methods the
undersigned has adopted to increase conversion of awareness to acceptance
in his training is to introduce a system where the trainee signs an
"Ethical Declaration" where he binds himself in writing to follow the
prescribed security practices. This is to increase his level of commitment.
In the IS domain, “half
adoption is no adoption” and "Security is as strong as its weakest link".
Hence one cannot be satisfied at achieving the motivational level of
“Acceptance”. The system has to look at other factors which are required to
convert “Acceptance” to “Availability” where the security implementation
tools are available. For example, a person may like to protect his computer
against the latest virus. But he can proceed only if a suitable anti virus
solution is available to him.
Availability is generally a
matter of “investment” whether at the personal level or at organizational
level. Hence it is considered as “External Motivator” along with
“Mandate”.
"Mandate" refers to the
kind of regulatory push that is provided by legislations such as the HIPAA.
The realization that “Mandate” has a useful role to play in IS motivation
is a factor which integrates the McGregor’s theory of X and Y type of
persons used in management. This theory states that an organization
consists of two types of persons, one who needs to be pushed to performance
and others who are self motivated . Mandating as a IS motivational factor
addresses the requirement of the X type of persons while “Inspiration”
recognizes the presence of Y type of persons.
The Theory of Security
Pentagon propounded by the undersigned therefore fully in compatibility
with the McGregor’s theory applied in this context.
The Theory of Security
Pentagon recognizes a specific role for “Mandate” which is applicable both
to an organization as well as to the State which wants security culture in
the community. “Mandate” helps people to “rationalize” why the seemingly
inconvenient security prescription should still be adopted. It helps fight
the natural tendency not to adopt to control often fired by the “technology
intoxication” of the IT users. Without “mandate” security adoption will be
painfully slow and perhaps never reach the desired level where the society
can feel safe.
One aspect of "mandate"
which we should remember is that even "mandate" for adoption of security
should ideally follow in the sequence of Awareness, Acceptance and
Availability. Otherwise there will be undesirable consequences.
An example in India
regarding mandating of the use of "Digital Signatures" in
authentication of certain documents (eg: MCA returns). This mandatory
procedure was introduced in India when there was lack of awareness of how
to use Digital Signatures in the user community. This has lead to many
users delegating their digital signatures to their auditors in gross
violation of law and endangering the very acceptability of the system as a
trusted system of e-document authentication in law.
Further the availability of
digital signing tools is still inadequate in India. Many digital
certificates are not compatible with the current OS. All this affects
"Availability" and therefore non implementation of digital signature which
is otherwise an excellent tool of IS.
The study of IS motivation
on the suggested framework of the Security Pentagon as proposed by Naavi
helps an individual or an organization to find better ways of adopting to
the security environment.
These are early days in
the history of this new theory and the concepts need to be explored,
debated and refined. This article along with the earlier one are an attempt
to clarify the thought process behind the theory for further refinement.
We know that “Behavioural
Science” is a subject to which only the top management in corporate circles
are often exposed and a majority of IT professionals may find it strange
that there should be a discussion on the subject called “Behavioural
science of Information Security”.
But most technology persons
have in the recent times come to accept that there is a “Human Factor” in
IS management and not everything in IS can be implemented purely by
technical measures. It is therefore not far that they will also realize
that “Behavioural Science” may hold cues to many of the otherwise
unexplainable traits of employees resulting in security breaches.
May be it is time for IS
Managers to take up Behavioural Science Courses to understand and
appreciate the inter-disciplinary concepts such as “Behavioural Science
aspects in Information Security”.
India is in the threshold
of a major change in the Cyber Laws which affect Information Security and
this theory highlights the need to support the mandated security measures
with appropriate "Awareness creating " and "Acceptability building"
strategies besides creation of suitable tools.
Naavi has in the past
worked on a Karnataka Cyber Law Awareness Movement and is now leading
a Karnataka Cyber Security Movement. "Acceptance" may follow in due course.
If these efforts are to result in action on the ground, IT companies need
to come forward to provide "Availability". Naavi is also leading an action
plan for adoption of security practices in Cyber Cafes based on the model
of the Security Pentagon. Accordingly, awareness is being created through
the Karnataka e-safe programme. Acceptance and Availability is being
addressed through a specific software system which is administratively
beneficial to the Cyber Cafes and also provides some benefits to the
regulators. The time is now ripe for "mandate" to follow through
appropriate Cyber Cafe regulations so that there would be a synergistic
effect in bringing about an accelerated implementation of information
security in the State.
Na.Vijayashankar
29th September 2009
Comments are Welcome at naavi@vsnl.com


