Theory of
IS Motivation Based on a Behavioural Science Approach
by
Naavi
Information Security
Practice has evolved over a period from a pure technical perspective to
techno legal perspective. While the market is slowly absorbing this
transformation, a new dimension of Information Security Management is
calling for serious attention. That is the “Human Behavioural Aspects of
Information Security Management”.
Naavi has been in the
forefront of defining the transformation of Information Security Management
in India from the technical perspective to Techno Legal Perspective. He has
introduced the concept of Defensive Legal Protection (DLP) and Offensive
Legal Remedy (OLR) approach to augment the present system of Information
Security Management based on Disaster Recovery Plan (DRP) and Business
Continuity Plan (BCP). Accordingly Corporate entities are urged to
introduce a new Information Security Framework based on not only installing
the most optimal technical security measures including access controls,
encryption, IDS, etc, but augmenting it with compliance of Cyber Laws.
Naavi has also developed an Information Security Framework , exclusively
for Legal Process Outsourcing Companies called
LIPS 1008 and also a more generic framework for Techno Legal Compliance
under the new Information Technology Act (2008 version) called
IISF 309 which is due to be effective anytime.
Now for the first time in
India, an attempt is being made to approach the Information Security
implementation issue from the perspective of Human Behavioural Science
perspective.
The transformation from
the technical perspective of IS to Techno legal perspective of IS was based
on the appreciation that technical IS can never be perfect and hence
breaches are a definite probability leading to legal liabilities. Hence the
Techno legal IS approach was developed to cover the exceptions where the
technical security is breached and a legal liability is created against the
information owner.
Now after a few years of
intense interaction with the information security community in which Naavi
has been discussing the need for a changed approach at corporate level we
are seeing an emergence of an appreciation at the IT professional forums
that they need to understand Cyber Laws and incorporate the principles of
Cyber Law Compliance into the technical designs of IS systems. In the
coming years we expect to see a convergence of Cyber Law professionals and
IT professionals and the tribe of Techno legal professionals will be on the
increase.
However, during the course
of these interactions, Naavi has found that in achieving the Techno legal
information security objectives, there is a “Human Behavioural element”
that plays a significant role. The adoption of the Techno legal
prescriptions get influenced by these human factors which the society needs
to understand and incorporate in Corporate IS policies.
The experience which Naavi
has gained through hundreds of interactions with corporate IS professionals
has developed into a thought process represented here putting forth a
hypothesis on how Companies and Corporate employees get motivated for the
adoption of Information Security in their day to day affairs. This
understanding may help in strategizing IS policies in an enterprise. The
thoughts are in the preliminary stage of development and will be refined
and expanded in the days to come with inputs from like minded persons. For
the purpose of identification, this thought process will be referred to as
“Theory of IS Motivation”. (TISM).
The objective of TISM is
to understand the human behavioural factors that affect implementation of
Information Security in an enterprise using “Information” as a key asset.
The theory can be
visualized through the TISM Security Pentagon shown below:
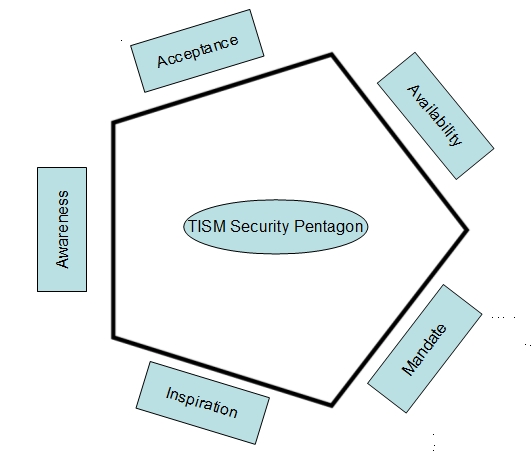
Fig
1: Five Elements of Security Implementation
Naavi’s
Theory of Information Security Motivation is built on the premise that
Information Security adoption in an enterprise is built on five factors
namely
- Awareness
- Acceptance
- Availability
- Mandate
- Inspiration
The natural progression of
the enterprise in implementing the Information Security practices is from
Awareness to Acceptance to Availability to Mandate and Inspiration. However
the relationship of these different elements of motivation is not built
one above the other as in the Maslow’s hierarchy of needs.
The Five Elements
Though awareness is a
foundation element without which the IS implementation cannot be proceed in
an organization, we consider that it is better placed as one of the five
boundaries of the Security Pentagon in the model rather than the base of a
pyramid. Awareness of IS at the top management level helps in the
enterprise allocating necessary resources and making security available in
an organization.
Awareness at the user
level is also an important building block of the IS system since no IS
practice can be successful without the participation of the users.
The reason why “Awareness”
is not put as a foundation block over which other elements are developed is
that the IT user industry is dependent on systems supplied by other
vendors. Many times the users are not experts in IT but are domain persons
to whom the tools have been given with operational training of how to use.
In such cases the person using the IT device may not be aware of security
requirements but the software may be having an inbuilt security
implementation based on the vendor’s awareness of what the user needs.
Awareness however cannot
be passive information dump on the IS managers or users for it to be an
action point. There are many instances where a person is aware of an IS
policy but does not care to follow. Other needs such as convenience
override his readiness to adopt security practices. The reason is that the
person who is aware might not have “accepted” the security requirement.
Hence “Awareness” needs to be translated to “Acceptance” before any action
can be motivated.
Once the awareness of
security is present in an organization and is also accepted by the target
group, the group will search for means to implement the security. At this
stage the availability of security tools become relevant. At the management
level this is the time for budgeting the acquisition of security products
and services. In many organizations, the implementation stalls at this
level because the solutions may not be available or even if available may
not be affordable. The hurdle can be passed after further awareness and
acceptance is created on how critical is a security requirement, what are
the consequences of not introducing the relevant security requirement etc.
Once the new level of awareness and acceptance is high enough to overcome
the barrier, the implementation may move forward.
We can therefore say that
the implementation tends to move in waves trying to move from one element
to another crossing the barriers at each level when surge of energy is
available. If the energy is not strong enough to cross the barrier, the
implementation remains at the previous element only.
The fourth element of the
Security Pentagon is “Mandate”. This is the forced introduction of security
practice as it happens when it becomes legally necessary to introduce
reasonable security practices to be in a business. For example the Data
protection Act or HIPAA mandates certain security practices or otherwise
the enterprise may have to vacate the business. Again to reach this level
and implement security practices, appropriate awareness and acceptance
should be first crossed.
Just as security
implementation can precede awareness in certain cases as explained earlier,
in some cases, the “legal mandate” may initiate IS practice though the
management might not have accepted it whole heartedly as beneficial to
itself. Based on the mandate the management may have to make available the
security prescriptions. Therefore “mandate” precedes “availability” against
the natural progression as indicated in the diagram through small arrows.
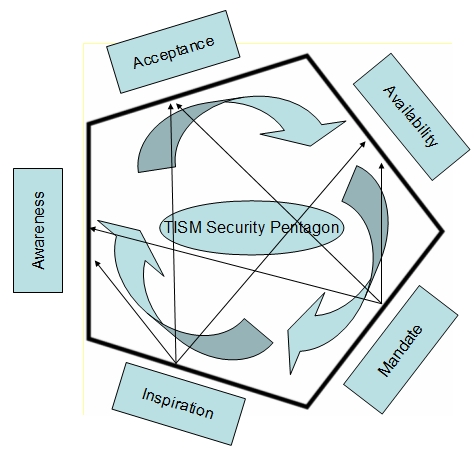
Fig 2: Progressions
and Influences Between different States of Motivation
“Mandate”
can itself trigger an awareness building exercise, create acceptance and
also availability. This sort of development can be clearly seen in the
HIPAA related security prescription as well as the ISO audit
implementations. We foresee this to happen when ITA 2008 (Information
Technology Act 2000 as amended in 2008)
The fifth element of the
Security Pentagon is termed “Inspiration”. What is meant by this element,
is that certain individuals or organizations donot wait for “Mandate” to
introduce security measures. They are so self motivated that they are fired
by an inspiration to be role models and initiate security practices
entirely on their own initiative. This may be a leadership characteristic.
This is similar to the “Self Actualization” need which Maslow propounded in
his theory of motivation.
Inspired persons are not
even constrained by “Lack of availability”. They create availability
through their own initiative. Similarly, they trigger awareness campaigns
and drive their colleagues towards acceptance through their own adoption
and sincere belief. Normally such inspiration comes from the top management
such as the CEOs. But it can start anywhere else too.
How the Theory can be
used in practice
The Security Pentagon model
can be used both within an enterprise as well as in other IT frameworks to
understand where they stand in respect of implementation of security in
their organization or network. It can also help in finding out what is
preventing implementation of security, so that appropriate corrective
actions can be taken.
Each person in an
organization can be mapped to the different levels of implementation of
“Awareness”, “Acceptance” or “Inspiration”. Their training requirements
can be drawn up based on the expected levels at which an employee is
targeted to reach. The HR department can design appropriate tools for
testing the motivation levels and accordingly develop training plans.
When security auditors
rate an organization, they can develop models of evaluation based on the
mapping of the employees to the motivation status of Awareness, Acceptance
and Inspiration.
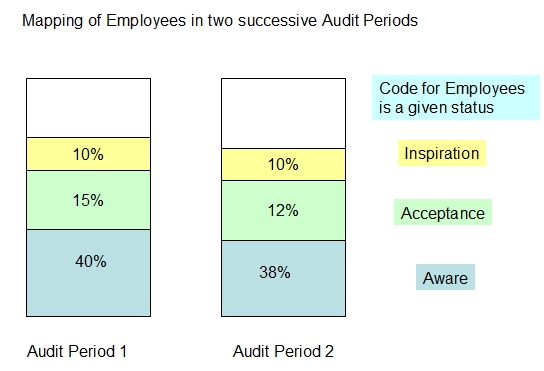
Fig 3: Audit
Observations
As an example, let’s see
the mapping of employees against three motivational status positions of
Awareness, Acceptance and Inspiration shown above. The audit indicates that
out of the total of 100% employees, in the audit period 1, 10% were
classified as being in the self motivated inspirational status while 15 %
were in the “Acceptance level”. 40% more were classified as being “Aware”
so that a total of 65% were aware and 35% were below the awareness level.
In the second audit period, on a percentage basis, while the Inspirational
level employees did not change, the acceptance level employees reduced to
12% and the overall aware employees were 60%.
The management can try to
interpret these results and compare it with the efforts and investments
made by the firm in awareness training, during the period between the two
audits. It is possible that a set of new employees could not be given
awareness training and hence the overall awareness level could have
dropped. The drop in the acceptance level could be because of dropping off
of enthusiasm due to lack of “Refresher Training” for employees who had
already been trained earlier. Such analysis could provide a measurable
scale for determining the ROI of the IS investments.
Where the regulatory
authorities (or the top management within an organization) consider that
the IS implementation in the community is below the acceptable levels they
can try tightening the mandatory provisions.
For example, if Cyber
Cafes are not complying with the regulations, the State Government can make
it mandatory and introduce a licensing system based on the fulfillment of
mandatory provisions. A corporate entity can make passing of an Awareness
test mandatory for promotion or introduce sanctions to punish non
compliance.
Top Management can
consider the status of making the security implementation tools “Available”
to the users in the organization either on the basis of the “Inspiration”
levels of the decision makers or because of “Mandate” as they are aware of
and accept.
Managements can consider
additional investments in various security components if they need to give
a push to the IS implementation.
Thus several issues of IS
management can be addressed using the Security pentagon model.
At present many
organizations which have high stakes in IT are low on awareness
particularly of the Techno Legal Security requirements. It is for this
reason that many offences take place in an organization in which the
employees are involved and causes problems for the superior officers and
the organization.
Company’s can also study
why their investments in “Awareness” donot always translate into
“Acceptance” and take appropriate corrective steps. This may require an
enterprise level survey from time to time suitably structured to elicit the
required information.
It is easy to measure how
many employees of an organization have been made “Aware” but it is not easy
to measure how many of them have reached the level of “Acceptance” or how
many are “Inspired” and self motivated. Suitable exercises on the lines of
management games need to be developed to understand the number of employees
who have graduated from awareness to other levels.
It is possible that some
individuals may be at awareness level for 10 concepts but at acceptance
level for only 5 concepts and at Inspiration level for one or two concepts.
The individuals may therefore exhibit a mixed status and their levels may
have to be represented like what is normally done in the development of an
“ego gram” in TA analysis. These are subjects of advanced study of the
model.
Similarly it would be
interesting to study how “Mandating” affects “Acceptance”. Will the users
show a tendency to comply? or tendency to revolt? Does this have any
correlation to the Technology levels of the users or power structures in
the organizations? .. are also issues to be observed.
Like all models, this
Pentagon model of Information Security Motivation will be a tool to
organize the IS efforts of an organization and help in resolving some
difficult to understand reasons which seem to hinder IS implementation.
More research can throw up
data on how the model can be applied to a given situation and how the
observations can be quantified and measured.
Na.Vijayashankar
27th September 2009
[Comments
Welcome]
Comments are Welcome at naavi@vsnl.com
Also Read
:
What Motivates an Individual to adopt Security?


