The DDOS attack on the Internet service provider Dyn which suffered a massive DDOS attack on October 21 with 1.2 Terra Bytes of data directed from about 145000 CCTV/DVR instruments working as a botnet shook up US internet and brought down many critical services. (Dyn headquartered in New Hampshire offers DNS services to resolve internet addresses and when it fails, the users were unable to reach several popular websites.)
(Report in Wired.com). ( Also see earlier report on OVH attack in naavi.org)
While the DDOS attacks on DNS service providers or others is not new, what attracted attention in this case was that the botnet consisted not of computer zombies but the CCTV cameras and DVRs working within many corporate networks and public utilities. These devices working on IP connections send the images captured to a central server and being a video files, the data size is large. Most of these devices are configured with a default password as supplied by the manufacturers which is either known or can be easily broken.
The available network of such devices with IP addresses are easily searchable in some search engines such as Shodan and therefore an easy fodder for those who are trying to do mischief.
In fact just a few weeks earlier, another similar attack had been launched on OVH a web hosting company. The attack on OVH failed to evoke preventive steps which lead to the next attack on Dyn. Even now if one searches Shodan search engine it spits out the IP addresses of about 27000 cameras in Germany, 26000 in US and about 1000 in India. Hackers use an exploit that can bruteforce these devices and divert the feeds to a target server to cause a DDOS attack.
The Shodan search engine also showed 48 Banking hosts in India whose IP addresses could be easily obtained for further analysis. May be these are not exploitable, but it indicates how the internet facing devices may easily be open to attacks from unknown persons. While servers used by Banks and other responsible users may have a tough password which cannot be easily broken, the same cannot be said of IoT devices used by common people.
The “Mirai” malware is one of the tools with which these DDOS attacks are being carried out. One can see the latest Mirai attack map (fossbyte.com) and how the attacks are spread all over the globe including India. 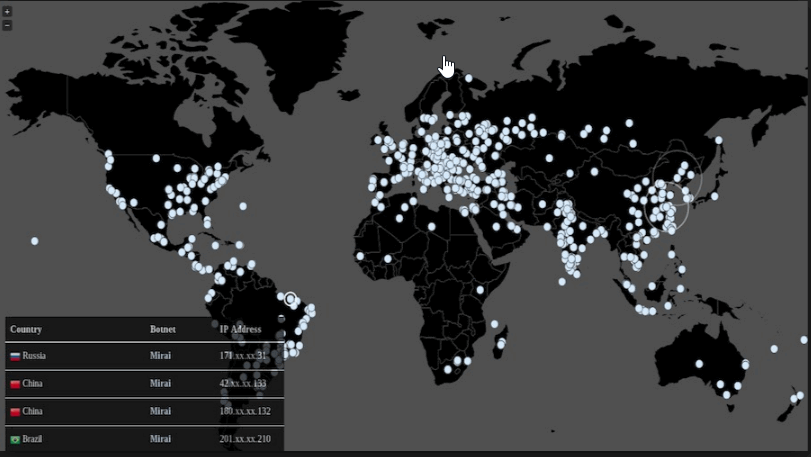
Now the news has just come that the latest Mirai Botnet attack has brought down the internet in the entire West African country of Liberia. (See report here). This could be a test attack and would be followed by another attack elsewhere soon.
In the map above India is showing a huge number of attacks.
A realtime Mirai botnet infection activity shown in the adjoining picture shows intense activity in India including around Bangalore. How these 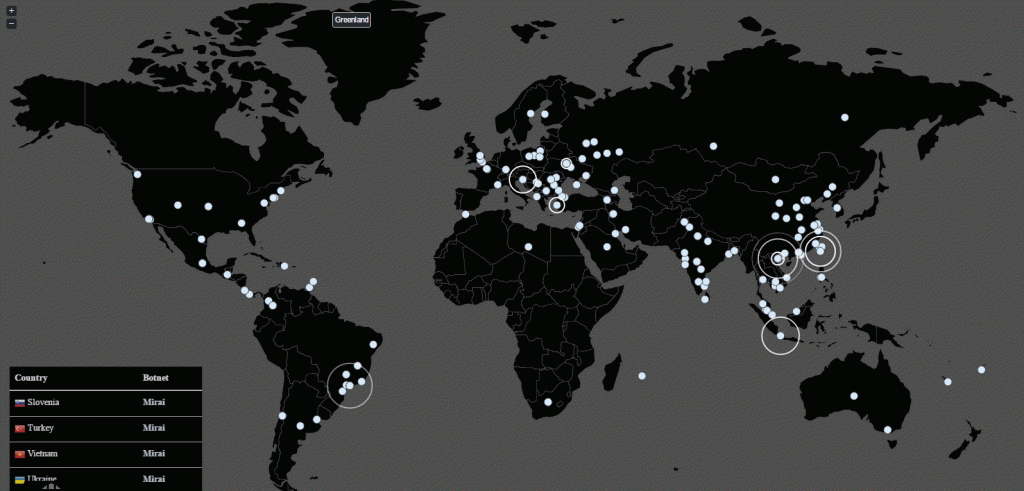 infections will play out is anybody’s guess. If there are any further DDOS attacks in which the devices owned by the infected systems participate, there would be a “Cyber Crime” incidence and possible prosecution under Section 66 read along with Section 79 of ITA 2008.
infections will play out is anybody’s guess. If there are any further DDOS attacks in which the devices owned by the infected systems participate, there would be a “Cyber Crime” incidence and possible prosecution under Section 66 read along with Section 79 of ITA 2008.
If the attack is on a nation crippling attack like the Liberian attack then such devices would be exposed to the charge of a “Cyber Terror Attack” or participating in a “Cyber War” on an otherwise friendly country.
Information Security professionals working in companies in which any Internet facing devices are being used need to first check if these devices are secured from external attack. Each CCTV exposed to IP should be secured like a “Server” containing “Confidential Data”.
At a time we in India are facing cyber attack challenges from Pakistan and China, it is essential that we take care that our assets are not part of an international botnet that can cause DDOS attacks elsewhere.
Some of these devices may actually be owned an operated by Government agencies where the security awareness may be insufficient. Just yesterday, it was reported that the Digital India website had been hacked indicating the security vulnerabilities of high profile websites maintained by the Government. I will therefore not be surprised if there are a number of IP devices including CCTVs in Government hospitals, Departments, Public sector companies and also with the Police as part of traffic management systems which are capable of being compromised and made part of the Mirai botnet.
I therefore urge the Government to undertake a study of the security of IP connected CCTVs to start with and secure them before it is too late.
Naavi






