I refer to the earlier post on “WhatsApp moment in Indian Financial Services” in which the views of Mr Nandan Nilekani on how the financial services market in India is transforming.
One of the changes that the new mobile payment systems such as Paytm has done is that a user gets on to this system merely by downloading the app and identifying himself with the mobile number. In a way the mobile service provider completes the KYC process which identifies the customer. If the KYC verification system of the Mobile Service Providers (MSP) is deficient, the deficiency will reflect as a security vulnerability in the financial system. There have been many instances where SIM cards have been issued to fraudsters with the use of fake ID instruments and therefore there is a serious concern if the financial services system becomes dependent on the MSPs for its security.
Mr Nandan Nilekani has indicted two other means of ID verification that is likely to support the Indian Financial system embracing the mobile payment systems. One is the e-KYC using Aadhaar and the other is using of the e-sign system.
Aadhaar based e-KYC System
The e-KYC system means, submit the Aadhaar number to UIDAI and obtain a copy of any Aadhaar holder. In practice most service providers donot make a query to the Aadhaar data base using biometrics of the person to be verified. They simply take a photo copy of the Aadhaar certificate and keep it along with the other documents.
This system deserves to be banned. If the Aadhaar based KYC is done on the basis of a real time verification of the biometrics with the Aadhaar data base, then the system would be more reliable. However, the Aadhaar based KYC may still be subject to risks such as the MIM attack and the confirmation received from the Aadhaar server lacks acceptable authentication.
e-Sign System
e-Sign system is being presently used in the DigiLocker system but in future could be used by others. This is a system where a user obtains digital certificate for one time use at a cost much less than obtaining the normal digital certificate valid for one year or more which is used for other purposes.
DigiLocker is a system introduced by the Government of India where a user can open the account quoting his Aadhaar number. The account can be used to store documents and shared with other authorized agencies whenever required with an authentication in the form of e-Sign.
Since opening of the DigiLocker account is based only on the quoting of aadhaar number and confirmation through OTP, the system is dependent on the mobile service provider’s KYC process. (DigiLocker provides for biometric based authentication but it is not mandatory).
Errors in the System
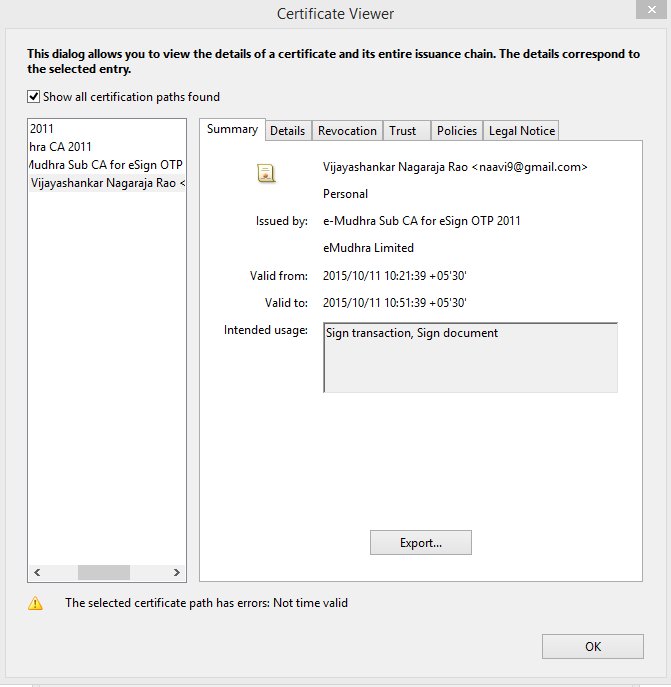
In order to verify the e-sign process, I applied e-sign on a document earlier uploaded to the store and then downloaded it. But the signature on the document stated “validity unknown”. When I explored the signature properties,it stated that “The signer’s identity is unknown because it has expired or is not yet validated”. The certificate itself showed validity for 30 minutes and the certificate was issued by e-Mudhra. However the revocation was not checked and showed up as an error. In other words, the e-sign on the document was not in a status to be relied upon.
Since this is an issue with the Digi Locker system, if a similar error is observed by a service provider relying on the e-Signed document submitted to him, he is likely to ignore the error.
We can however justify the errors as teething problems in a system under implementation, (or because the system is only on a test bed at present). But there is a deeper problem with the legal validity of of e-Sign system itself and if the Indian Financial Services system has to rely upon the DigiLocker system as Mr Nandan Nilekani expects lot of ground is yet to be covered.
Legal Validity of e-Sign System
The validity of the e-Sign system is supported by the notification dated 28th January 2015 which added a new item into the Schedule 2 of ITA 2008. This notification should be read with guidelines issued by CCA in June 2015 on the e-Sign process.
I have made an attempt here to decypher these two documents and understand the legal implications. It is possible that the intention of the Government might have been different and it might not have been properly worded in these documents. We may therefore be coming to an incorrect evaluation. But it is necessary for us to debate this issue since e-Sign process is likely to become the backbone of Digital India in due course and it needs to be legally on a sound footing.
We therefore look forward to receiving clarifications from relevant authorities to ensure that public have a correct understanding of the legal position of e-Sign as a valid authentication of digital documents under Section 3A of ITA 2008.
Notification of 28th January 2015:
The notification of 28th January 2015 under ITA 2008 states as follows.
Quote:
e-authentication technique using Aadhaar e-KYC service
Authentication of an electronic record by e-authentication Technique which shall be done by-
(a) the applicable use of e-authentication, hash, and asymmetric crypto system techniques, leading to issuance of Digital Signature Certificate by Certifying Authority
(b) a trusted third party service by subscriber’s key pair-generation, storing of key pairs on hardware security module and creation of digital signature provided that the trusted third party shall be offered by the certifying authority. The trusted third party shall send application form and certificate signing request to the Certifying Authority for issuing a Digital Signature Certificate to the subscriber.
(c) Issuance of Digital Signature Certificate by Certifying Authority shall be based on e-authentication, particulars specified in Form C of Schedule IV of the Information Technology (Certifying Authorities) Rules, 2000, digitally signed verified information from Aadhaar e-KYC services and electronic consent of Digital Signature Certificate applicant.
(d) The manner and requirements for e-authentication shall be as issued by the Controller from time to time.
(e) The security procedure for creating the subscriber’s key pair shall be in accordance with the e-authentication guidelines issued by the Controller.
(f) The standards referred to in rule 6 of the Information Technology (Certifying Authorities) Rules, 2000 shall be complied with, in so far as they relate to the certification function of public key of Digital Signature Certificate applicant.
(g) The manner in which information is authenticated by means of digital signature shall comply with the standards specified in rule 6 of the Information Technology (Certifying Authorities) Rules, 2000 in so far as they relate to the creation, storage and transmission of Digital Signature Certificate.”
Unquote:
The key points noted in this notification are:
1) e-authentication, hash and asymmetric crypto systems are three elements to be used.
2) Key pair to be stored on a hardware security module
3) Trusted third party shall be offered by the Certifying Authority which shall send the application form and certificate signing request to the Certifying authority
4) Issue of digital certificate shall be based on e-authentication
5) Form C information to be digitally verified from Aadhaar e-KYC service
6) Electronic consent of the Digital Signature Certificate to be obtained from the applicant
7) e-authentication guidelines to be issued by the CCA
Validating Aadhaar through ITA 2008
The first thing we observe in this notification is that the notification issued as a part of statutory law and added as a schedule to the ITA 2000/8 relies on Aadhaar e-KYC service. While the Supreme Court is yet to validate the legality of the UIDAI itself, the Government has already validated the Aadhaar e-KYC service for issue of Digital Certificate by a licensed Certifying Authority.
Use of HSM
The second key factor in this notification is a reference to a system of generation of the Key Pair on a HSM maintained by the Certifying Authority and not under the control of the digital certificate holder.
Both the above aspects need to be discussed in detail to assess the legal validity of the e-sign system.
Other observations
 The notification envisages that there would be a trusted third party who would be “offered” by the Certifying Authority but would be a different entity which would send the application form and certificate signing request to the Certifying Authority. The word “offered” may actually mean “appointed” or “sub licensed” but there is a clear indication that the trusted third party mentioned here has to be an entity different from the Certifying authority. In other words, a “Registration Authority” has to be licensed as a “Trusted Third Party” to operate the system including the HSM.
The notification envisages that there would be a trusted third party who would be “offered” by the Certifying Authority but would be a different entity which would send the application form and certificate signing request to the Certifying Authority. The word “offered” may actually mean “appointed” or “sub licensed” but there is a clear indication that the trusted third party mentioned here has to be an entity different from the Certifying authority. In other words, a “Registration Authority” has to be licensed as a “Trusted Third Party” to operate the system including the HSM.
In the e-sign system in DigiLocker, there is no party other than the Certifying Authority apart from DeitY which should be considered as owning the system. Since the notification itself was issued by DeitY, it can be presumed that it cannot be the trusted third party envisaged in this notification. From the copy of the digital certificate shown here, it appears that the digital certificate is issued by the Certifying Authority itself as a “Sub CA”. This does not seem to be in tune with the intention of the notification.
Circumstances indicate that the DigiLocker itself operates as the agency that submits the application form to the Certifying authority and is therefore the “Registration Agency”.
DeitY which operates as a part of the Government which has appointed the CCA and has a division namely NIC which itself is a licensed Certifying authority, being a Registrar for e-Mudhra appears to be a strange public private partnership.
Verification of Information in Application Form
The information in the digital certificate application needs to be verified from Aadhaar e-KYC service. We may note that we are talking of an application form to be submitted before the e-Signing certificate is to be issued to the aadhaar holder. Also the notification indicates that the information has to be “digitally verified”. It does not say “information should be authenticated”. In other words, the notification is suggesting that the application form need not be “Digitally Authenticated” either by the applicant or the Registrar such as the DigiLocker. In practice, the application form may get filled up directly from the aadhaar information already available with the DigiLocker. It is not completed by the applicant and verified by any trusted third party. This again appears to be a violation of the intention of the notification.
Electronic Consent for Digital Certificate
The notification also envisages that the Certificate should be “Consented” to by the applicant. This is equivalent to “acceptance” and “Publishing” of digital certificate as referred to under “Duties of the Subscriber” in ITA 2008.
However, the e-signing process in the Digi Locker does not (presently) go through the process of obtaining the consent of the applicant either with or without digital signature.
Inherent Contradiction
Since both the application for digital signature certificate as well as consent for digital certificate has to be “Digitally Signed” according to ITA 2008, the current process adopted by Digi Locker does not meet the requirements of law. These requirements cannot be met in future as well (without amendment to ITA 2008) since these are requirements prior to the activation of e-signing powers of the customer and cannot be authenticated by e-signing.
CCA Guidelines
The issue of digital certificates under the e-sign system is mandated to use “e-authentication” process which is described more fully in the CCA document on e-authentication. There is no indication that existing digital certificates of a subscriber (if any) can be used for e-sign process and the existing process is not enabled for the use of digital certificates already issued. The e-authentication process is therefore mandated on all users of DigiLocker.
The CCA’s document needs to be separately vetted for security considerations by Information Security professionals in detail and I invite the readers to submit their views for publication here. My own preliminary views on the guideline more from the ITA 2008 perspective is provided below.
Legal Validity of the CCA Guidelines
The CCA guideline identifies the trusted third party referred to in the notification as the eSign Service Provider or ESP. It also uses a term “Application Service Provider”. There is no clarity whether the Application Service Provider (ASP) and ESP are same or different. We can presume that ASP should be approved by the ESP through an approval process. There is a mention “agreement” (Refer para 2.1) without specifying between whom. We presume it is the agreement between the ASP and the ESP. Additionally there is a mention of an AUA (Authentication user Agency) and e-KYC agent of UIDAI. The ESP will be the AUA and e-KYC agent of UIDAI. In the Digi Locker case, there needs to be clarity on whether DigiLocker (or DeitY) is the ASP or ESP or both?
The CCA guideline says (Para 2.2.1) that the mode of e-authentication should be in accordance with Aadhaar e-KYC Services.
It appears that the Aadhaar e-KYC services envisaged in this guideline is different from what is otherwise defined by UIDAI. According to UIDAI, a KYC query is one where the information submitted by a user for verification which is queried with the UIDAI data base (preferably using the biometric) and obtaining the information which can be compared with what is submitted.
If the query is responded to based on OTP and not on biometric request, the system will in turn be dependent on the KYC of the MSP. Banks have adapted e-KYC system as detailed in the RBI Circular which envisages downloading of e-Aadhaar and using it as KYC document.
However, it appears that while making e-authentication subordinate to the Aadhaar e-KYC services, CCA presumed that e-authentication is some thing more than merely checking the information with the data base.
According to para 2.2.2 of the guideline, Aadhaar e-KYC service should provide digitally signed information which is also fulfilled when an e-aadhaar copy is downloaded.
What is additionally required under the e-authentication is perhaps the issue of a “Response Code” which should be recorded on the e-signing certificate application and should be preserved for 6 months online and further 2 years offline.
The application form should be electronically generated and programmatically filled up and submitted to the ESP.
According to para 2.2.3., the application form should be “authenticated by Aadhaar e-KYC services”. Aadhaar e-KYC service does not envisage digital signing of any content. It is only provision of confirmation of information available in the Aadhar records of a person. So what the guideline mean by “authenticated by Aadhaar e-KYC services” is difficult to understand.
Further the consent of the subscriber for getting a digital signature certificate should be obtained electronically. Currently the process of e-signing a document uploaded on DigiLocker indicates that no consent is sought from the document holder for the digital certificate.
The digital certificate issued for e-Sign is issued with a validity of 30 minutes but otherwise it is similar to the digital certificates that are issued for other purposes and valid for 1 or 2 years. If a user has to apply e-sign on a document, he has to first get the e-sign digital certificate. For this he has to first make an application to the ESP. It is obvious that any application made in the form of an electronic document needs to be authenticated by a digital/electronic signature. Hence unless a person already has a digital certificate, he cannot make an application for e-signature online. This is a fundamental flaw in the design of the e-sign system.
From the system as designed, it appears that the e-Sign digital signature application is submitted by the DigiLocker authorities and not the applicant. The locus-standi of the DigiLocker authorities to submit an application on behalf of the digital certificate applicant is questionable. The e-sign digital certificate would therefore be considered as “issued” without a valid application from the applicant and hence it would be not in accordance with ITA 2008.
Why CCA gave permission to the system as presently being suggested is intriguing and we need more clarification from CCA on their logic why they consider that the system is compliant with Indian law.
The legal validity of the HSM system
According to para 2.3 of the CCA guidance, the ESP should facilitate generation of key pairs on their Hardware Security Module and the Private key will be destroyed after one time use.
So far under the Digital Signature system, the generation of the private key-public key pair was done solely under the control of the subscriber and the Certifying authority would not have access to the private key even at the time of key pair generation. It was for this reason that the digital signature was considered “Non Repudiable” in law.
In the e-sign system, the HSM is maintained under the control of the ESP. Hence it is impossible for judiciary to consider that the private key was always under the control of the subscriber. Hence the non repudiable nature of the e-sign is not sustainable on a Court of law.
e-Sign is therefore an inferior form of authentication and cannot be equated to digital signature in terms of evidence in a Court of law. In a way the introduction of such a system by the Government actually dilutes the credibility of the digital signature system in general and Courts may decide to question the non-repudiable nature of the digital signature system in India.
The provision on destruction of private key after every use is also little suspect in law. Obviously it has been suggested as a measure of security. However, “Private Key” belongs to the subscriber and the ESP has no right either to create it nor to destroy it.
According to Section 43 of ITA 2008, it is the duty of the subscriber to exercise reasonable care to retain control of the private key and take all steps to prevent its disclosure. Also, If the private key has been compromised, then, the subscriber shall communicate the same without any delay to the Certifying Authority .
Further without the private key it is difficult to understand how the e-sign can be verified subsequently.
The CCA guideline is therefore directly in conflict with ITA 2008 and has no legal validity.
In fact, the system as suggested may impose criminal liabilities under ITA 2008 on the innocent subscriber of e-sign merely because the private key compromise is not reported and revoked. If any fraud occurs with the use of e-sign, the primary liability of the fraud would be on the ESP.
It is surprising that CCA should have over looked this provision of law.
Security Requirements
The CCA guidance lists certain essential security requirements under para 2.7.
I request my friends from IS community to analyze and comment on the same.
I look forward to CCA providing necessary clarifications or withdrawing the e-sign notification. CCA should also immediately revamp is advisers who are giving them wrong advises which are contrary to ITA 2008 .
Coming back to Mr Nandan Nilekani’s prediction that we are in a WhatsApp moment in Financial services, I would rather say that we may be in a Napster moment where the business may pick up fast only to be shot down because the foundation may collapse due to legal considerations. Just as Napster collapsed because of Copyright violations, systems built on e-Sign validation may collapse because Courts may hold it illegal sooner or later.
I wish Digital India managers recognize that DeitY is making mistake after mistake, identify who is responsible for series of mistakes and take corrective steps.
Epilogue
The concept of e-sign as a low cost option to digital signatures available on call is good. But the way it is suggested to be implemented is incorrect and ultra-vires the ITA 2008.
I am not discussing here what could be an ITA 2008 compliant system which meets the requirements of e-Sign but if any Certifying Authority is interested in developing such a system, I would be willing to discuss the structuring of such a system.
Naavi
P.S: The part of the article referring to HSM stands corrected after the revised notification of 30th June 2015 deleting the use of HSM.






