How to
Recognize a Phishing Mail
Phishing has been a
constant source of concern for Netizens. In India, due to the
weak security systems adopted by Banks, Phishing has become a most
convenient form of robbing innocent citizens of their money in
the Bank.
There is a reasonable
suspicion that many
employees (particularly the contract employees involved in
marketing) of Banks are involved in the Phishing racket and
facilitate phishing frauds.
One way by which Phishing is aided
and abetted is by opening accounts for Phishing mules ignoring
the KYC norms or trying to follow the KYC instructions in letter
but not in spirit.
Second method which is
suspected to be used by rogue Bank employees is to access the
passwords internally but still simply drop a phishing mail to
the target account. Then the fraudsters use the
acquired password with or without the customer answering the
Phishing mail. When the customer later
complains, he will be questioned..
"Have you received a
mail asking for password?"..
An honest customer has
to answer.. "Yes".
Immediately the Bank will
say... "You violated our condition on Internet Banking and
hence you alone are responsible".
This explains why may
Phishing incidents happen even when the customer does not answer
the Phishing mail.
Since a similar situation
may be simulated with the use of some Trojans, it is
impossible except in rare circumstances with forensic help to
prove the innocence of the customer. Banks take advantage of the
inability of the customer to defend himself to escape liability.
It is therefore essential
that Netizens should train themselves about Phishing and be able
to recognize a Phishing mail. This is ofcourse easier said than
done since fraudsters keep using different methods to hoodwink
Netizens and even experts some time fall prey to such e-mails.
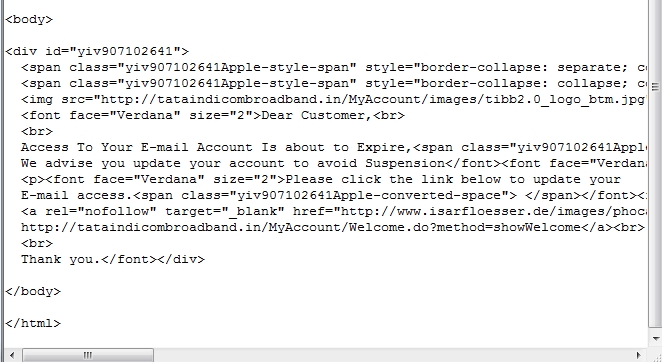
While Phishers may use
multiple strategies to obtain the password, here is an example
of how Phishers may first try to acquire your e-mail password.
This may also be the first step to acquire the Banking password
since the Phisher may just go to the Bank website and ask for
change of password. The request may then be routed through the
e-mail with a link to the password change page. In mobile
Banking situations, the PIN may be mailed to the e-mail address.
Getting control of the e-mail is therefore getting half the key
to enter your Bank account.
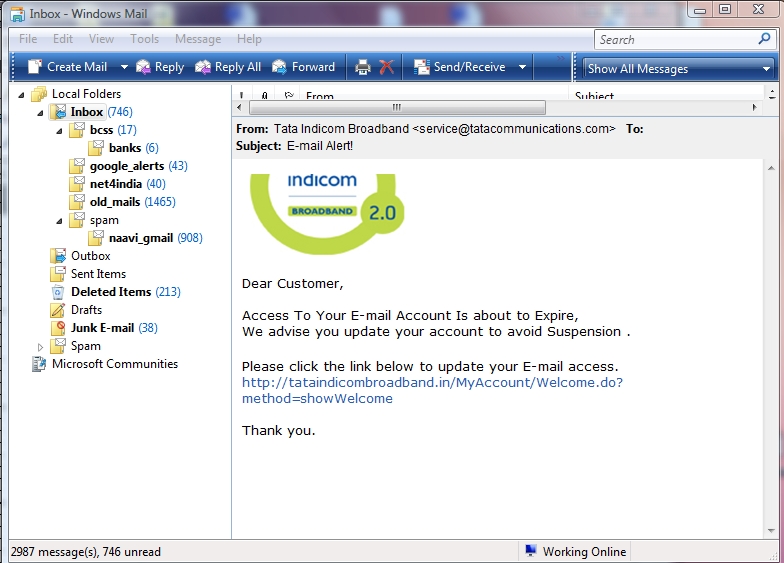
The mail appears normal except that the "To"
field does not contain the name of the recipient. This is the
first check the recipient should run. Some times this field may
show "Undisclosed recipients". There are exceptional cases of
"Targeted Phishing" where the recipient's correct e-mail address
is displayed and one has to then look at other indicators.
The second and more reliable indiator is the
link to which you are invited to click. In the above mail the
link as shown in the e-mail is
http://tataindicombroadband.in/MyAccount/Welcome.do?method=showWelcome
.
Though the link appears genuine, if the mouse curser is moved to the http link
provided in the mail, one would see in the bottom of the window
the real link to which you would be taken to.
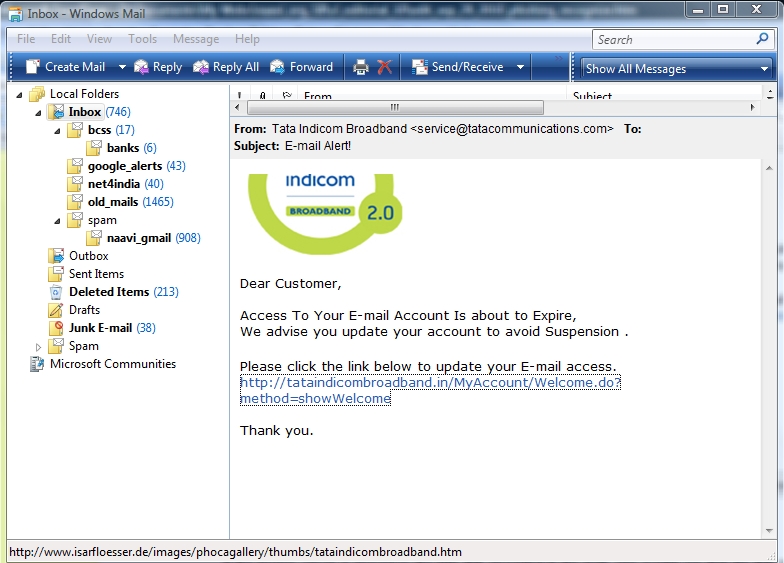
The link available in the mail points to
http://www.isarfloesser.de/images/phocagallery/thumbs/tataindicombroadband.htm
Obviously one can see that this URL does not appear to have any
connection with Tata Indicom.
If we click on the link, the Netizen would
reach the following page which looks similar to the Tata Indicom
site except for the URL being different. (In some Phishing
cases, URL is also made to look similar to the real URL by
inserting an image)
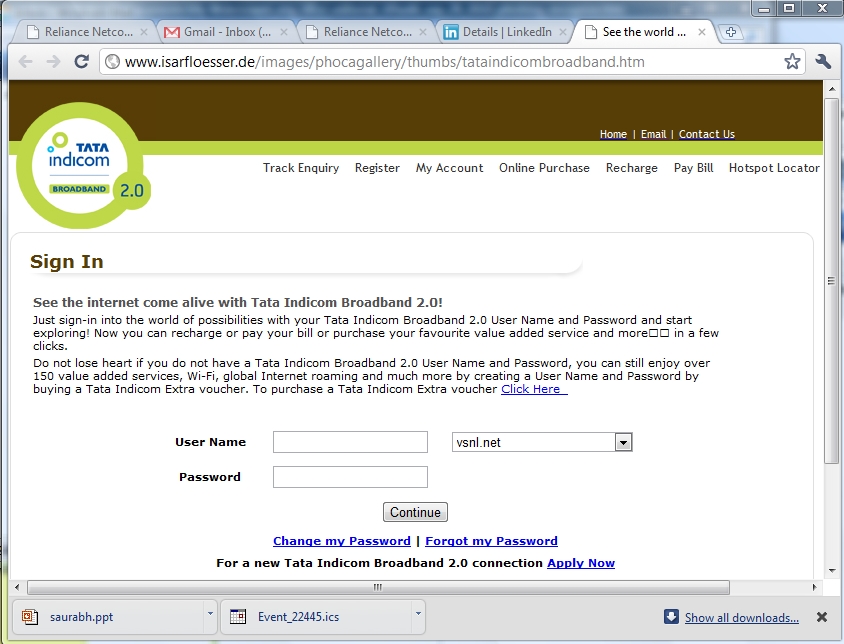
One can see that this page has the user name
and password and if this is entered, then it will reach the
hands of the fraudsters.
Once the password is entered, and "continue"
button is pressed, the next screen will again show the same
looking page this time from the genuine site as shown below.
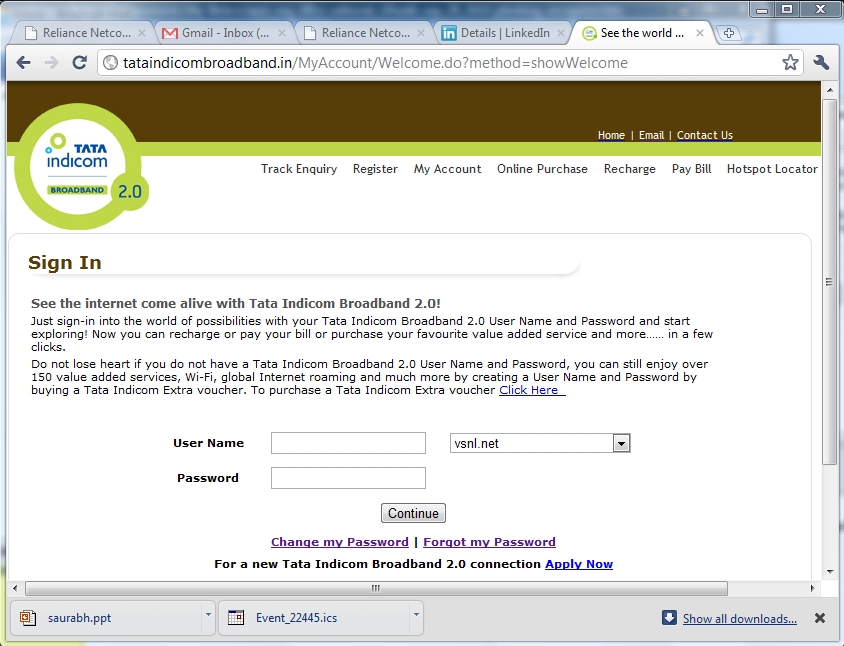
The user would naturally assume that there
was some error and re enter the information once again, go to
his genuine account panel and would never doubt that his
password has already been picked by deceit by the Phisher.
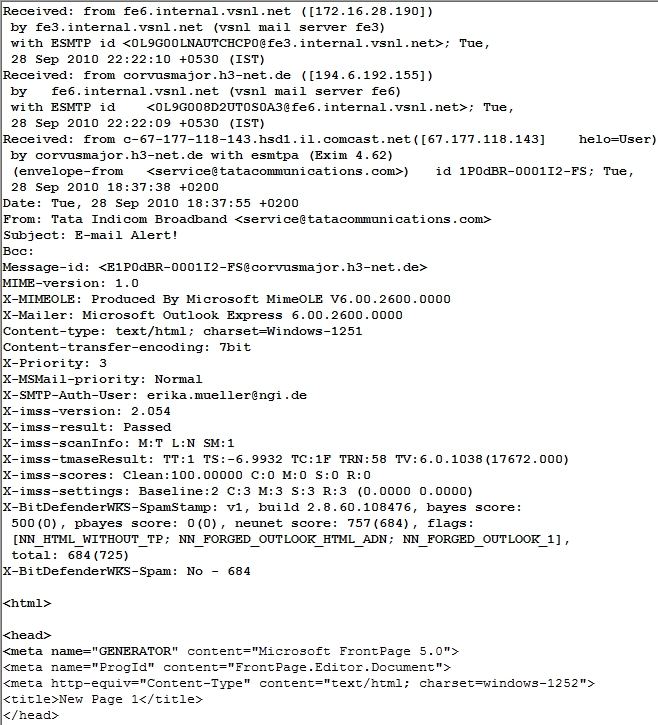
The next check is to check the header
information in the mail. The process of opening the header may
vary with the e-mail client one uses. In Google or Yahoo it may
be available under "Show Details" etc and the user has to find
out how to open the header.
The header information of the above e-mail
looked like this-
If you could read the meaning into the
header, one can recognize that the mail originated from an IP
address 67.117.118.143.
This IP address is actually registered to a
Customer by name LeslieJosephDds, 268, Bush St, San Fransisco,
through the service provider ATT Internet services.
(See details)
The domain name isarfloesser.de itself is
registered in the name of Franz Bernack with address Domberg 16,
85354, Freising, Germany.
(See details)
In case Tata Indicom is aware of the
existence of this e-mail, it is duty bound to take reasonable
steps as an "Intermediary" to initiate action against the person
who pima facie appears to have sent the mail as well as the
domain name owner of the domain
http://www.isarfloesser.de/images/phocagallery/thumbs/tataindicombroadband.htm
This is being provided for the general
information of
Netizens.
In my next article, I will also provide a
suggestion on what can the Netizen do in case he gets such an
e-mail.
Naavi
Sept 29 2010


