We had discussed in the previous articles that Information Security adoption by individual employees may be mapped to five motivational parameters namely,
1. Awareness, 2. Acceptance 3. Availability, 4. Mandate and 5. Inspiration.
Unlike the normal motivational models, the model suggested for visualization of this process for better understanding was a “Pentagon” where each of the five factors were considered the sides that bind the IS adoption process. This was different from the Maslow’s pyramid/triangle model or any other forms of sequential adoption of different factors.
In the current article, I add a few more thoughts on how we can build a measurement system where a Company’s level of achievement in Information Security capability can be mapped against a model similar to the quality CMM modelling system. This would be relevant for the purpose of auditing of the level of IS achievement. Under this model, each of the five motivational factors are mapped against the level of achievement in a matrix as shown in the following picture.
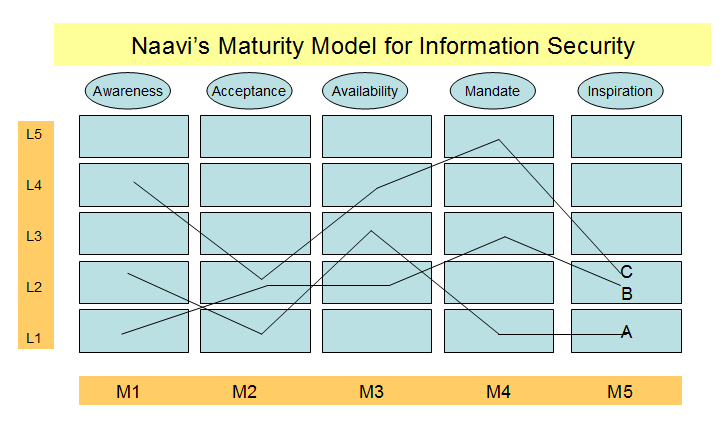
For example, the IS capability of a Company A may be depicted as a matrix element such as M1L2,M2L1,M3L3,M4L1,M5L1. Company B is mapped as M1L1,M2L2,M3L2,M4L3,M5L2. Company C is mapped as M1L4,M2L2,M3L4,M4L5,M5L2.
It may be observed that unlike the CMM model where the maturity is recognized on a stacking basis that Level 2 is after level 1 Level 3 is after Level 2 etc, the Maturity Model for IS is suggested as a concurrent measurement over different motivational parameters with a possiblity that a company may attain a higher maturity level in one parameter while maintaining a lower maturity level in some other parameter.
This system of recording different maturity capabilities in different maturity parameters recognizes that, IS capability is dependent on human beings and hence the achievement of capability is not entirely in the hands of the Company alone. While the Company may invest in best security tools, create 100% awareness or even mandate the IS practices, it has no control on two other parameters such as “Acceptance” and “Inspiration”. These are dependent on the employees. Hence it may not be possible for a company to reach say L5 in all parameters simultaneously even after it exhausts all resources under its capability.
It is possible that the complex looking matrix notation M1L2 ..etc can be replaced with a score on a base of 100 or in any other manner. This may be done either with equal weightage on all the five parameters or with higher parameters for “Acceptance” and “Inspiration”. The placement of any achievement in a particular level L1 to L5 may be calculated on the basis of an estimated percentage achievement in different parameters. It may also be required to develop certain behavioural exercises to determine the achieved level of “Acceptance”. These are for the follow up discussion.
Still it is recognized that there is scope for some subjectivity, lack of repeatability or other deficiencies in the proposed approach. However, one may also debate if this model needs to exactly match the current CMM models or whether it may stand on its own evaluation parameters which are distinct.
At this point of time, the above model is introduced for further discussion. I do have some thoughts on how the different levels of achievement of each motivational parameters which will be presented in subsequent articles. I invite other IS practitioners to present their views so that this model can be refined further.
P.S: This article refers to the following three of my earlier articles which provide the background.
1. Techno Legal Behavioural Science Approach to Information Security
2. What motivates an individual to adopt Security
3. Theory of Motivation based on Behavioural Science Approach
Those who have not browsed through these articles may peruse the same.

