The National ID Card Challenge for Nandan Nilekani.. Part II
[This is part II of the series.
Part I is available here]
One of the important principles suggested for the
National ID Card scheme in the previous part (ZeMo Card system) is to de-link
subject data from the ID device. For this purpose the data required to be
associated with a person is divided into three categories. (or more as
required). The first category of data is the data related to the ID of the
holder. Part of this is visible on the card itself. The second category is
related to the security of the ID. Part of this is embedded in the card in
a machine only readable manner. Part of the security data along with the
main data linked to the subject is held in a remote server which is
accessible with the use of the ID data and the access data.
The physical appearance of a sample of such a card
would be as follows:
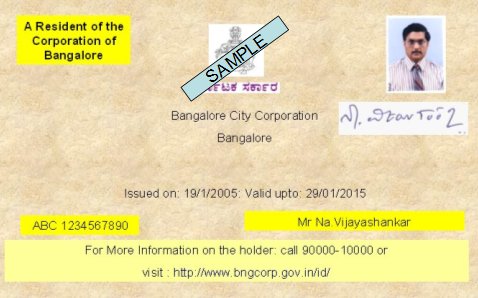
(A Sample ID Card under the ZeMo system)
The basic version which is depicted above does not have
any memory. It however has a serial number which is the Unique ID attached
to the holder. The unique ID can also be etched or represented through a
bar code in such a manner that it cannot be tampered with. The card also
contains a printing of the signature of the person.
For the unique national ID card, a low memory smart card
may be used instead of the memory less card so that the digital thumb print
of the person can be recorded. The resident memory is used only for
recording the ID data such as the thumb print and no other data. This has
to be supplemented with an option to register a "Password" by the
user. Passwords may not be suitable as a mandatory provision for the NIDC
since a majority of users would be illiterate. The biggest challenge of
course is how to make the embedded electronic information tamper proof. It
may be necessary to use some special printing technology and multi factor
authentication data to prevent possible cloning of a card with modified
personal ID. It is also possible to use cards with embedded RFID tags.
(More details of what would be appropriate as Security is an issue which is
beyond the scope of this note.)
The
de-linking of the information from the ID has its own advantages.
The first
and foremost advantage is that the database can be under the control of the
authority and can be updated without the need for the card holder to
present the card for modification.
In the
sample card indicated above an expiry date is provided for as a means of
abundant caution so that the holder can be made to visit an authorized
center with a new photograph and signature to be recorded at least once in
10 years. This is a policy decision for the Government to consider.
The
common frequent occurrences when the database is to be modified such as
change updation of health records, updation of qualifications, updation of
credit information, updation of employment details etc can be made with
suitable documents from intermediary agencies such as the Hospitals,
Colleges, Banks, Employers etc without the need for the card holder to
personally submit the information. Any such modifications reflect at all
access points when the data is queried based on the ID tag attached to the
card.
The ease
of updation of database by the authority without the need for the card
holder’s consent or intervention is not available in the case of Smart
Cards. The smart card data can be modified only when the card holder
presents the card at one of the data writing centers. If the modification
is not done on the card, the holder will be walking around with a card
which does not correspond to the current information and therefore defeats
the very purpose of issuing of the card.
One more
significant advantage in the ZeMo system is that the primary database can
be created modularly and seamlessly integrated with the system.
Operationally this would mean that after creating the primary data say from
the PDS system, the health data base can simply be added. Further, the
financial database can be integrated. Operationally therefore the ZeMo
cards provides the flexibility of being expanded modularly. The smart cards
do not have such flexibility since the cards have to be re-written if any
change is made in the data base.
Hacking Risk Mitigation:
In both
the ZeMo based system as well as the Smart Card based system there has to
be a central database and it is susceptible for unauthorized access. In the
case of ZeMo based system it is envisaged that a “Synchronized Proxy” would
have access to public through open networks. This access would be to a part
of the database elements which contains the non critical public data of
the person. This will be susceptible to a higher level of hacking risk.
However since this is separated from the centralized database the risk to
the critical data is not different from the Smart Card based system.
In the
Smart Card based system the card itself contains the data both critical and
non critical. It is also envisaged that in many access points the card data
alone will be relied upon without cross reference to the original data.
This is advantageous from the point of view of instant access to the
information as against the connectivity dependent access of the ZeMo based
system. However a “Non reliable Data Access” is a greater risk since it
does not serve the purpose of the card.
It must
be recognized that the Smart Card would be in the hands of the user which
means that the data attached to the Card is in the hands of the public. It
is therefore susceptible for modification through use of any technology at
any point in India or outside.
Smart
Cards are prone to “Floating Information Risk” where manipulated data is
never available to authorities for verification and will be floating until
a major scam surfaces. This is the typical type of risk that surfaced in
the forged stamp paper scam with thousands of crores of rupees worth stamps
being in the hands of unregistered stamp papers in the hands of the public.
Also the
Smart Cards can be duplicated and not withstanding the hidden codes that
can be embedded, the risk of duplication by organized outfits such as
terrorists is a real threat.
As in the
case of Currency duplication and Stamp Paper duplication, Smart Card based
Resident IDs will be easily duplicated in large numbers in border areas to
change demographic configuration or to obtain a false identity. The ability
to check forged smart card data cannot be provided for in all access points
since they may not be by design meant to cross verify with any other
central database system.
It has
also been revealed by M/s Sergei Skorobogatov and Ross Anderson of
Cambridge University that sensitive information stored on a smart card
microprocessor can be revealed with a flash of light using inexpensive, off
the shelf equipments.
It has
been found that firing light from an ordinary camera flash at parts of a
smart card microchip can assist an attacker in determining the sensitive
information stored on the card.
In the semi invasive
attack, the researchers removed part of a chip's protective covering and
then focused the light from an ordinary camera flash using a microscope on
particular parts of a smart card's microprocessor. It was found that this
could reveal the information stored in the card such as for example, the
cryptographic key used to gain access to a building or to secure internet
transactions.
Since the Smart Cards will
be in the possession of the public for extended times, it can be modified
if effort is placed.
On the other hand, the ZeMo
card system does not place faith on the data on the card and it is always
checked with reference to the central database. The only way data can be
manipulated is by hacking the central database server or the intermediary
routers or linking the data of one genuine person to a fake card holder.
All attempts to hack an electronic system leaves a trail with which either
the card can be cancelled or the culprit traced before large scale damage
is done. Manipulations on the card itself need to be secured with
appropriate printing technology safeguards.
The electronic data base
would ordinarily be capable of generating instant alerts for identifying
any security risks as in the case of online credit card validation systems
and once identified, alerts become available at all access points
simultaneously leaving little time for the offender to make profitable use
of the manipulation.
It is therefore considered
that the Central Secure data base management lends itself to better
security than the distributed database represented by the smart cards.
On the other hand the Smart
Cards are to be used only for the purpose of implanting a mechanical ID,
then the RFID cards can achieve this purpose at a lot less cost than the
Smart Cards.
If in some point of time in
the future, “Digital Signatures” need to be embedded into the ID cards,
then only Smart Cards may become useful. However, it is possible to use the
RFID cards also in some manner to invoke digital signatures since some
storage space is available in higher versions of RFID cards.


