"Naavi Pyramid" for Modular
implementation of Total Information Assurance
Information Assurance is an
essential objective of any organization with a stake in IT. In
critical business organizations such as Banks and Health Care
industries, it is imperative that Information Assurance at a
certain minimal level should be considered as a base requirement
for carrying on the business itself.
However, an Information Assurance
program with the 5 components of Confidentiality, Integrity,
Availability, Authenticity and Non repudiation is considered
"expensive" and "Time consuming" for most of the organizations.
For medium and small enterprises, it is almost a non starter
because of the costs would never match the available IT or
Information Security budgets. ISO 27001 or COBIT remain only
dreams in most of the organizations because of the cost factor.
In such a circumstance, what would
be the alternative before a management which would like to keep
the Information risks within manageable limits. In the Banking
industry where an uncovered risk immediately converts itself
into Capital Adequacy erosion through the Basel II norms,
management cannot remain a mute spectator to a growing level of
Information risk without any effective mechanism for control.
Similarly when the RBI guidelines
or the SEBI guidelines applicable for publicly listed banks
mandate information risk control, it is not possible for the
managements of Banks to ignore the compliance requirements and
continue to be in business.
This problem is acute in the case
of smaller Banks including Cooperative Banks or the RRBs where
the IT requirement, usage and risks are similar to any large
bank like an SBI, but it does not have the same financial
strength of the SBI to implement an ISO 27001 program across the
enterprise. Implementing a COBIT framework is even more
difficult for these Banks or even many of the large Banks.
When confronted with a similar
problem in any business challenge managements immediately
consider a "Modular Approach" where the end objective is divided
into several smaller steps and achieved progressively without
need for large investment of time and money.
However so far Information
Security implementation has been considered amenable only for a
"Quantum Approach" to implementation rather than a "Modular
Approach" since it is always considered that "Security is as
strong as the weakest link" and cannot be broken up into parts.
It is like when we are crossing a 10 ft wide pit, we cannot make
it in two 5 ft jumps. We either cover the 10 ft in one single
leap or fall into the abyss.
Under such circumstances, it has
been a challenge for Information Assurance professionals to find
a method of implementation on a modular basis but yet meet the
principle of "Security without broken links".
Towards this challenging task,
Naavi's approach to Total Information Assurance using the Naavi
Pyramid model is expected to make a significant contribution.
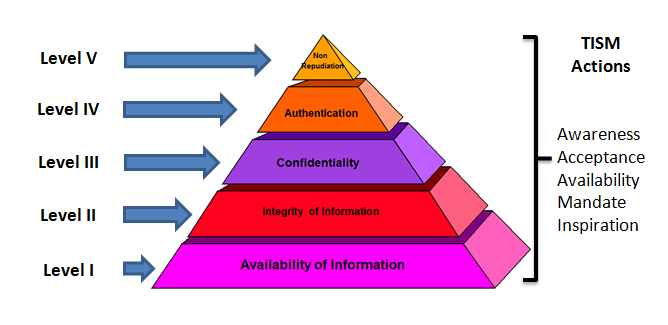
The Naavi pyramid approach is
built on the premise that Total Information Assurance which
satisfies all the 5 elements such as Confidentiality, Integrity,
Availability, Authenticity and Non Repudiation can be achieved
across all the three dimensions of security namely the
Technology, the Law and the Human aspects if we try to re
arrange the objectives in a hierarchy of priorities starting
with Availability at the bottom and growing upto Non Repudiation
in steps covering Integrity, Confidentiality and Authenticity in
that order as depicted in the diagram indicated above.
The Pyramid approach aims to
prioritize the 5 elements in the form of 5 levels. At the first
level, the objective is to achieve a satisfactory level of
"Availability" of information. "Availability" is considered the
"priority" and it does not mean that the organization does not
recognize the aspects of assurance. While achieving the desired
level of fulfillment of the "Availability objective", some of
the other objectives may also be achieved to some extent.
However the budgetary focus would be on achieving
"Availability".
While achieving "Availability" it
would be necessary to complete Information classification,
identify the risks associated with the information, how denial
of access attacks can be prevented, how DRP and BCP can be
effectively implemented. Policy documents for Information
Security as well as Privacy will also have to be drawn though
with a limited scope.
Once the Level I is completed, the
organization can take up additional measures for Level II and so
on until all levels are reached. Once the final level is
attained the assurance implementation should be over and above
the ISO 27001/COBIT level.
Detailed specification list under TIAF4MI at each
level is being
developed by Ujvala Consultants Pvt Ltd for its own
implementation.
The TIAF4MI is therefore a unique and practical approach which
incorporates the best practices inherent in the current IS and
IA practices and is practical in its implementation procedure. increases the acceptability amongst corporate
managers.
Hopefully the industry practitioners will respond positively to this
new approach to Information Security and Information Assurance.
Naavi
23rd Nov 2012

