Maturity Model for Information Security Capability..2
We introduced an approach to building a maturity
model for Information Security Capability in our previous article. This
article will provide a background to bring a larger section of the
readers of Naavi.org into the debate and also fill up some of the
gaps left uncovered in the previous article so that experts can start
adding their thoughts.
We have been discussing that Techno Legal
Information Security is a top management requirement in today's
information led business world. We have also been emphasizing that ITA
2008 has the effect of mandating Information Security and therefore
companies need to implement a ITA 2008 compliance programme before the
Clause 49 certification is due for the current financial year. We have
also brought in the element of "Behavioural Science" to the domain of
Information Security presenting a "Theory of Information Security
Motivation" identifying the motivational factors that determine the
successful implementation of IS practices in a company.
Now, under the the Maturity Model for Information
Security Capability (shall we call it IS-CMM ?.. so that we can
appreciate the relationship of this approach with the better known CMMI
or SEI CMM terms used in software industry) we are exploring the
methods for measuring the IS capability of an organization. Ideally this
article should have appeared before the article that appeared on 6th but
we shall try to merge some of the essential parts of the earlier article
into this so that it will become a more comprehensive article.
Software industry has successfully introduced the
concept of different levels of maturity in software development process
adopted by an organization to supplement its people and technology
resources. This People-Process-Technology combination is the foundation on
which a good software development company is built. The process capability
is measured on a five level tiered basis so that a CMM Level 5 company is
considered to have processes that have reached an optimization level in its
software development process.
Level 1 is considered the initial start point for a
company where there may be no processes. At this initial level, results of any project
may depend totally on the manager’s personal approach and the programmers’
experience, meaning the success of a particular project can be repeated
only if the same managers and programmers are assigned to the next project.
A Company is recognized to have graduated to Level 2
when project management technologies have been introduced in the
company based on accumulated
experience and there are standards for produced software which
are documented. This enables the process to become "repeatable" without
the dependency on the same set of people.
A Company graduates to Level 3 when
standards for the processes of software development and maintenance are
introduced and documented (including project management), There is a special quality management department for building and
maintaining these standards. The degree of organizational dependence on the qualities of
particular developers decreases and the process does not tend to roll
back to the previous level in critical situations.
Level 4 is referred to as the "Managed Level" where there
are quantitative indices (for both software and process as a whole)
established in the organization. Better project management is achieved
due to the decrease of digression in different project indices. However,
sensible variations in process efficiency may be different from random
variations (noise), especially in mastered areas.
When the company reaches Level 5, improvement
procedures are carried out not only for existing processes, but also for
evaluation of the efficiency of newly introduced innovative technologies.
The main goal of an organization on this level is permanent improvement
of existing processes. This should anticipate possible errors and defects
and decrease the costs of software development, by creating reusable
components for example.
Though the CMM does not by itself guarantee that a
"Good" software would be developed, nor it is meant to provide such a
guarantee, the Certification of a Software Company under the CMM
methodology has come to be considered an index of a Company's
capability.
Naavi has always been of the opinion that "There is No
Quality without Security" and hence a quality process approach such as CMM
is expected to also consider that the process should have an inbuilt
"Security". Hence a CMM certification or a Six Sigma Certification ignoring
the Information Security aspects was always considered a faulty/inadequate
certification. However since the focus of CMM certification originated from
the need to strengthen the quality, it was natural that Security
orientation of a quality process can only come in as an "After thought".
It would be dysfunctional to start downgrading a CMM
Level 5 Company if its Information Security process is inadequate, if
unauthorized persons can hack into the company and say steal the source
codes etc. Hence we need to leave the quality certification methodologies
at the current practices though it remains "Quality Sans Security" and find
a parellel concurrent Security certification which grades the Security
Capability of a Company on a different scale.
For example, we may develop a separate metric for
Information Security Achievements such as (for argument) Level 1 of ISO
27001, Level 2 of ISO 27001 etc and evaluate a company from the perspective
of quality of processes on the basis of CMM and Quality of Security on the
basis of ISO (modified). The market may interpret the overall Quality cum
Security standing of the enterprise by looking at both parameters
simultaneously.
What the author is proposing under IS CMM is an
Information Security Capability Maturity Model which is aimed to assess the
IS achievements through a combination of People, Process and
Technology.
Just as we say that "There is No Quality Without
Security", it is true that " There is No Security Without Quality". In fact
this is not just a statement born out of the management's intentions or
best practices, it is how the Techno Legal Security System recognizes
Security. The proof is available in the fact that under Section 66 of
Information Technology Act 2000 (ITA 2000) compliance of which is part of
the Techno Legal Information Security System, says that "Diminishing of the
value or Utility of information residing in a computer system" is a Cyber
Crime and if such a crime occurs in a Company the Company may have to bear
a financial liability leading to other adverse consequences affecting even
the BCP. "Quality" process is meant to maintain a certain level of value or
utility of the software. Therefore, when "Quality" is not maintained, the
"Value" of the software may be treated as "Diminished". In order to prevent
occurence of a crime (ie.,preventing the diminishing of value through
negligence in handling the quality process) the Security Process should
ensure that the Quality Process is not diluted.
It is therefore possible for the IS CMM process to
integrate the current CMM process and become an "Integrated Organizational
Capability Maturity Model". Since we have conceded that the existing
CMM process need not be disturbed in the name of "Security", the
alternative possibility of integrating "CMM" as a quality parameter into
the "IS-CMM" needs to be seriously explored. We are addressing such an
approach in this model.
ISO 27001 incorporates "Technology". But its
inclusiveness may be inadequate when it comes to "People". The requirements
of "Policy Documents" under ISO 27001 does address "Process" but its end
objectives may be more focussed on the security domain only and unless
there is a strong bonding with the "Legal Compliance", the "Quality
Process" is not attracted within the ISO framework. Again, like the CMM
model, ISO 27001 has already matured to a certain level and any tinkering
of its process would again be creating more problems than it may solve.
For this reason, it is better to find a solution to
grade companies on the basis of their Security Capability outside the ISO
framework. We shall therefore not attempt to find Level I, II, III.. etc
of ISO 27001.
After eliminating the current CMM and ISO frameworks as
solutions for creating an evaluation and gradation system for a "Quality
Cum Security" capability of an organization, a possible solution appears to
be available with the Three Dimensional Information Security approach which
the author has presented earlier.
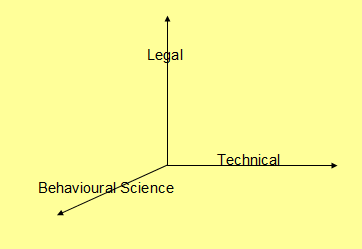
In the Three dimensional theory of Information Security
discussed earlier by this author, The Technical and Legal dimensions of
Information Security was further augmented by the Behavioural Science
dimension.
The hypothesis is that the way people behave to
different stimuli is an important factor to be considered for IS
implementation both for risk assessment and for mitigation strategies.
The three dimensional model was supplemented by the
"Theory of Information Security Motivation" (TISM) under which it was
considered that the Information Security Motivation may be visualized as a
"Pentagon
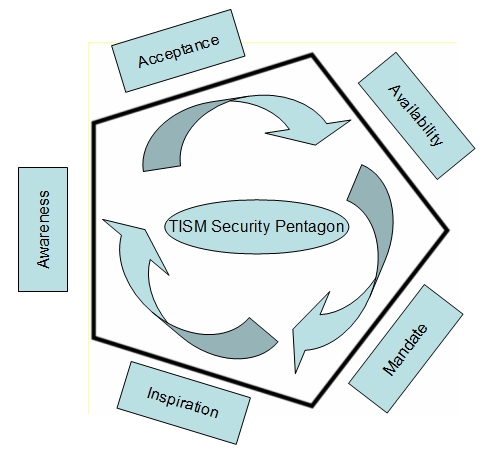
Model" where it was suggested that Information
Security adoption by individual employees may be mapped to five
motivational parameters namely,
1. Awareness, 2. Acceptance 3. Availability, 4.
Mandate and 5. Inspiration.
Unlike the normal motivational models, the model
suggested for visualization of this process for better understanding was
a “Pentagon” where each of the five factors were considered the sides
that bind the IS adoption process. This was different from the Maslow’s
pyramid/triangle model or any other forms of sequential adoption
of different factors
Out of the, five IS motivational factors considered
above, Awareness, Acceptance and Inspiration are related to
"People". "Availability" is related to "Technology". "Mandate" is related
to "Process". Hence, Naavi's Theory of Information Security Motivation (TISM)
already integrates the three important aspects of Corporate performance
namely "People", Process" and "Technology". If we build an IS-CMM model
based on the evaluation of Security Capability on the basis of TISM, we
will perhaps be creating a satisfactory model of evaluation of Corporate
performance.
With this background let us now look at a suggested
Maturity Model for Information Security as shown below.
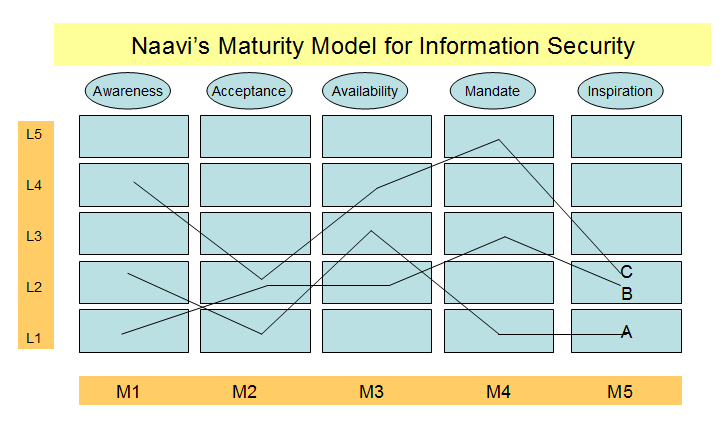
In this model the five motivational factors have not
been combined but held independently. Also in order to differentiate the
levels of capability, instead of adopting a level across different
motivational parameters, a matrix type depiction is presented.
i.e., instead of saying that Company A is in IS CMM
Level I, Comany B is in IS CMM Level II and Company C is in IS CMM Level
III, the following matrix notation is used.
Under this notation, Company A may
be depicted as a matrix element such as M1L2,M2L1,M3L3,M4L1,M5L1. Company
B is mapped as M1L1,M2L2,M3L2,M4L3,M5L2. Company C is mapped as
M1L4,M2L2,M3L4,M4L5,M5L2. [Alternatively, the notation can be IS CMM-L
(2.1.3.1.1)], etc
This system of recording different maturity
capabilities in different maturity parameters recognizes that, IS
capability is dependent on human beings and hence the achievement of
capability is not entirely in the hands of the Company alone. While the
Company may invest in best security tools, create 100% awareness or even
mandate the IS practices, it has no control on two other parameters such
as “Acceptance” and “Inspiration”. These are dependent on the employees.
Hence it may not be possible for a company to reach say L5 in all
parameters simultaneously even after it exhausts all resources under its
capability.
However, if the matrix notation is considered too
complicated for practical utility, it is suggested that it can be reduced
to a "Rating Notation" For this purpose, the matrix elements may be
first reduced to a "Score" on a scale of 100. Then, the Company is
further evaluated on the following basis.
1. Current Status of IS Capability Score (represented by
a score 0 to 100 divided into five grades A, B, C, D and E)
2. Estimated Capability to retain or improve the
current status in the medium term with known business parameters,
(represented by one of the letters A to E indicating the level to which
it may tend in the medium term)
3.Estimated Capability to retain or improve the
current status in the long term even when the current known business
parameters may undergo a change.(represented by one of the letters A to E
indicating the level to which it may tend in the medium term)
Under this notation, the examples of how a IS
Capability Score may be presented by the Company would be AAA, BAA, CBA, EBB, DBA, etc
I invite comments and suggestions on the above.
P.S: This article refers to the following Four of my
earlier articles which provide the background.
1. Techno
Legal Behavioural Science Approach to Information Security
2. What
motivates an individual to adopt Security
3. Theory
of Motivation based on Behavioural Science Approach
4.
IS Maturity Capability Model
Those who have not browsed through these articles may
peruse the same.
Naavi
February 8, 2010
Comments are Welcome at
naavi@vsnl.com


